Global Risks Report 2023
The world faces a set of risks that feel both wholly new and eerily familiar. The Global Risks Report 2023 explores some of the most severe risks we may face over the next decade. As we stand on the edge of a low-growth and low-cooperation era, tougher trade-offs risk eroding climate action, human development and future resilience.
The Global Risks Report 2023 18th Edition INSIGHT REPORT In partnership with Marsh McLennan and Zurich Insurance Group
January 2023 Global Risks Report 2023 Terms of use and disclaimer This document is published by the World Economic Forum as a contribution to a project, insight area or interaction. The 昀椀ndings, interpretations and conclusions expressed herein are a result of a collaborative process facilitated and endorsed by the World Economic Forum but whose results do not necessarily represent the views of the World Economic Forum, nor the entirety of its Members, Partners or other stakeholders. World Economic Forum All rights reserved. No part of this publication may 91-93 route de la Capite be reproduced, stored in a retrieval system, or CH-1223 Cologny/Geneva transmitted, in any form or by any means, electronic, Switzerland mechanical, photocopying, or otherwise without the Tel.: +41 (0)22 869 1212 prior permission of the World Economic Forum. Fax: +41 (0)22 786 2744 E-mail: [email protected] ISBN-13: 978-2-940631-36-0 www.weforum.org The report and an interactive data platform are Copyright © 2023 available at https://www.weforum.org/reports/global- by the World Economic Forum risks-report-2023/. Global Risks Report 2023 2
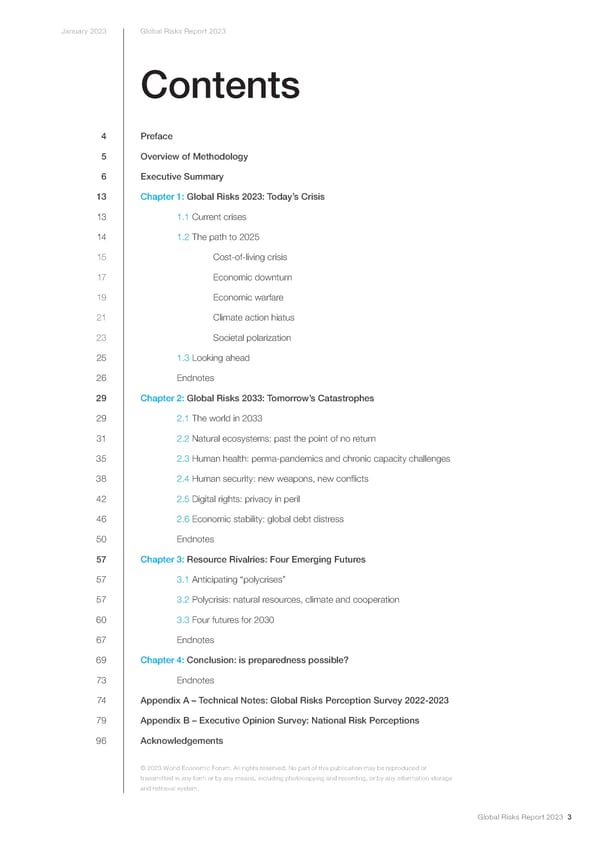
January 2023 Global Risks Report 2023 Contents 4 Preface 5 Overview of Methodology 6 Executive Summary 13 Chapter 1: Global Risks 2023: Today’s Crisis 13 1.1 Current crises 14 1.2 The path to 2025 15 Cost-of-living crisis 17 Economic downturn 19 Economic warfare 21 Climate action hiatus 23 Societal polarization 25 1.3 Looking ahead 26 Endnotes 29 Chapter 2: Global Risks 2033: Tomorrow’s Catastrophes 29 2.1 The world in 2033 31 2.2 Natural ecosystems: past the point of no return 35 2.3 Human health: perma-pandemics and chronic capacity challenges 38 2.4 Human security: new weapons, new con昀氀icts 42 2.5 Digital rights: privacy in peril 46 2.6 Economic stability: global debt distress 50 Endnotes 57 Chapter 3: Resource Rivalries: Four Emerging Futures 57 3.1 Anticipating “polycrises” 57 3.2 Polycrisis: natural resources, climate and cooperation 60 3.3 Four futures for 2030 67 Endnotes 69 Chapter 4: Conclusion: is preparedness possible? 73 Endnotes 74 Appendix A – Technical Notes: Global Risks Perception Survey 2022-2023 79 Appendix B – Executive Opinion Survey: National Risk Perceptions 96 Acknowledgements © 2023 World Economic Forum. All rights reserved. No part of this publication may be reproduced or transmitted in any form or by any means, including photocopying and recording, or by any information storage and retrieval system. Global Risks Report 2023 3
January 2023 Global Risks Report 2023 Preface Saadia Zahidi Managing Director Last year’s Global Risks Report warned that a Yet much-needed attention and resources are being divergent economic recovery from the COVID-19 diverted from newly emerging or rapidly accelerating pandemic risked deepening divisions at a time risks to natural ecosystems, human health, security, when collaboration was urgently required to address digital rights and economic stability that could looming global challenges. Yet despite hard-learned become crises and catastrophes in the next decade. lessons around the interdependence of global risks, A low-growth, low-investment and low-cooperation few would have anticipated the extent of instability era further undermines resilience and the ability to that would soon unfold, this time driven by a new war manage future shocks. In recognition of growing in Europe. complexity and uncertainty, the report also explores connections between these risks. The analysis The health and economic aftereffects of the pandemic focuses on a potential "polycrisis", relating to have quickly spiraled into compounding crises. shortages in natural resources such as food, water, Carbon emissions have climbed, as the post- and metals and minerals, illustrating the associated pandemic global economy 昀椀red back up. Food and socioeconomic and environmental fall-out through a energy have become weaponized by the war in set of potential futures. Ukraine, sending in昀氀ation soaring to levels not seen in decades, globalizing a cost-of-living crisis and fueling The report is underpinned by our annual Global social unrest. The resulting shift in monetary policy Risks Perception Survey, which brings together marks the end of an economic era de昀椀ned by easy leading insights from over 1,200 experts across the access to cheap debt and will have vast rami昀椀cations World Economic Forum’s diverse network. It draws for governments, companies and individuals, widening on the collective intelligence of the world’s foremost inequality within and between countries. risk experts, including the Global Risks Advisory Board and the Chief Risk Of昀椀cers Community, as As the con昀氀ict between Russia and Ukraine well as thematic experts from academia, business, approaches one year, economies and societies government, the international community and will not easily rebound from continued shocks. In civil society. The report has also bene昀椀ted greatly this year’s Global Risks Perception Survey, more from the expertise of the World Economic Forum’s than four in 昀椀ve respondents anticipated consistent platforms, which work daily to drive tangible, volatility over the next two years. The persistence system-positive change for the long term. We are of these crises is already reshaping the world that deeply grateful to our long-standing partners in the we live in, ushering in economic and technological report’s development: Marsh McLennan and Zurich fragmentation. A continued push for national resilience Insurance Group. in strategic sectors will come at a cost – one that only a few economies can bear. Geopolitical dynamics The 2023 edition of the Global Risks Report are also creating signi昀椀cant headwinds for global highlights the multiple areas where the world is cooperation, which often acts as a guardrail to these at a critical in昀氀ection point. It is a call to action, to global risks. collectively prepare for the next crisis the world may face and, in doing so, shape a pathway to a more The 18th edition of the Global Risks Report considers stable, resilient world. this backdrop of simmering geopolitical tensions and con昀氀uence of socioeconomic risks. It identi昀椀es the most severe perceived risks to economies and societies over the next two years. The world's collective focus is being channeled into the “survival” of today’s crises: cost of living, social and political polarization, food and energy supplies, tepid growth, and geopolitical confrontation, among others. Global Risks Report 2023 4
January 2023 Global Risks Report 2023 Overview of methodology The Global Risks Perception Survey (GRPS) has Refer to Appendix A: Technical Notes: Global underpinned the Global Risks Report for nearly two Risks Perception Survey 2022-2023 for more decades and is the World Economic Forum’s premier detail, including relevant de昀椀nitions for each of the 32 source of original global risks data. This year’s global risks. GRPS has brought together leading insights on the evolving global risks landscape from over 1,200 To complement GRPS data on global risks, the experts across academia, business, government, the report also draws on the World Economic Forum’s international community and civil society. Responses Executive Opinion Survey (EOS) to identify risks for the GRPS 2022-2023 were collected from 7 that pose the most severe threat to each country September to 5 October 2022. over the next two years, as identi昀椀ed by over 12,000 business leaders in 121 economies. When “Global risk” is de昀椀ned as the possibility of the considered in context with the GRPS, this data occurrence of an event or condition which, if it provides insight into local concerns and priorities occurs, would negatively impact a signi昀椀cant and points to potential “hot spots” and regional proportion of global GDP, population or natural manifestations of global risks. Refer to Appendix resources. The GRPS 2022-2023 included the B: Executive Opinion Survey: National Risk following components: Perceptions for more detail. • Outlook invited respondents to predict global Finally, the report integrates the views of leading volatility to provide context to the evolution of the experts to generate foresight and to support global risks landscape. analysis of the survey data. The Global Risks Report harnesses contributions from over 40 colleagues • Severity assessed the perceived likely impact across the World Economic Forum’s platforms. of global risks over a one-, two- and 10-year Qualitative insights were also collected from over horizon, to illustrate the potential development of 50 experts from across academia, business, individual global risks over time. government, the international community and civil society through community meetings, private • Consequences asked respondents to consider interviews and thematic workshops conducted from potential impacts of a risk arising, to highlight July to November 2022. These include the Global relationships between global risks and the Risks Advisory Board and the Chief Risks Of昀椀cers potential for compounding crises. Community. Refer to Contributors for more detail. • Risk preparedness and governance invited respondents to assess the current effectiveness of the management of global risks and re昀氀ect on which stakeholders are best placed to effectively manage them, to elicit opportunities for global action and collaboration. • Qualitative questions on risks sourced expert knowledge to identify new and emerging risks. Global Risks Report 2023 5
January 2023 Global Risks Report 2023 Executive Summary The 昀椀rst years of this decade have heralded a development after decades of progress, rapid and particularly disruptive period in human history. The unconstrained development of dual-use (civilian and return to a “new normal” following the COVID-19 military) technologies, and the growing pressure of pandemic was quickly disrupted by the outbreak of climate change impacts and ambitions in an ever- war in Ukraine, ushering in a fresh series of crises in shrinking window for transition to a 1.5°C world. food and energy – triggering problems that decades Together, these are converging to shape a unique, of progress had sought to solve. uncertain and turbulent decade to come. As 2023 begins, the world is facing a set of risks The Global Risks Report 2023 presents the results that feel both wholly new and eerily familiar. We have of the latest Global Risks Perception Survey (GRPS). seen a return of “older” risks – in昀氀ation, cost-of-living We use three time frames for understanding global crises, trade wars, capital out昀氀ows from emerging risks. Chapter 1 considers the mounting impact of markets, widespread social unrest, geopolitical current crises (i.e. global risks which are already confrontation and the spectre of nuclear warfare – unfolding) on the most severe global risks that many which few of this generation’s business leaders and expect to play out over the short term (two years). public policy-makers have experienced. These are Chapter 2 considers a selection of risks that are being ampli昀椀ed by comparatively new developments likely to be most severe in the long term (10 years), in the global risks landscape, including unsustainable exploring newly emerging or rapidly accelerating levels of debt, a new era of low growth, low global economic, environmental, societal, geopolitical and investment and de-globalization, a decline in human technological risks that could become tomorrow’s FIGURE A Global risks ranked by severity over the short and long term "Please estimate the likely impact (severity) of the following risks over a 2-year and 10-year period" 2 years 10 years 1 Cost-of-living crisis 1 Failure to mitigate climate change 2 Natural disasters and extreme weather 2 Failure of climate-change adaptation events 3 Geoeconomic confrontation 3 Natural disasters and extreme weather events 4 Failure to mitigate climate change 4 Biodiversity loss and ecosystem collapse 5 Erosion of social cohesion and societal 5 Large-scale involuntary migration polarization 6 Large-scale environmental damage 6 Natural resource crises incidents 7 Failure of climate change adaptation 7 Erosion of social cohesion and societal polarization 8 Widespread cybercrime and cyber insecurity 8 Widespread cybercrime and cyber insecurity 9 Natural resource crises 9 Geoeconomic confrontation 10 Large-scale involuntary migration 10 Large-scale environmental damage incidents Risk categories Economic Environmental Geopolitical Societal Technological Source World Economic Forum Global Risks Perception Survey 2022-2023. Global Risks Report 2023 6
