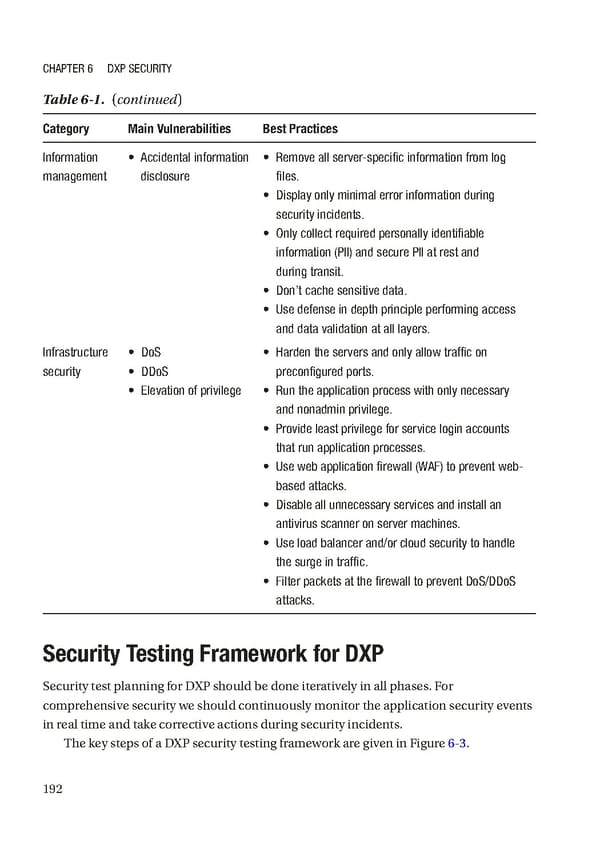
Chapter 6 DXp SeCurity Table 6-1. (continued) Category Main Vulnerabilities Best Practices information • accidental information • remove all server-specific information from log management disclosure files. • Display only minimal error information during security incidents. • Only collect required personally identifiable information (pii) and secure pii at rest and during transit. • Don’t cache sensitive data. • use defense in depth principle performing access and data validation at all layers. infrastructure • DoS • harden the servers and only allow traffic on security • DDoS preconfigured ports. • elevation of privilege • run the application process with only necessary and nonadmin privilege. • provide least privilege for service login accounts that run application processes. • use web application firewall (WaF) to prevent web- based attacks. • Disable all unnecessary services and install an antivirus scanner on server machines. • use load balancer and/or cloud security to handle the surge in traffic. • Filter packets at the firewall to prevent DoS/DDoS attacks. Security Testing Framework for DXP Security test planning for DXP should be done iteratively in all phases. For comprehensive security we should continuously monitor the application security events in real time and take corrective actions during security incidents. The key steps of a DXP security testing framework are given in Figure 6-3. 192
 Building Digital Experience Platforms Page 206 Page 208
Building Digital Experience Platforms Page 206 Page 208