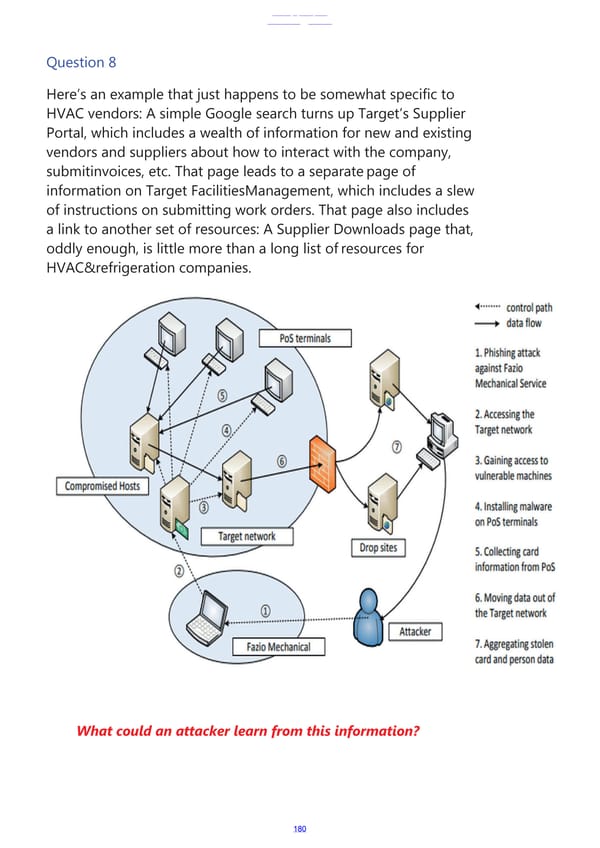
Question 8 Here’s an example that just happens to be somewhat specific to HVAC vendors: A simple Google search turns up Target’s Supplier Portal, which includes a wealth of information for new and existing vendors and suppliers about how to interact with the company, submitinvoices, etc. That page leads to a separatepage of information on Target FacilitiesManagement, which includes a slew of instructions on submitting work orders. That page also includes a link to another set of resources: A Supplier Downloads page that, oddly enough, is little more than a long list ofresources for HVAC&refrigeration companies. 00 • · • ••·· rnntrnl ri.1rh .,,..,....---- -----.. data flow / lnals 1. Phishin9 iltt-ack d~dill>l Fdl.KJ ! I • Mechanic.ii Service i ~ J.. Accesstng the ' / ,.,.,./ Target network 3. Gainine, access to vulnerable milchincs Compromised Ho _.- ----::i;;}--- · -·~ 4. lnsulling matw.are UII Pus L~rmilldl.) 5. Collecting card 1nformat1on from PoS G. Moving data out of the Target network 7. Aggregating stolen r.:m1 ;:mtt pPr<;nn rfat..1 What could an attacker learn from this information? 180
 Military English. Learning by Doing. Book Page 29 Page 31
Military English. Learning by Doing. Book Page 29 Page 31