Governments and central banks could face stubborn in昀氀ationary pressures over the next two years, not least given the potential for a prolonged war in Ukraine, continued bottlenecks from a lingering pandemic, and economic warfare spurring supply chain decoupling. Downside risks to the economic outlook also loom large. A miscalibration between monetary and 昀椀scal policies will raise the likelihood of liquidity shocks, signaling a more prolonged economic downturn and debt distress on a global scale. Continued supply-driven in昀氀ation could lead to stag昀氀ation, the socioeconomic consequences of which could be severe, given an unprecedented interaction with historically high levels of public debt. Global economic fragmentation, geopolitical tensions and rockier restructuring could contribute to widespread debt distress in the next 10 years. Even if some economies experience a softer-than- crises. Chapter 3 imagines mid-term futures, expected economic landing, the end of the low exploring how connections between the emerging interest rate era will have signi昀椀cant rami昀椀cations risks outlined in previous sections may collectively for governments, businesses and individuals. The evolve into a “polycrisis” centred around natural knock-on effects will be felt most acutely by the resource shortages by 2030. The report concludes most vulnerable parts of society and already-fragile by considering perceptions of the comparative state states, contributing to rising poverty, hunger, violent of preparedness for these risks and highlighting protests, political instability and even state collapse. enablers to charting a course to a more resilient Economic pressures will also erode gains made by world. Below are key 昀椀ndings of the report. middle-income households, spurring discontent, political polarization and calls for enhanced social protections in countries across the world. Cost of living dominates global Governments will continue to face a dangerous risks in the next two years while balancing act between protecting a broad swathe of climate action failure dominates their citizens from an elongated cost-of-living crisis without embedding in昀氀ation – and meeting debt the next decade servicing costs as revenues come under pressure from an economic downturn, an increasingly urgent transition to new energy systems, and a less The next decade will be characterized by stable geopolitical environment. The resulting new environmental and societal crises, driven by economic era may be one of growing divergence underlying geopolitical and economic trends. “Cost- between rich and poor countries and the 昀椀rst of-living crisis” is ranked as the most severe global rollback in human development in decades. risk over the next two years, peaking in the short term. “Biodiversity loss and ecosystem collapse” is viewed as one of the fastest deteriorating global Geopolitical fragmentation will drive risks over the next decade, and all six environmental geoeconomic warfare and heighten risks feature in the top 10 risks over the next 10 the risk of multi-domain con昀氀icts years. Nine risks are featured in the top 10 rankings over both the short and the long term, including “Geoeconomic confrontation” and “Erosion Economic warfare is becoming the norm, with of social cohesion and societal polarisation”, increasing clashes between global powers and state alongside two new entrants to the top rankings: intervention in markets over the next two years. “Widespread cybercrime and cyber insecurity” Economic policies will be used defensively, to build and “Large-scale involuntary migration”. self-suf昀椀ciency and sovereignty from rival powers, but also will increasingly be deployed offensively to constrain the rise of others. Intensive geoeconomic As an economic era ends, the weaponization will highlight security vulnerabilities next will bring more risks of posed by trade, 昀椀nancial and technological stagnation, divergence and interdependence between globally integrated economies, risking an escalating cycle of distrust distress and decoupling. As geopolitics trumps economics, a longer-term rise in inef昀椀cient production and rising prices becomes more likely. Geographic hotspots The economic aftereffects of COVID-19 and the war that are critical to the effective functioning of the in Ukraine have ushered in skyrocketing in昀氀ation, a global 昀椀nancial and economic system, in particular in rapid normalization of monetary policies and started the Asia-Paci昀椀c, also pose a growing concern. a low-growth, low-investment era. Global Risks Report 2023 7
Interstate confrontations are anticipated by GRPS respondents to remain largely economic in nature over the next 10 years. However, the recent uptick in military expenditure and proliferation of new technologies to a wider range of actors could drive a global arms race in emerging technologies. The longer-term global risks landscape could be de昀椀ned by multi-domain con昀氀icts and asymmetric warfare, with the targeted deployment of new-tech weaponry on a potentially more destructive scale than seen in recent decades. Transnational arms control mechanisms must quickly adapt to this new security context, to strengthen the shared moral, reputational and political costs that act as a deterrent to accidental and intentional escalation. Technology will exacerbate inequalities while risks from cybersecurity will remain a constant concern The technology sector will be among the central targets of stronger industrial policies and enhanced Climate mitigation and climate state intervention. Spurred by state aid and military adaptation efforts are set up for a expenditure, as well as private investment, research risky trade-off, while nature and development into emerging technologies will continue at pace over the next decade, yielding collapses advancements in AI, quantum computing and biotechnology, among other technologies. For countries that can afford it, these technologies will Climate and environmental risks are the core focus of provide partial solutions to a range of emerging global risks perceptions over the next decade – and crises, from addressing new health threats and a are the risks for which we are seen to be the least crunch in healthcare capacity to scaling food security prepared. The lack of deep, concerted progress on and climate mitigation. For those that cannot, climate targets has exposed the divergence between inequality and divergence will grow. In all economies, what is scienti昀椀cally necessary to achieve net zero these technologies also bring risks, from widening and what is politically feasible. Growing demands misinformation and disinformation to unmanageably on public-and private-sector resources from other rapid churn in both blue- and white-collar jobs. crises will reduce the speed and scale of mitigation efforts over the next two years, alongside insuf昀椀cient However, the rapid development and deployment progress towards the adaptation support required of new technologies, which often comes with for those communities and countries increasingly limited protocols governing their use, poses its affected by the impacts of climate change. own set of risks. The ever-increasing intertwining of technologies with the critical functioning of As current crises diverts resources from risks arising societies is exposing populations to direct domestic over the medium to longer term, the burdens threats, including those that seek to shatter on natural ecosystems will grow given their still societal functioning. Alongside a rise in cybercrime, undervalued role in the global economy and overall attempts to disrupt critical technology-enabled planetary health. Nature loss and climate change resources and services will become more common, are intrinsically interlinked – a failure in one sphere with attacks anticipated against agriculture and will cascade into the other. Without signi昀椀cant policy water, 昀椀nancial systems, public security, transport, change or investment, the interplay between climate energy and domestic, space-based and undersea change impacts, biodiversity loss, food security communication infrastructure. Technological risks and natural resource consumption will accelerate are not solely limited to rogue actors. Sophisticated ecosystem collapse, threaten food supplies and analysis of larger data sets will enable the misuse livelihoods in climate-vulnerable economies, amplify of personal information through legitimate legal the impacts of natural disasters, and limit further mechanisms, weakening individual digital sovereignty progress on climate mitigation. and the right to privacy, even in well-regulated, democratic regimes. Global Risks Report 2023 8
FIGURE B Short- and long-term global outlook "Which of the following best characterizes your outlook for the world over the short-term (2 years) and longer-term (10 years)? 2% 2% 2 years 13% 69% 14% 10 years 20% 34% 26% 11% 9% Progressive tipping points and persistent crises leading to catastrophic outcomes Consistently volatile across economies and industries with multiple shocks accentuating divergent trajectories Slightly volatile with occasional localised surprises Limited volatility with relative stability Renewed stability with a revival of global resilience Source World Economic Forum, Global Risks Perception Survey 2022-2023. Food, fuel and cost crises global shock is shrinking. Over the next 10 years, exacerbate societal vulnerabilities fewer countries will have the 昀椀scal headroom to invest while declining investments in in future growth, green technologies, education, care and health systems. The slow decay of public human development erode future infrastructure and services in both developing and resilience advanced markets may be relatively subtle, but accumulating impacts will be highly corrosive to the strength of human capital and development – a critical Compounding crises are widening their impact across mitigant to other global risks faced. societies, hitting the livelihoods of a far broader section of the population, and destabilizing more economies in the world, than traditionally vulnerable As volatility in multiple domains communities and fragile states. Building on the most grows in parallel, the risk of severe risks expected to impact in 2023 – including polycrises accelerates “Energy supply crisis”, “Rising in昀氀ation” and “Food supply crisis” – a global Cost-of-living crisis is already being felt. Economic impacts have been Concurrent shocks, deeply interconnected risks cushioned by countries that can afford it, but many and eroding resilience are giving rise to the risk of lower-income countries are facing multiple crises: polycrises – where disparate crises interact such debt, climate change and food security. Continued that the overall impact far exceeds the sum of each supply-side pressures risk turning the current cost-of- part. Eroding geopolitical cooperation will have ripple living crisis into a wider humanitarian crisis within the effects across the global risks landscape over the next two years in many import-dependent markets. medium term, including contributing to a potential polycrisis of interrelated environmental, geopolitical Associated social unrest and political instability will and socioeconomic risks relating to the supply of and not be contained to emerging markets, as economic demand for natural resources. pressures continue to hollow out the middle-income bracket. Mounting citizen frustration at losses in The report describes four potential futures centred human development and declining social mobility, around food, water and metals and mineral shortages, together with a widening gap in values and equality, all of which could spark a humanitarian as well as an are posing an existential challenge to political systems ecological crisis – from water wars and famines to around the world. The election of less centrist leaders continued overexploitation of ecological resources as well as political polarization between economic and a slowdown in climate mitigation and adaption. superpowers over the next two years may also reduce Given uncertain relationships between global risks, space further for collective problem-solving, fracturing similar foresight exercises can help anticipate potential alliances and leading to a more volatile dynamic. connections, directing preparedness measures towards minimizing the scale and scope of polycrises With a crunch in public-sector funding and competing before they arise. security concerns, our capacity to absorb the next Global Risks Report 2023 9
