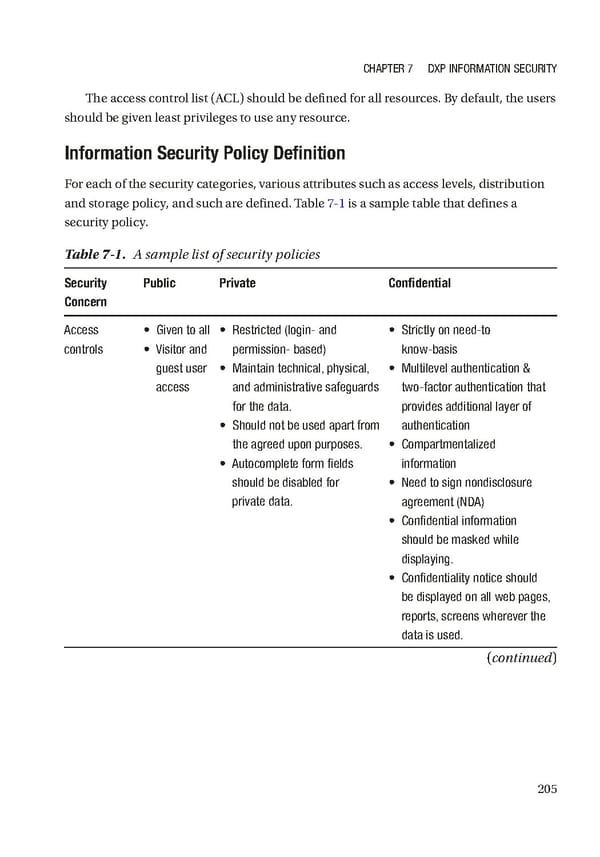
Chapter 7 DXp InformatIon SeCurIty The access control list (ACL) should be defined for all resources. By default, the users should be given least privileges to use any resource. Information Security Policy Definition For each of the security categories, various attributes such as access levels, distribution and storage policy, and such are defined. Table 7-1 is a sample table that defines a security policy. Table 7-1. A sample list of security policies Security Public Private Confidential Concern access • Given to all • restricted (login- and • Strictly on need-to controls • Visitor and permission- based) know- basis guest user • maintain technical, physical, • multilevel authentication & access and administrative safeguards two-factor authentication that for the data. provides additional layer of • Should not be used apart from authentication the agreed upon purposes. • Compartmentalized • autocomplete form fields information should be disabled for • need to sign nondisclosure private data. agreement (nDa) • Confidential information should be masked while displaying. • Confidentiality notice should be displayed on all web pages, reports, screens wherever the data is used. (continued) 205
 Building Digital Experience Platforms Page 219 Page 221
Building Digital Experience Platforms Page 219 Page 221