In the years to come, as continued, concurrent leveraging the interconnectivity between global crises embed structural changes to the economic risks can broaden the impact of risk mitigation and geopolitical landscape, they accelerate the activities – shoring up resilience in one area can other risks that we face. More than four in 昀椀ve have a multiplier effect on overall preparedness for GRPS respondents anticipate consistent volatility other related risks. As a deteriorating economic over the next two years at a minimum, with multiple outlook brings tougher trade-offs for governments shocks accentuating divergent trajectories. However, facing competing social, environmental and security respondents are generally more optimistic over concerns, investment in resilience must focus on the longer term. Just over one-half of respondents solutions that address multiple risks, such as funding anticipate a negative outlook, and nearly one in 昀椀ve of adaptation measures that come with climate respondents predict limited volatility with relative – and mitigation co-bene昀椀ts, or investment in areas that potentially renewed – stability in the next 10 years. strengthen human capital and development. Indeed, there is still a window to shape a more Some of the risks described in this year’s report are secure future through more effective preparedness. close to a tipping point. This is the moment to act Addressing the erosion of trust in multilateral collectively, decisively and with a long-term lens to processes will enhance our collective ability to shape a pathway to a more positive, inclusive and prevent and respond to emerging cross-border stable world. crises and strengthen the guardrails we have in place to address well-established risks. In addition, FIGURE C Global risks landscape: an interconnections map Use of weaponsUse of weapons of mass destructionof mass destruction Interstate conflictInterstate conflict Adverse outcomesAdverse outcomes of frof frontier technologiesontier technologies Geoeconomic Geoeconomic confrontation confrontation Ineffectiveness of Widespread cybercrime Ineffectiveness of Digital power concentrationDigital power concentration Widespread cybercrime multilateral institutions and cyber insecurity multilateral institutions and cyber insecurity Digital inequalityDigital inequality Terrorist attacks Terrorist attacks Misinformation and Misinformation and disinformation BrBreakdown of criticaleakdown of critical disinformation information infrastructurinformation infrastructuree EnvirEnvironmentalonmental damage incidentsdamage incidents Natural disasters and State collapse Natural disasters and State collapse extreme weather extreme weather FailurFailure to mitigatee to mitigate climate changeclimate change Large-scaleLarge-scale involuntary migrationinvoluntary migration Biodiversity loss andBiodiversity loss and Erosion of social cohesion Erosion of social cohesion ecosystem collapseecosystem collapse Proliferation of illicit Proliferation of illicit Failure of Failure of Natural rNatural resouresourcece economic activity economic activity climate-change SeverSevere mentale mental climate-change crises crises adaption health deteriorationhealth deterioration adaption Collapse of a systemically Infectious diseasesInfectious diseases Chronic health conditions Collapse of a systemically Chronic health conditions important supply chain important supply chain Employment crisesEmployment crises Failure to stabilize price trajectories Collapse or lack of public Failure to stabilize price trajectories Collapse or lack of public infrastructure and services infrastructure and services Debt crises Debt crises Cost-of-living crisis PrProlonged economicolonged economic Cost-of-living crisis downturdownturnn Asset bubble burstAsset bubble burst Nodes Edges Risk influence Relative influence High High Medium Medium Low Low Risk categories Economic Environmental Geopolitical Societal Technological Source World Economic Forum, Global Risks Perception Survey 2022-2023. Global Risks Report 2023 10
FIGURE D Currently manifesting risks “Please rank the top 5 currently manifesting risks in order of how severe you believe their impact will be on a global level in 2023” 1 2 3 4 5 Energy supply crisis Cost-of-living crisis Rising inflation Food supply crisis Cyberattacks on critical infrastructure Source Risk categories Economic Environmental Geopolitical Societal Technological World Economic Forum Global Risks Perception Survey 2022-2023. FIGURE E Global risks ranked by severity "Please estimate the likely impact (severity) of the following risks over a 2-year and 10-year period" Short term Long term 1 Cost-of-living crisis 1 Failure to mitigate climate change 2 Natural disasters and extreme weather events 2 Failure of climate-change adaption 3 Geoeconomic confrontation 3 Natural disasters and extreme weather events 4 Failure to mitigate climate change 4 Biodiversity loss and ecosystem collapse 5 Erosion of social cohesion and societal polarization 5 Large-scale involuntary migration 6 Large-scale environmental damage incidents 6 Natural resource crises 7 Failure of climate-change adaption 7 Erosion of social cohesion and societal polarization 8 Widespread cybercrime and cyber insecurity 8 Widespread cybercrime and cyber insecurity 9 Natural resource crises 9 Geoeconomic confrontation 10 Large-scale involuntary migration 10 Large-scale environmental damage incidents 11 Debt crises 11 Misinformation and disinformation 12 Failure to stabilize price trajectories 12 Ineffectiveness of multilateral institutions and international cooperation 13 Prolonged economic downturn 13 Interstate conflict 14 Interstate conflict 14 Debt crises 15 Ineffectiveness of multilateral institutions and international cooperation 15 Cost-of-living crisis 16 Misinformation and disinformation 16 Breakdown of critical information infrastructure 17 Collapse of a systemically important industry or supply chain 17 Digital power concentration 18 Biodiversity loss and ecosystem collapse 18 Adverse outcomes of frontier technologies 19 Employment crises 19 Failure to stabilize price trajectories 20 Infectious diseases 20 Chronic diseases and health conditions 21 Use of weapons of mass destruction 21 Prolonged economic downturn 22 Asset bubble bursts 22 State collapse or severe instability 23 Severe mental health deterioration 23 Employment crises 24 Breakdown of critical information infrastructure 24 Collapse of a systemically important industry or supply chain 25 State collapse or severe instability 25 Severe mental health deterioration 26 Chronic diseases and health conditions 26 Collapse or lack of public infrastructure and services 27 Collapse or lack of public infrastructure and services 27 Infectious diseases 28 Proliferation of illicit economic activity 28 Use of weapons of mass destruction 29 Digital power concentration 29 Proliferation of illicit economic activity 30 Terrorist attacks 30 Digital inequality and lack of access to digital services 31 Digital inequality and lack of access to digital services 31 Asset bubble bursts 32 Adverse outcomes of frontier technologies 32 Terrorist attacks Source Risk categories Economic Environmental Geopolitical Societal Technological World Economic Forum Global Risks Perception Survey 2022-2023. Global Risks Report 2023 11
FIGURE F Perceptions around preparedness and governance Risk name Risk preparedness Risk governance Please indicate the current effectiveness of Which set of stakeholders can most effectively risk management, taking into account mechanisms manage the risk? in place to prevent the risk from occurring or prepare to mitigate its impact Terrorist attacks Infectious diseases Breakdown of critical information infrastructure Asset bubble bursts Chronic diseases and health conditions Use of weapons of mass destruction Collapse or lack of public infrastructure and services Prolonged economic downturn Adverse outcomes of frontier technologies Proliferation of illicit economic activity Widespread cybercrime and cyber insecurity Employment crises State collapse or severe instability Digital inequality and lack of access to digital services Collapse of a systemically important industry or supply chain Failure to stabilize price trajectories Debt crises Interstate conflict Ineffectiveness of multilateral institutions and international cooperation Geoeconomic confrontation Digital power concentration Severe mental health deterioration Large-scale environmental damage incidents Cost-of-living crisis Large-scale involuntary migration Erosion of social cohesion and societal polarization Natural disasters and extreme weather events Natural resource crises Biodiversity loss and ecosystem collapse Misinformation and disinformation Failure of climate-change adaption Failure to mitigate climate change 0 25 50 75 100 0 25 50 75 100 Risk category Perception Stakeholder Economic Highly ineffective Local government Environmental Ineffective National government Geopolitical Indeterminate effectiveness Bilateral Societal Highly effective Multi-country Technological Effective Regional International organization Businesses Source Public-Private cooperation World Economic Forum, Global Risks Perception Survey 2022-2023. Global Risks Report 2023 12
January 2023 Global Risks Report 2023 Today's Crisis 1 Global Risks 2023: Today’s Crisis 1.1 Current crises With the global landscape dominated by manifesting that are likely to be most severe in two years, risks, we introduce this year three time frames for and 3) risks that are likely to be most severe in 10 understanding global risks: 1) current crises (i.e. years. This chapter address the outlook for the global risks which are already unfolding), 2) risks 昀椀rst two time frames. Most respondents to the FIGURE 1.1 Currently manifesting risks “Please rank the top 5 currently manifesting risks in order of how severe you believe their impact will be on a global level in 2023” Higher no. of respondents Energy supply crisis Cost-of-living crisis Rising inflation Cyberattacks on critical infrastructure Food supply crisis Disruptions in global supply chains for non-food goods epsondents Weaponization of e of r economic policy Failure to set and meet Shar Debt crisis national net-zero targets Weakening of human rights Continued waves of COVID-19 Structural failures Deployment of nuclear weapons in health systems Deployment of chemical and biological weapons Ranking Higher ranking Risk categories Economic Environmental Geopolitical Societal Technological Source World Economic Forum Global Risks Perception Survey 2022-2023. Global Risks Report 2023 13
2022-2023 Global Risks Perception Survey (GRPS) geopolitical dynamics – with the diffusion of power chose “Energy supply crisis”; “Cost-of-living across countries of differing political and economic crisis”; “Rising in昀氀ation”; “Food supply crisis” systems – are coinciding with a more rapidly and “Cyberattacks on critical infrastructure” changing economic landscape, ushering in a low- as among the top risks for 2023 with the greatest growth, low-investment and low-cooperation era potential impact on a global scale (Figure 1.1). and a potential decline in human development after Those that are outside the top 5 for the year but decades of progress. remain concerns include: failure to meet net- zero targets; weaponization of economic policy; The result is a global risks landscape that feels both weakening of human rights; a debt crisis; and failure wholly new and eerily familiar. There is a return of of non-food supply chains. “older” risks that are understood historically but experienced by few in the current generations News headlines all over the world make these of business leaders and public policy-makers. In results largely unsurprising. Yet their implications addition, there are relatively new developments are profound. Our global “new normal” is a return in the global risk landscape. These include to basics – food, energy, security – problems our widespread, historically high levels of public and globalized world was thought to be on a trajectory in some cases private-sector debt; the ever more to solve. These risks are being ampli昀椀ed by the rapid pace of technological development and persistent health and economic overhang of a its unprecedented intertwining with the critical global pandemic; a war in Europe and sanctions functioning of societies; and the growing pressure that impact a globally integrated economy; and an of climate change impacts and ambitions in an ever- escalating technological arms race underpinned shorter time frame for transition. Together, these by industrial competition and enhanced state are converging to shape a unique, uncertain and intervention. Longer-term structural changes to turbulent 2020s. 1.2 The path to 2025 The complex and rapid evolution of the global risks There were some notable differences between the landscape is adding to a sense of unease. More than responses of government and business respondents, four in 昀椀ve GRPS respondents anticipated consistent with “Debt crises”, “Failure to stabilize price volatility over the next two years at a minimum, with trajectories”, “Failure to mitigate climate change” multiple shocks accentuating divergent trajectories and “Failure of climate change adaptation” (Figure 1.10). featuring more prominently for governments, and “Widespread cybercrime and cyber insecurity” and Respondents to the GRPS see the path to 2025 “Large-scale environmental damage incidents” dominated by social and environmental risks, featuring higher for business (Figure 1.3). driven by underlying geopolitical and economic trends (Figure 1.2). The following sections explore the most severe FIGURE 1.2 Global risks ranked by severity over the short term (2 years) 1 Cost-of-living crisis 6 Large-scale environmental damage incidents 2 Natural disasters and extreme weather 7 Failure of climate change adaptation events 3 Geoeconomic confrontation 8 Widespread cybercrime and cyber insecurity 4 Failure to mitigate climate change 9 Natural resource crises 5 Erosion of social cohesion and societal 10 Large-scale involuntary migration polarization Risk categories Economic Environmental Geopolitical Societal Technological Source World Economic Forum Global Risks Perception Survey 2022-2023. Global Risks Report 2023 14
FIGURE 1.3 Severity by stakeholder over the short term (2 years) Government Business 1 Cost-of-living crisis 1 Cost-of-living crisis 2 Natural disasters and extreme weather 2 Natural disasters and extreme weather 3 Failure to mitigate climate change 3 Geoeconomic confrontation 4 Geoeconomic confrontation 4 Widespread cybercrime and cyber insecurity 5 Failure of climate-change adaption 5 Large-scale environmental damage incidents 6 Debt crises 6 Erosion of social cohesion and societal polarization 7 Erosion of social cohesion and societal 7 Failure to mitigate climate change polarization 8 Failure to stabilize price trajectories 8 Natural resource crises 9 Widespread cybercrime and cyber insecurity 9 Debt crises 10 Prolonged economic downturn 10 Failure of climate-change adaption Risk categories Economic Environmental Geopolitical Societal Technological Source World Economic Forum Global Risks Perception Survey 2022-2023. global risks that many expect to play out over the Although global supply chains have partly adapted, next two years, within the context of the mounting with pressures signi昀椀cantly lower than the peak 3 impacts and constraints being imposed by the experienced in April last year, price shocks to core numerous crises felt today. These are: cost-of-living necessities have signi昀椀cantly outpaced general crisis, economic downturn, geoeconomic warfare, in昀氀ation over this time (Figure 1.4). The FAO Price climate action hiatus and societal polarization. We Index hit the highest level since its inception in 1990 4 describe current trends associated with each risk, in March last year. Energy prices are estimated to brie昀氀y cover the reasons behind them and then note remain 46% higher than average in 2023 relative their emerging implications and knock-on effects. to January 2022 projections.5 The relaxation of China's COVID-19 policies could drive up energy and commodity prices further - and will test the Cost-of-living crisis resilience of global supply chains if policy changes remain unpredictable as infections soar. Ranked as the most severe global risk over the next Cost-of-living crisis was broadly perceived by two years by GRPS respondents, a global Cost-of- GRPS respondents to be a short-term risk, at peak living crisis is already here, with in昀氀ationary pressures severity within the next two years and easing off disproportionately hitting those that can least afford thereafter. But the persistence of a global cost-of- it. Even before the COVID-19 pandemic, the price living crisis could result in a growing proportion of of basic necessities – non-expendable items such the most vulnerable parts of society being priced out 1 as food and housing – were on the rise. Costs of access to basic needs, fueling unrest and political further increased in 2022, primarily due to continued instability. Continued supply-chain disruptions disruptions in the 昀氀ows of energy and food from could lead to sticky core in昀氀ation, particularly in Russia and Ukraine. To curb domestic prices, around food and energy. This could fuel further interest rate 30 countries introduced restrictions, including export hikes, raising the risk of debt distress, a prolonged bans, in food and energy last year, further driving economic downturn and a vicious cycle for 昀椀scal 2 up global in昀氀ation. Despite the latest extension, the planning. looming threat of Russia pulling out of the Black Sea Grain Export Deal has also led to signi昀椀cant volatility in Despite some improvement during the pandemic, the price of essential commodities. household debt has been on the rise in certain Global Risks Report 2023 15
FIGURE 1.4 Price hikes in basic necessities, 2020-2022 30 High income 30 Upper-middle income 25 25 20 20 centage)15 15 10 10 5 5 Inflation (per0 0 -5 -5 Jan May Sep Jan May Sep Jan May Sep Jan May Sep Jan May Sep Jan May Sep 2020 2021 2022 2020 2021 2022 30 Lower-middle income 30 Low income 25 25 20 20 15 15 10 10 5 5 0 0 -5 -5 Jan MayMayMay SepSepSep Jan MayMay SepSep Jan MayMay SepSep Jan May Sep Jan May Sep Jan May Sep 2020 2021 2022 2020 2021 2022 CPI all items Food and non-alcoholic beverages Housing, water, electricity, gas and other fuels Source Note IMF, Consumer Price Index. Median year-on-year inflation, by income group. economies. Global mortgage rates have reached their concerns, leaving emerging and developing countries highest level in more than a decade. Some estimates with far less 昀椀scal room to protect their populations in suggest that the increase in rates amounts to a 35% the future. increase in mortgage payments for homeowners.6 Rent in昀氀ation has also followed suit – in the United Both affordability and availability of basic necessities States of America, it is estimated to peak at over 8% can stoke social and political instability. Last year, 7 in May this year before easing, disproportionately the increase in fuel prices alone led to protests in affecting lower socioeconomic groups who are more an estimated 92 countries, some of which resulted likely to rent but least able to afford rental price hikes. in political upheaval and fatalities, alongside strikes 10 Retirees will also be impacted as pensions fail to and industrial action. The impact of insecurity will 8 keep pace with higher in昀氀ation. Higher costs of food, continue to be felt most acutely in already vulnerable energy and housing, causing lower real incomes, will states – including Somalia, Sudan, South Sudan and result in trade-offs in essential spending, worsening the Syrian Arab Republic – but may also exacerbate health and wellbeing outcomes for communities. instability in countries facing simultaneous food and debt crises, such as Tunisia, Ghana, Pakistan, Egypt 11 Economic impacts are often cushioned by expansive and Lebanon. 昀椀scal policy and government programmes in 9 countries that can afford them. Advanced economies A combination of extreme weather events and continue to roll out measures, many of which have constrained supply could lead the current cost-of- been broad-brush in approach – ranging from caps living crisis into a catastrophic scenario of hunger on electricity bills, fuel rebates and subsidized public and distress for millions in import-dependent transport tickets for consumers, to export controls countries or turn the energy crisis towards a on food, tax relief, enhanced state aid and support humanitarian crisis in the poorest emerging markets. for affected companies. The resulting pressure on Energy shortages – as a result of supplier shut- 昀椀scal balances may exacerbate debt sustainability offs or natural, accidental or intentional damage Global Risks Report 2023 16
to pipelines and energy grids – could cause Economic downturn widespread blackouts and fatalities if combined with seasonal extreme weather. There is also a material possibility of a global food supply crisis occurring in Last year’s edition of the Global Risks Report 2023, with the continuation of the war in Ukraine, warned that in昀氀ation, debt and interest rate rises the lagged effect of a price spike in fertilizer last year were emerging risks. Today, governments and and the impact of extreme weather conditions on central banks – led by developed markets, notably food production in key regions. Estimates suggest the United States of America, Eurozone and the that over 800,000 hectares of farmland were wiped United Kingdom of Great Britain – are walking out by 昀氀oods in Pakistan – increasing commodity a tightrope between managing in昀氀ation without prices signi昀椀cantly in a country that was already triggering a deep or prolonged recession, and 12 grappling with record 27% in昀氀ation. Predicted protecting citizens from a cost-of-living crisis while droughts and water shortages may cause a decline servicing historically high debt loads. Public-sector in harvests and livestock deaths across East Africa, respondents to the GRPS ranked Debt crises (#6), North Africa and Southern Africa, exacerbating food Failure to stabilise price trajectories (#8) and 13 insecurity. “Prolonged economic downturn” (#10) in the top 10 risks over the next two years (Figure 1.3). Although some regions anticipate above-average yields next year, unexpected production or Managing in昀氀ation is a worldwide concern. “Rapid transportation shocks in key exporters – including and / or sustained in昀氀ation” was also highlighted water shortages in the Netherlands and droughts as a top-昀椀ve risk over the next two years in 89 of and large-scale insect loss in the United States the countries surveyed in the EOS, a signi昀椀cant 14 of America and Brazil – or controls imposed by increase from 2021 (Figure 1.5). It was ranked these countries could further destabilize global as the top threat in a number of G20 countries – food security, explored in Chapter 3: Resource including Brazil, South Korea and Mexico – although Rivalries. “Severe commodity price shocks or in昀氀ationary pressures have affected both developed volatility” was a top-昀椀ve risk over the next two and developing economies. In昀氀ation rates rose years in 47 countries surveyed by the Forum’s above 80% in Argentina and Türkiye, while Executive Opinion Survey (EOS), while “Severe Zimbabwe, the Bolivarian Republic of Venezuela, commodity supply crises” registered as a more Lebanon, the Syrian Arab Republic and Sudan localized risk, as a top-昀椀ve concern across 34 witnessed triple-digit in昀氀ation. In昀氀ation in the United countries, including in Switzerland, South Korea, States of America peaked above 9% in June last Singapore, Chile and Türkiye. The catastrophic year and hit record highs in the United Kingdom of effects of famine and loss of life can also have spill- Great Britain and the Eurozone in October, at 11.1% over effects further a昀椀eld, as the risk of widespread and 10.6%, respectively, forcing interest rates higher violence grows and involuntary migration rises. and in昀氀icting more pain on emerging economies.15 FIGURE 1.5 National risk perceptions: inflation "Which five risks are the most likely to pose the biggest threat to your country in the next two years?" A. Failure to stabilize price trajectories, 2021 B. Rapid and / or sustained inflation, 2022 Rank Rank 1 10 20 30 1 10 20 30 Source World Economic Forum Executive Opinion Survey 2022. Global Risks Report 2023 17
The IMF’s most recent projections anticipate a Even if the economic fallout remains comparatively decline in global in昀氀ation from almost 9% in 2022 contained, global growth is forecast to slow to to 6.5% this year and 4.1% in 2024, with a sharper 2.7% in 2023, with around one-third of the world’s 16 disin昀氀ation in advanced economies. However, economy facing a technical recession – the third- 18 downside risks to the outlook loom large. The weakest growth pro昀椀le in over 20 years. This complexity of in昀氀ationary dynamics is creating a downturn will be led by advanced markets, with challenging policy environment for both the public projected growth falling to 1.1% in 2023, while the sector and central banks, given the mix of demand largest economies – the EU, China and the United and supply-side drivers, including a prolonged war States of America – face continued challenges to in Ukraine and associated energy-supply crunch, growth. However, for developing economies, there potential for escalating sanctions, and continued is a risk of further economic distress and tougher bottlenecks from a lingering pandemic or new trade-offs. Stubbornly high in昀氀ation and more sources of supply-side controls. disorderly containment will raise the likelihood of stagnant economic growth, liquidity shocks and Given currently low headline unemployment in debt distress on a global scale. Energy importers in advanced economies, persistent price pressures will particular will bear the brunt of higher energy prices likely lead to higher interest rates to avoid in昀氀ation stemming from a strengthened US dollar, but its de-anchoring. Central banks have sped up the post- continued strength is importing in昀氀ation worldwide. pandemic normalization of monetary policy. Nearly 90% (33 of 38) of central banks monitored by the Globalized capital 昀氀ows over recent decades have Bank for International Settlements raised interest increased exposure of emerging and developing rates in 2022, a dramatic shift away from the loose markets to rising interest rates, especially those 昀椀nancial conditions that characterized the previous with a high proportion of USD-denominated debt, 17 19 decade. With a rapid rise in rates, the risk of such as Argentina, Colombia and Indonesia. Early unintended consequences and policy error is high, tightening of monetary policy in many markets – with possible overshoot leading to a deeper and including Brazil, Mexico, Chile, Peru and Colombia – more prolonged economic downturn and potential minimized initial exposure. But while some countries global recession. have resorted to foreign-exchange interventions FIGURE 1.6 Sovereign debt in default 600 500 400 300 USD Billion 200 100 0 e 8 6 4 2 Defaulted globalpublic debt as shar of global public debt0 1975 1980 1985 1990 1995 2000 2005 2010 2015 2020 Year Advanced economies Emerging-market and frontier economies Heavily indebted poor countries Other developing countries Source Bank of Canada and Bank of England, 2022.20 Global Risks Report 2023 18
to limit currency depreciation and debt-servicing green technologies or build future resilience in loads, heightened volatility continues to drive education, healthcare and ecological systems, with demand for US assets. This has led to record capital impacts exacerbated by the most powerful and out昀氀ows from markets with weaker macroeconomic disproportionately borne by the most vulnerable, as fundamentals, with investors already withdrawing explored in Chapter 2.6: Economic stability. $70 billion from emerging market bond funds by 21 October last year. Geoeconomic warfare Growth agendas, including the critical pivot to greener economies, have been based on the “Geoeconomic confrontation” was ranked the availability of cheap debt. The extent to which third-most severe risk over the next two years by countries can continue to 昀椀nance development GRPS respondents. Interstate confrontations were will be dependent on domestic political and debt anticipated by both GRPS and EOS respondents dynamics. Sri Lanka’s recent crisis provides a very to remain largely economic in nature over the short real example of the spiraling risks to human security term. Geoeconomic confrontation – including and health that can arise from economic distress, sanctions, trade wars and investment screening – where a debt default and shortage in foreign was considered a top-昀椀ve threat over the next two currency limited imports; disrupted access to food, years among 42 countries surveyed by the EOS and fuel, healthcare and electricity; and led to violent featured as the top risk in many East and South- protests and the resignation of the President. East Asian countries, among others. In comparison, “Interstate con昀氀ict” was ranked as a top-昀椀ve risk in The scale of sovereign debt defaults could 28 countries surveyed by the EOS (Figure 1.7). signi昀椀cantly rise in weaker emerging markets over the next two years, in terms of both the percentage The weaponization of economic policy between value of total global debt and number of states in globally integrated powers has highlighted default (Figure 1.6). Although unlikely under the vulnerabilities posed by trade, 昀椀nancial and current trajectory to reach globally destabilizing technological interdependence - for the public and levels, the proportion of countries in or at high risk of private sector alike. The Ukraine con昀氀ict triggered debt distress has already doubled from 2015 levels.22 the imposition of sanctions, nationalization of key This will increase the global in昀氀uence of creditor players, and government appropriation of assets, nations and heighten state fragility as the capacity such as Germany’s seizure of Russian energy 24 to address simultaneous crises in food and energy companies' stakes in local re昀椀neries last year. 23 will be limited. Some countries will be unable to Reputational and legal risks for multinational contain future shocks, invest in future growth and company operations in certain markets also grew: FIGURE 1.7 National risk perceptions: interstate confrontation "Which five risks are the most likely to pose the biggest threat to your country in the next two years?" A. Geoeconomic confrontation B. Interstate conflict Rank Rank 1 10 20 30 1 10 20 30 Source World Economic Forum Executive Opinion Survey 2022. Global Risks Report 2023 19
consumer good companies faced boycotts after also been contemplated by the United States of continuing to provide basic necessities to Russia, America.27 and a European energy company was accused of “complicity in war crimes” due to linkages to a Together, these trends towards geoeconomic Russian gas 昀椀eld.25 warfare risk creating widespread spillovers. More extensive deployment of economic levers to meet In the face of vulnerabilities highlighted by the geopolitical goals risks a vicious and escalating cycle pandemic and then war, economic policy, particularly of distrust. Financial and technological rami昀椀cations in advanced economies, is increasingly directed may highlight further vulnerabilities, leading states to towards geopolitical goals. Countries are seeking proactively wind back other interdependencies in the to build “self-suf昀椀ciency”, underpinned by state aid, name of national security and resilience over the next and achieve “sovereignty” from rival powers, through two years. This may spur contrary outcomes to the onshoring and “friend-shoring” global supply chains. intended objective, driving resilience and productivity Defensive measures to boost local production and growth lower and marking the end of an economic minimize foreign interference in critical industries era characterized by cheaper and globalized capital, include subsidies, tighter investment screening, labour, commodities and goods. data localization policies, visa bans and exclusion of companies from key markets. This will likely continue to weaken existing alliances as nations turn inwards, with enhanced While initially driven by tensions between the United state intervention perceived to drive a “race to States of America and China, many policies are the bottom”. Further pressure will be placed on extra-territorial in nature or have been similarly multilateral governance mechanisms that act as adopted by other markets, with spill-over effects mitigants to these risks, potentially mirroring the across a broad range of industries. For example, politicization of the World Health Organization Switzerland is considering the introduction of a (WHO) during the COVID-19 pandemic and the general cross-sectoral foreign direct investment near paralysis of trade enforcement on more screening regime for the 昀椀rst time. Expanded state contentious issues by the World Trade Organization aid to support self-suf昀椀ciency in “strategically (WTO) in recent years.28 It will also likely embed important products”, including climate mitigation and the importance of broader geopolitical spheres adaptation, has also heightened competition within of in昀氀uence in “dependent” markets, with global global blocs. The EU has already raised concerns powers extensively exercising trade, debt and about the USA's In昀氀ation Reduction Act, which technological power. Although some developing includes signi昀椀cant tax credits and subsidies for local and emerging markets may wield critical resources green technologies.26 as leverage, considered in Chapter 3: Resource Rivalries, anticipated controls on capital, labour, Economic levers are also being used to proactively knowledge and technological 昀氀ows risk widening the constrain the rise of rivals. This includes delisting developmental divide. of foreign companies, extensive use of the foreign direct product rule and export controls on key In addition, spheres of in昀氀uence will not be purely technologies and intellectual property as well as contained to global powers, nor “dependent” broad constraints on citizens and entities working developing and emerging markets. The in昀氀uence and with designated foreign companies. The introduction alignment of the Middle East in regional and global of an outbound investment screening regime has politics will shift. Although the challenge of longer- Global Risks Report 2023 20
term economic diversi昀椀cation remains a signi昀椀cant distraction domestically, the current energy crisis will raise economic, military and political capital of numerous countries over the next two years. Comparative ties of the United States of America and China will have signi昀椀cant rami昀椀cations for the balance of power in the region, as well as global military dynamics, considered further in Chapter 2.4: 29 Human security. Strategies to enhance security may also come at a wider economic cost. Intensi昀椀ed geopolitical tensions risk weakening the economic landscape even further, resulting in lingering in昀氀ation or depressed growth even if current pressures subside. If on- and friend-shoring continue to be prioritized – particularly in strategic industries such as technology, telecommunications, 昀椀nancial systems, agriculture, mining, healthcare and pharmaceuticals – consumers will potentially face rising costs well into the future. As costs of compliance with divergent political and economic systems climb, multinational companies may pragmatically pick a side, speeding up divergence between various market models. While intended to lower risks associated with what is scienti昀椀cally necessary and what is politically geopolitical and economic disruption, shortened expedient. Current pressures should result in supply chains may also unintentionally heighten a turning point, encouraging energy-importing exposure to geographically concentrated risks, countries to invest in “secure”, cleaner and cheaper including labour shortages, civil unrest, pandemics renewable energy sources.32 Yet geopolitical tensions and natural weather events. Geopolitical risks and economic pressures have already limited – and posed by geographic hotspots that are critical to in some cases reversed – progress on climate the effective functioning of the global 昀椀nancial and change mitigation, at least over the short term. For economic system, in particular in the Asia-Paci昀椀c, example, the EU spent at least EUR50 billion on new also pose a growing concern. and expanded fossil-fuel infrastructure and supplies, 33 and some countries restarted coal power stations. Climate action hiatus Despite some longer-term government action on the energy transition, such as the USA’s In昀氀ation Reduction Act and the EU’s REPowerEU plan, Despite 30 years of global climate advocacy and overall momentum for climate mitigation is unlikely to diplomacy, the international system has struggled rapidly accelerate in the next two years. Negotiations to make the required progress on climate change. at the Conference of the Parties of the UNFCCC The potential failure to address this existential global (COP27) failed to reach a much-needed agreement risk 昀椀rst entered the top rankings of the Global to phase out all fossil fuels, laying bare the dif昀椀culty Risks Report over a decade ago, in 2011. Today, of balancing short-term needs with longer-term atmospheric levels of carbon dioxide, methane and ambitions. Policy-makers are increasingly confronted nitrous oxide have all reached record highs. Emission by perceived trade-offs between energy security, trajectories make it very unlikely that global ambitions affordability and sustainability. The stark reality of 600 30 to limit warming to 1.5°C will be achieved. million people in Africa without access to electricity illustrates the failure to deliver change to those A Failure to mitigate climate change is ranked who need it and the continued attraction of quick as one of the most severe threats in the short term fossil-fuel powered solutions – despite the risks but is the global risk we are seen to be the least of stranded assets, energy security challenges of prepared for, with 70% of GRPS respondents rating exported fossil fuel commodities and lifetime carbon existing measures to prevent or prepare for climate emissions that exceed the 1.5°C limit. change as “ineffective” or “highly ineffective” (Figure 4.1). According to the Intergovernmental There is also growing recognition that not only the Panel on Climate Change (IPCC), the chance of pace of the transition but also effectiveness and breaching the 1.5°C target by as early as 2030 integrity matter: climate litigation is increasing and stands at 50%. Current commitments made by the concerns about emissions under-reporting and G7 private sector suggest an increase of 2.7°C by greenwashing have triggered calls for new regulatory 34 mid-century, way above the goals outlined in the oversight for the transition to net zero. While some 31 Paris Agreement. countries have made disclosure mandatory, much of the corporate world have not yet assessed or Recent events have exposed a divergence between started to manage their climate risks. In the absence Global Risks Report 2023 21
of clearer policy signals and consistent regulation report, the impact of these events disproportionately and enforcement, mitigation efforts will be shaped affects low- and middle-income countries. It by increasingly disruptive climate activism, raising registered as a top-昀椀ve risk in 25 countries surveyed the likelihood of stranded assets – as well as people. by the EOS, in particular in developing coastal states A just transition that supports those set to lose across Latin America, Africa and South-East Asia. from decarbonization is increasingly invoked by countries heavily dependent on fossil-fuel industries As 昀氀oods, heatwaves, droughts and other extreme as a reason to slow down efforts. These challenges, weather events become more severe and frequent, against the backdrop of a deteriorating economic a wider set of populations will be affected. In landscape and in昀氀ated input costs, may postpone parallel, a consolidation of public- and private- investments in greener production methods – sector resources may set up emerging and pressing 35 particularly in heavier, “dirtier” industries. trade-offs between disaster recovery, loss and damage, adaptation and mitigation. Although climate All of this implies that the risks of a slower and more mitigation has been overwhelmingly favoured over disorderly transition (extensively covered in last year's adaptation in terms of 昀椀nancing to date, particularly Global Risks Report) have now turned into reality, in the private sector,38 EOS results indicate that potentially leading to dire planetary and societal climate adaptation may now be seen as a more consequences. Any rollback of government and immediate concern in the short term by business private action will continue to amplify risks to human leaders. Failure of climate change mitigation only health (explored in Chapter 2.3: Human health) and featured in the top 昀椀ve risks over the next two years spur the deterioration of natural capital, as discussed in one economy, Zambia, whereas the Failure of in Chapter 2.2: Natural ecosystems. Climate climate-change adaptation was a top-昀椀ve risk change will also increasingly become a key migration in 16 countries, such as the Netherlands, where it driver and there are indications that it has already ranked 昀椀rst (Figure 1.8). The diversion of attention contributed to the emergence of terrorist groups and and resources towards adaptation may further 36 con昀氀icts in Asia, the Middle East and Africa. slow progress on global-warming targets in the economies that remain the biggest contributors to Indeed, with 1.2°C of warming already in the greenhouse gas (GHG) emissions.39 system, the compounding effect of a changing climate is already being felt, magnifying humanitarian Despite plans for a global goal on adaptation challenges such as food insecurity, and adding to be agreed at COP28, there has also been another hefty bill to already stretched 昀椀scal insuf昀椀cient progress towards the support required 37 balances. In the GRPS results, “Natural disasters for infrastructure and populations already affected and extreme weather events” was considered the by the fallout from climate change. Adaptation has second-most severe risk over the next two years. As not been adequately funded, with 34% of climate 40 with many of the global risks featured in this year’s 昀椀nance currently allocated to adaptation worldwide. FIGURE 1.8 National risk perceptions: climate action "Which five risks are the most likely to pose the biggest threat to your country in the next two years?" A. Failure of climate-change adaptation B. Failure of climate-change mitigation Rank Rank 1 10 20 30 1 10 20 30 Source World Economic Forum Executive Opinion Survey 2022. Global Risks Report 2023 22
Nor do new investments in infrastructure or capital Societal polarization allocation decisions adequately consider current and future risks. Investors and policy-makers are locking themselves into costly futures, likely to be borne “Erosion of social cohesion and societal by the most vulnerable. Disagreements on what polarisation” has been climbing in the ranks of constitutes adaptation, and the lack of shared goals perceived severity in recent years.43 De昀椀ned as the and best practices, robust regulatory frameworks loss of social capital and fracturing of communities and metrics, add to a high risk of overshooting and leading to declining social stability, individual and undershooting adaptation efforts. collective wellbeing and economic productivity, it ranked as the 昀椀fth-most severe global risk faced in Limits to adaptation are also increasingly evident. the short term by GRPS respondents. It was also This has been highlighted by the Loss and Damage seen as one of the most strongly in昀氀uenced risks agenda which, after decades on the sidelines of the in the global network, triggered by many other climate discourse, has now reached the mainstream. short- and longer-term potential risks – including A new 昀椀nancing mechanism was tentatively agreed debt crises and state instability, cost-of-living crises at COP27, although the contribution to this fund by and in昀氀ation, a prolonged economic downturn and high-emitting economies remains unclear. Even as climate migration (Figure 1.9). more funding is unlocked, there is a risk of ignoring or avoiding climate-proo昀椀ng against future disasters, as A widening gap in values and equality is posing governments scramble to provide relief and support an existential challenge to both autocratic and in disaster-hit areas. Market-based mechanisms for democratic systems, as economic and social divides managing 昀椀nancial shocks are inadequate and may are translated into political ones. Polarization on diminish further within the next two years. There is a issues such as immigration, gender, reproductive risk of retreat by insurers from some areas of natural rights, ethnicity, religion, climate and even secession catastrophe coverage, with the gap in insurance and anarchism44 have characterized recent elections, estimated to have grown from $117 billion in 2020 to referendums and protests around the world – from 41 $161 billion in 2021. Only 7% of economic losses the United States of America and China to the from 昀氀ood events in emerging markets – and 31% Islamic Republic of Iran. Mounting citizen frustration in advanced economies – have been covered by at perceived gaps in direct governmental action, 42 insurance in the last 20 years. human development and social mobility manifested FIGURE 1.9 Risk interconnections: the erosion of social cohesion Digital power concentration Interstate conflict Digital inequality Terrorist attacks Misinformation and disinformation State collapse Large-scale Erosion of social cohesion involuntary migration Proliferation of illicit Severe mental economic activity health deterioration Reference Infectious diseases Chronic health conditions Employment crises Collapse or lack of public Failure to stabilize price trajectories infrastructure and services Debt crises Prolonged economic Cost-of-living crisis downturn Nodes EdgesEdges Risk influence Relative influence High High Medium Medium Low Low Risk categories Economic Environmental Geopolitical Societal Technological Source World Economic Forum, Global Risks Perception Survey 2022-2023. Global Risks Report 2023 23
in frequently divisive and unruly civil protests last chambers. It was perceived as a moderately severe year. More protests were observed between January risk by GRPS respondents, ranking 16th over the 45 and October than in all of 2021. short term. Regulatory constraints and educational efforts will likely fail to keep pace, and its impact Consequences of societal polarization are vast, will expand with the more widespread usage of ranging from a drag on growth to civil unrest and automation and machine-learning technologies, deepening political 昀椀ssures. And there are indications from bots that imitate human-written text to that increasing polarization is contributing to the deepfakes of politicians.51 decline of democracies and accompanying rise in hybrid regimes, with the share of the world’s Polarization undermines social trust and, in some population living in autocratizing countries rising cases, has re昀氀ected power struggles within a political 52 from 5% in 2011, to 36% in 2021. Only 13% of elite more than underlying divisions in ideologies. the world’s population are currently living under a Often, hardened polarization on key issues lead to liberal democracy, compared to 44% living under an government gridlocks. "Swings" between parties 46 electoral autocracy. each electoral cycle may stymie the adoption of a longer-term policy outlook, causing greater strife, The erosion of the social and political centre risks especially when navigating the dif昀椀cult and uncertain becoming self-perpetuating. Divisions incentivize economic outlook of the coming years. Additionally, the adoption of short-term, more extreme policy although less likely in more democratically robust platforms to galvanize one side of the population states, an increasing presence of anocracies (those and perpetuate populist beliefs. Notably, the forms of government that are part democracy, contest between two, non-centrist candidates or part autocracy, referred to in Chapter 2.5: Digital 47 positions is often close. Although heralded as rights) and factionalism may radicalize polarization. a resurgence of leftist movements, the Brazilian This could lead to increased incidences of threat presidential election of 2022 was won by President campaigns and political violence, hate crimes, violent Lula by 1.8 points – the slimmest margin recorded protests and even civil war.53 48 since it became a democratic nation. As such, a large proportion of the population can feel alienated Social and political polarization may also further and angered by leadership in the following term, reduce the space for collective problem-solving to acting as a multiplier to existing societal concerns address global risks. The far right has been elected and civil unrest. This is further ampli昀椀ed by social in Italy and are now the second largest party in media, which increases polarization and distrust in Sweden, while the left has resurged in Latin America. 49 institutions alongside political engagement. National elections will take place in several G20 countries within the next two years, including the “Misinformation and disinformation” are, United States of America, South Africa, Türkiye, together, a potential accelerant to the erosion of Argentina, Mexico and Indonesia. The election of social cohesion as well as a consequence. With less-centrist leaders and adoption of more “extreme” the potential to destabilize trust in information and policies in economic superpowers may fracture 50 political processes, it has become a prominent tool alliances, limit global collaboration and lead to a for geopolitical agents to propagate extremist beliefs more volatile dynamic. and sway elections through social media echo Global Risks Report 2023 24
1.3 Looking ahead The way risks play out over the next two years are embedding structural changes to the economic has rami昀椀cations for the decade to come. Nearly and geopolitical landscape that will accelerate other one in 昀椀ve respondents to the GRPS felt optimistic global threats faced over the next 10 years. And about the outlook for the world in the longer term, as the con昀氀uence of current crises distracts focus predicting limited volatility with relative – and and resources from risks arising over the medium potentially renewed – stability over the next 10 years to longer-term horizon, we may face increasing (Figure 1.10). Yet, over half anticipated progressive burdens on natural and human ecosystems. Some tipping points and persistent crises leading to of these risks are close to a tipping point, but catastrophic outcomes over the next 10 years, there is a window to shaping a more secure future. or consistent volatility and divergent trajectories. Understanding them is vital. Notably, younger age groups were more hopeful for the future: one in three respondents under the age The next chapter considers the potential global of 40 shifted to a neutral or positive stance over the shocks we are heading towards over the next longer time frame. decade, highlighting worrying developments emerging from the crises of today that are eroding Shocks of recent years – most notably, the war in the resilience and stability of the global system. Ukraine and COVID-19 pandemic – have re昀氀ected It highlights a series of such emergent risks – the and accelerated an epochal change to the global shocks of tomorrow – that can be reduced through order. Risks that are more severe in the short term collective attention and action today. FIGURE 1.10 Short- and long-term global outlook "Which of the following best characterizes your outlook for the world over the short-term (2 years) and longer-term (10 years)? 2% 2% 2 years 13% 69% 14% 10 years 20% 34% 26% 11% 9% Progressive tipping points and persistent crises leading to catastrophic outcomes Consistently volatile across economies and industries with multiple shocks accentuating divergent trajectories Slightly volatile with occasional localised surprises Limited volatility with relative stability Renewed stability with a revival of global resilience Source World Economic Forum, Global Risks Perception Survey 2022-2023. Global Risks Report 2023 25
Endnotes 1. Bogmans, Christian, Andrea Pescatori and Ervina Prifti, “Four Facts about Soaring Consumer Food Prices”, IMF Blog, 24 June 2021, https://www.imf.org/en/Blogs/Articles/2021/06/24/four-facts-about- soaring-consumer-food-prices; Hoffer, Brice, “On the rise: Growth of the global rental housing sector”, UBS, 2021, https://www.ubs.com/content/dam/assets/asset-management-reimagined/global/insights/ asset-class-perspectives/real-estate/docs/white-paper-on-the-rise.pdf. 2. Georgieva, Kristalina, Gita Gopinath and Ceyla Pazarbasioglu, “Why We Must Resist Geoeconomic Fragmentation – and How”, IMF Blog, 22 May 2022, https://www.imf.org/en/Blogs/Articles/2022/05/22/ blog-why-we-must-resist-geoeconomic-fragmentation. 3. Federal Reserve Bank of New York, Global Supply Chain Pressure Index, https://www.newyorkfed.org/ research/policy/gscpi#/interactive, accessed 27 October 2022. 4. Food and Agriculture Organisation of the United Nations (FAO), FAOSTAT: Consumer Price Indices, https://www.fao.org/faostat/en/#data/CP, accessed 27 October 2022. 5. Guénette, Justin-Damien and Jeetendra Khadan, 2022, “The energy shock could sap global growth for years”, World Bank blogs, 22 June 2022. 6. Anstey, Chris, “What's Happening in the World Economy: Unforgiving Mortgage Rates”, Bloomberg. com, 6 October 2022, https://www.bloomberg.com/news/newsletters/2022-10-06/what-s-happening- in-the-world-economy-unforgiving-mortgage-rates; Dickler, Jessica, “Another Interest Rate Hike from the Federal Reserve Is on the Way: Here's How It May Affect You”, CNBC, 31 October 2022, https://www. cnbc.com/2022/10/31/another-fed-rate-hike-is-onthe-way-heres-how-it-could-impact-you.html. 7. Zhou, Xiaoqing and Jim Dolmas, “Rent in昀氀ation expected to accelerate then moderate in mid-2023”, Federal Reserve Bank of Dallas, 16 August 2022. 8. Pearce, Graham, Kate Bravery, Adrienne Cernigoi, and Sumer Drall, “Risk and retirement: where are the future 昀椀nancial hotspots?”, Marsh McLennan, September 2022, https://www.marshmclennan.com/ insights/publications/2022/september/risk-and-retirement-where-are-the-future-昀椀nancial-hotspots.html. 9. Credit Suisse Research Institute, Global Wealth Report 2022: Leading perspectives to navigate the future, 2022, https://www.credit-suisse.com/about-us/en/reports-research/global-wealth-report. html#:~:text=Global%20Wealth%20Report%202022&text=Total%20global%20wealth%20grew%20 by,fastest%20annual%20rate%20ever%20recorded, accessed 14 November 2022; Federal Reserve Bank of New York, Total Household Debt Surpasses $16 trillion in Q2 2022; Mortgage, Auto Loan and Credit Card Balances Increase, 2 August 2022. 10. Gebreab, Efrem, Thomas Naadi, Ranga Sirilal and Becky Dale, “Fuel protests gripping more than 90 countries”, BBC, 17 October 2022, https://www.bbc.com/news/world-63185186. 11. Food and Agriculture Organisation of the United Nations (FAO), War in Ukraine intensi昀椀es food security risks in the Southern and Eastern Mediterranean, 8 September 2022, https://www.fao.org/support-to- investment/news/detail/en/c/1603647/. 12. Haq, Mifrah, “Pakistan Faces Hunger Crisis as Floods Wash Away Crops, Livestock”, Nikkei Asia, 13 September 2022, https://asia.nikkei.com/Economy/Natural-disasters/Pakistan-faces-hunger-crisis-as- 昀氀oods-wash-away-crops-livestock. 13. Food and Agriculture Organisation of the United Nations (FAO), Crop prospects and food situation, September 2022, 14 November 2022, https://www.fao.org/3/cc2300en/cc2300en.pdf. 14. Hance, Jeremy, “Trouble in the tropics: The terrestrial insects of Brazil are in decline”, Mongabay, 5 October 2022; Jepsen, Sarina, “California Supreme Court let decision stand that bees can be protected by the California Endangered Species Act”, Xerces Society for Invertebrate Conservation, 22 September 2022. 15. Trading Economics, In昀氀ation Rate, https://tradingeconomics.com/country-list/in昀氀ation- rate?continent=world, accessed 14 November 2022; Amaro, Silvia, “Euro zone in昀氀ation hits record high of 10.7% as growth slows sharply”, CNBC, 31 October 2022. 16. IMF, World Economic Outlook Report October 2022: Countering the cost-of-living crisis, October 2022, 2022, https://www.imf.org/en/Publications/WEO/Issues/2022/10/11/world-economic-outlook- october-2022. 17. Bank of International Settlements, Central bank policy rates, https://www.bis.org/statistics/cbpol. htm?m=2679, accessed 27 October 2022. 18. IMF, World Economic Outlook Report October 2022: Countering the cost-of-living crisis, October 2022, 2022, https://www.imf.org/en/Publications/WEO/Issues/2022/10/11/world-economic-outlook- october-2022. 19. Echavarria, Paulina Restrepo and Praew Grittayaphong, “Dollar-denominated public debt in Asia and Latin America”, Federal Reserve Bank of St Louis, 3 August 2021, https://www.stlouisfed.org/on-the- economy/2021/august/dollar-exposure-public-debt-asia-latin-america. 20. Beers, David, et. al, “BoC-BoE Sovereign Default Database: What’s new in 2022”, Bank of Canada, https://www.bankofcanada.ca/wp-content/uploads/2022/08/san2022-11.pdf, accessed 14 November 2022. Global Risks Report 2023 26
Endnotes 21. Wheatley, Jonathan, “Out昀氀ows from emerging market bond funds reach $70 billion in 2022”, Financial Times, 2 October 2022. 22. Chabert, Guillaume, Martin Cerisola and Dalia Hakura, "Restructuring debt of poorer nations requires more ef昀椀cient coordination”, IMF Blogs, 7 April 2022. 23. Schnabel, Isabel, Speech: A new age of energy in昀氀ation: climate昀氀ation, fossil昀氀ation, and green昀氀ation, 17 March 2022, speech presented at The ECB and its Watchers XXII Conference, Frankfurt, https:// www.ecb.europa.eu/press/key/date/2022/html/ecb.sp220317_2~dbb3582f0a.en.html, accessed 14 November 2022. 24. Leggett, Theo, “Germany takes control of stakes in Rosneft oil re昀椀neries”, BBC, 16 September 2022, https://www.bbc.com/news/business-62924071. 25. Bryan, Kenza and Sarah White, “Total accused of being complicit in Russian war crimes in Ukraine”, Financial Times, 14 October 2022; Gretler, Connie, “Nestle defends its Russia stance saying food is a basic right amid war”, Bloomberg, 7 April 2022. 26. Bounds, Andy, “EU accuses US of breaking WTO rules with green energy incentives”, Financial Times, 6 November 2022. 27. Liu, Qianer, Kathrin Hille and Yuan Yang, “World’s top chip equipment suppliers halt business with China”, Financial Times, 13 October 2022. 28. Farge, Emma, “WTO can reach deals on 'dif昀椀cult' topics by early 2024 - WTO chief”, Reuters, 27 September 2022; Gruszczynski, Lukasz and Margherita Melillo, “The Uneasy Coexistence of Expertise and Politics in the World Health Organization”, International Organisations Law Review, 24 March 2022. 29. Moonakal, Nadeem Ahmed, “The Impact and Implications of China’s Growing In昀氀uence in the Middle East”, The Diplomat, 9 July 2022. 30. 2021 data. World Meterological Organization, Greenhouse Gas Bulletin, 26 October 2022. 31. Davis, James and Robert Bailey, “Missing the Mark”, Oliver Wyman & CDP, 2022, https://www. oliverwyman.com/our-expertise/insights/2022/sep/cdp-temperature-ratings.html. 32. Mulder, Nicholas, The Sanctions Weapon, Finance & Development, June 2022; Papathanasiou, Demetrios, “Renewables are the key to green, secure, affordable energy”, World Bank Blogs, 21 June 2022, https://blogs.worldbank.org/energy/renewables-are-key-green-secure-affordable-energy. 33. Hancock, Alice, “Europe’s new dirty energy: the ‘unavoidable evil’ of wartime fossil fuels”, Financial Times, 6 September 2022. 34. UN Secretary General’s High-Level Expert Group on Net-Zero Emissions Commitments of Non-State Entities, Integrity Matters, 8 November 2022, https://www.un.org/en/climatechange/high-level-expert- group. 35. The Economist, Germany faces a looming threat of deindustrialisation, 11 September 2022, https:// www.economist.com/business/2022/09/11/germany-faces-a-looming-threat-of-deindustrialisation?itm_ source=parsely-api. 36. Silke, Andrew and John Morrison, “Gathering Storm: An Introduction to the Special Issue of Climate Change and Terrorism”, Terrorism and Political Violence, vol. 35, iss 5, 5 July 2022, pp. 883-893. 37. For more detail on the complex link between extreme weather events and anthropogenic causes, refer to World Meteorological Organization, Atlas of Mortality and Economic Losses from Weather, Climate and Water Extremes (1970–2019), WMO-No. 1267, 2021. 38. Pörtner, Hans-Otto (ed.) et. al, Climate Change 2022: Impacts, Adaptation and Vulnerability, IPCC, 2022. 39. Bellon, Matthieu and Emmanuele Massetti, “Economic Principles for Integrating Adaptation to Climate Change into Fiscal Policy”, IMF, March 2022; Pörtner, Hans-Otto (ed.) et. al, Climate Change 2022: Impacts, Adaptation and Vulnerability, IPCC, 2022. 40. UN Environment Programme (UNEP), Adaptation Gap Report 2022, 1 November 2022. 41. Bevere, Lucia and Federica Remondi, Sigma: Natural catastrophes in 2021: the 昀氀oodgates are open, Swiss Re Institute, 30 March 2022. 42. Ibid. 43. Formerly described as “Profound social instability” in the GRPS. 44. Ganesh, Janan, “Anarchy is a likelier future for the west than tyranny”, Financial Times, 21 June 2022. 45. Carnegie Endowment for International Peace, Global Protest Tracker, 2022, November 9, https:// carnegieendowment.org/publications/interactive/protest-tracker. Global Risks Report 2023 27
Endnotes 46. V-Dem Institute, Democracy Report 2022: Autocratization Changing Nature?, University of Gothenburg, 2022, https://www.v-dem.net/documents/19/dr_2022_ipyOpLP.pdf; Somer, Murat and Jennifer L. McCoy, “Pernicious polarization, autocratization and opposition strategies”, Democratization, vol 28, 12 Jan 2021; McCoy, Jennifer and Benjamin Press, What Happens When Democracies Become Perniciously Polarized?, Carnegie Endowment for International Peace, 18 January 2022. 47. Buschschlüter, Vanessa, “Brazil election: Lula makes stunning comeback”, BBC, 31 October 2022. 48. Mano, Ana and Anthony Boadle, “Brazil's Bolsonaro Silent on Lula Victory, Transition Talks Begin”, Reuters, 1 November 2022, https://www.reuters.com/world/americas/lula-wins-brazilian-election- bolsonaro-has-not-conceded-2022-10-31/. 49. Lewandowsky, Stephan, et. al, “Is the global decline in democracy linked to social media? We combed through the evidence to 昀椀nd out”, The Conversation, 8 November 2022. 50. Favaro, Marina, Neil Renic and Ulrich Kühn, Negative Multiplicity: Forecasting the Future Impact of Emerging Technologies on International Stability and Human Security, Institute for Peace Research and Security Policy, September 2022. 51. Lai, Samantha, Data misuse and disinformation: Technology and the 2022 elections, Brookings Institute, 21 June 2022. 52. Lee, Amber Hye-Yon, “Social Trust in Polarized Times: How Perceptions of Political Polarization Affect Americans’ Trust in Each Other”, Political Behaviour, vol. 44, no. 3, 18 March 2022, pp. 1533-1544; Carothers, Thomas and Andrew O’Donohue, How to Understand the Global Spread of Political Polarization, Carnegie Endowment for International Peace, 1 October 2019. 53. Walter, Barbara, “Why should we worry that the US could become an 'anocracy' again? Because of the threat of civil war”, The Washington Post, 24 January 2022, https://www.washingtonpost.com/ opinions/2022/01/24/why-should-we-worry-that-us-could-become-an-anocracy-again-because-threat- civil-war/. Global Risks Report 2023 28
January 2023 Global Risks Report 2023 Tomorrow’s Catastrophes 2 Global Risks 2033: Tomorrow’s Catastrophes 2.1 The world in 2033 As risks highlighted in the past chapter unfold Based on GRPS results, the longer-term global today, much-needed attention and resources are risks landscape is also dominated by deteriorating being diverted from global risks that may become environmental risks (Figure 2.1). More speci昀椀cally, tomorrow’s shocks and crises. The Global Risks climate- and nature-related risks lead the top 10 Perceptions Survey (GRPS) addresses a one-, risks, by severity, that are expected to manifest two- and 10-year horizon. Chapter one addressed over the next decade. Differentiated as separate the present and two-year time frame, focusing on risks for the 昀椀rst time in the GRPS, Failure to currently unfolding and shorter-term risks. This mitigate climate change and Failure of climate- chapter focuses on the third time frame: risks that change adaptation top the rankings as the most may have the most severe impact over the next 10 severe risks on a global scale, followed by Natural years. disasters and extreme weather events and “Biodiversity loss and ecosystem collapse”. FIGURE 2.1 Global risks ranked by severity over the long term (10 years) 1 Failure to mitigate climate change 6 Natural resource crises 2 Failure of climate-change adaptation 7 Erosion of social cohesion and societal polarization 3 Natural disasters and extreme weather 8 Widespread cybercrime and cyber insecurity events 4 Biodiversity loss and ecosystem collapse 9 Geoeconomic confrontation 5 Large-scale involuntary migration 10 Large-scale environmental damage incidents Risk categories Economic Environmental Geopolitical Societal Technological Source World Economic Forum Global Risks Perception Survey 2022-2023. Comparing the two-year and 10-year time frames worsening scores over the course of the 10-year provides a picture of areas of increasing, decreasing time frame, indicating respondents’ concerns about and continued concerns according to GRPS increased severity of these risks in the longer term. respondents (Figure 2.2). The top right of the graph “Large-scale involuntary migration, rises to 昀椀fth indicates global risks that are perceived to be place in the 10-year time frame, while Erosion the most severe in both the short and long term. of social cohesion and societal polarization is These are consistent areas of global concern and, perceived to be slightly more severe over the longer arguably, attention. Four environmental risks have term. Global Risks Report 2023 29
Risks that are growing in severity over the The far right of the graph indicates that today’s longer term include “Biodiversity loss and most prominent risk, the “Cost-of-living crisis”, is ecosystem collapse” and “Misinformation and anticipated to drop in severity over the longer term. disinformation”. Among other technological risks, Towards the center, the scores of geopolitical risks as indicated in the far left of the graph, “Digital were mixed, with the “Use of weapons of mass inequality and lack of access to digital services” destruction” remaining consistent, “State collapse and “Adverse outcomes of frontier technologies” or severe instability” and “Ineffectiveness of are also anticipated to signi昀椀cantly deteriorate over multilateral institutions” worsening and Interstate the 10-year time frame. con昀氀ict perceived as decreasing in severity. The scores of multiple social risks are also worsening, This year, we look at 昀椀ve newly emerging or rapidly including “Severe mental health deterioration”, accelerating risks clusters – drawn from the “Collapse or lack of public infrastructure and economic, environmental, societal, geopolitical and services”, and “Chronic diseases and health technological domains, respectively – that could conditions”. In contrast, economic risks such become tomorrow’s crisis. We explore their current as “Failure to stabilize price trajectories”, “A drivers and emerging implications, and brie昀氀y touch prolonged economic downturn”, “Collapse of a on opportunities to forestall and reshape these systemically important industry or supply chain”, outcomes by acting today. and “Asset bubble burst” are perceived to fall slightly in expected severity over the 10-year time frame. FIGURE 2.2 Relative severity of risks over a 2 and 10-year period Higher 6.0 severity Failure to mitigate climate change Failure of climate-change adaption Natural disasters and extreme weather Biodiversity loss and ecosystem collapse Large-scale involuntary Natural resource crises migration Erosion of social cohesion Widespread cybercrime and societal polarization and cyber insecurity Geoeconomic confrontation Misinformation and disinformation Large-scale environmental 5.0 Ineffectiveness of multilateral institutions damage incidents and international cooperation Chronic diseases and health conditions Severe mental health deterioration Interstate conflict Debt crises Adverse outcomes of Cost-of-living crisis frontier technologies Failure to stabilize price trajectories Prolonged economic Long-term severity downturn Digital inquality Asset bubble burst Terrorist attacks 4.0 Collapse or lack of public infrastructure and services 3.3 3.3 4.0 5.0 6.0 Short-term severity Higher severity Risk categories Economic Environmental Geopolitical Societal Technological Source Note World Economic Forum Global Risks Severity was assessed on a 1-7 Likert scale [1 – Low severity, 7 – High severity]. Perception Survey 2022-2023. Global Risks Report 2023 30
These include: • Digital rights: the potential evolution of data and cyber insecurity, given the slow-burning, • Natural ecosystems: deteriorating risks to insidious erosion of the digital autonomy of natural capital (“assets” such as water, forests individuals, putting privacy in peril. and living organisms) due to growing trade-offs and feedback mechanisms relating to climate • Economic stability: growing debt crises, with change, taking us past the point of no return. repercussions for 昀椀nancial contagion as well as collapse of social services, emerging from a • Human health: chronic risks that are being global reckoning on debt and leading to social compounded by strained healthcare systems distress. facing the social, economic and health aftereffects of the COVID-19 pandemic. The newly emerging or rapidly accelerating risk clusters identi昀椀ed this year are not intended to be • Human security: a nascent reversal in exhaustive. Rather, they aim to provide topic-speci昀椀c demilitarization and growing vulnerability of nuclear- analysis, nudge pre-emptive action and attention, armed states to emerging technologies, emerging and serve as examples for applying similar analysis from new weapons and multi-domain con昀氀icts. to a range of other future risk domains. 2.2 Natural ecosystems: past the point of no return Biodiversity within and between ecosystems is for a dangerous mix (Figure 2.3). Given that over already declining faster than at any other point half of the world's economic output is estimated 1 during human history. Unlike other environmental to be moderately to highly dependent on nature, risks, Biodiversity loss and ecosystem collapse the collapse of ecosystems will have far-reaching was not seen as pressing of a concern by GRPS economic and societal consequences. These include respondents over the short term. Yet it accelerates increased occurrence of zoonotic diseases, a fall in perceived severity, rising to 4th place over the 10- in crop yields and nutritional value, growing water year time frame (Figure 2.1). stress exacerbating potentially violent con昀氀ict, loss of livelihoods dependent on food systems and Human interventions have negatively impacted a nature-based services like pollination, and ever more complex and delicately balanced global natural dramatic 昀氀oods, sea-level rises and erosion from the ecosystem, triggering a chain of reactions. Over the degradation of natural 昀氀ood protection systems like next 10 years, the interplay between biodiversity water meadows and coastal mangroves. loss, pollution, natural resource consumption, climate change and socioeconomic drivers will make FIGURE 2.3 Compounding environmental crises Environmental damage incidents Failure to mitigate climate change Natural disasters and extreme weather Biodiversity loss and Failure of climate-change ecosystem collapse Reference adaption Natural resource crises Chronic health conditions Nodes EdgesEdges Risk influence Relative influence High High Medium Medium Low Low Risk categories Economic Environmental Geopolitical Societal Technological Source World Economic Forum, Global Risks Perception Survey 2022-2023. Global Risks Report 2023 31
Terrestrial and marine ecosystems are facing and other natural disasters are already degrading multiple pressure points due to their undervalued nature-based solutions to climate change, such contribution to the global economy as well as overall as wild昀椀res in forests used for carbon offsetting.7 planetary health. While not the sole drivers, at the In addition, a variety of ecosystems are at risk of heart of this potential catastrophe are key trade- tipping over into self-perpetuating and irreversible offs and feedback mechanisms emerging from change that will accelerate and compound the current crises. Without signi昀椀cant policy change or impacts of climate change. Continued damage to investments, the complex linkages between climate carbon sinks through deforestation and permafrost change mitigation, food insecurity and biodiversity thaw, for example, and a decline in carbon storage degradation will accelerate ecosystem collapse. productivity (soils and the ocean) may turn these ecosystems into “natural” sources of carbon and 8 methane emissions. The impending collapse of Exponentially accelerating nature the Greenland and West Antarctic ice sheets may loss and climate change contribute to sea-level rise and coastal 昀氀ooding, while the “die-off” of low-latitude coral reefs, the nurseries of marine life, are sure to impact food Nature loss and climate change are intrinsically supplies and broader marine ecosystems. interlinked – a failure in one sphere will cascade into the other, and attaining net zero will require 2 mitigatory measures for both levers. If we are Trade-offs between food security unable to limit warming to 1.5°C or even 2°C, the and nature conservation continued impact of natural disasters, temperature and precipitation changes will become the dominant cause of biodiversity loss, in terms of composition Land-use change remains the most proli昀椀c threat and function (Figure 2.4).3 Heatwaves and droughts to nature, according to many experts.9 Agriculture are already causing mass mortality events (a single and animal farming alone take up more than 35% of hot day in 2014 killed more than 45,000 昀氀ying foxes Earth's terrestrial surface and are the biggest direct in Australia), while sea level rises and heavy storms drivers of wildlife decline globally. The ongoing crisis 4 have caused the 昀椀rst extinctions of entire species. in the affordability and availability of food supplies Arctic sea-ice, warm-water coral reefs and terrestrial positions efforts to conserve and restore terrestrial ecosystems have been found most at risk in the biodiversity at odds with domestic food security, as near term, followed by forest, kelp and seagrass explored in Chapter 3: Resource Rivalries. 5 ecosystems. Conservation efforts and nature-based solutions The impacts of climate change on ecosystems can (which can offer biodiversity co-bene昀椀ts) will struggle further constrain their mitigation effects. Increased to be commercially competitive with intensive, severity and frequency of extreme weather events yield-focused agricultural practices, particularly in FIGURE 2.4 Impacts of climate change on ecosystems Confidence in attribution to climate change Changes in ecosystem structure Species range shifts Changes in timing (phenology) Ecosystems Terrestrial Freshwater Ocean Terrestrial Freshwater Ocean Terrestrial Freshwater Ocean Global High High High High High High High High High Africa High High High High Lim. evidence High Lim. evidence Low Low Asia High Medium High Low Medium Lim. evidence Low Low Medium Australasia High High High High Lim. evidence High High Lim. evidence Low Central and South America High High High High High High Lim. evidence Lim. evidence Low Europe High High High High High High High High High North America High High High High High High High High High Small Islands High High High High High High High Lim. evidence Medium Arctic High Medium High High High High High Medium High Antarctic Medium Lim. evidence Medium Medium Lim. evidence Medium Medium Lim. evidence Lim. evidence Mediterrean region High Lim. evidence High High Medium High High Lim. evidence Medium Tropical forest High Lim. evidence N/A Medium Lim. evidence N/A Lim. evidence Lim. evidence N/A Mountain regions High High N/A High Medium N/A High Low N/A Deserts High N/A N/A High N/A N/A Lim. evidence N/A N/A Biodiversity hotspots High Lim. evidence High High Lim. evidence High High Lim. evidence Not assessed Source 6 IPCC, 2022. Global Risks Report 2023 32
densely populated, agrarian nations. State incentives Yet, there is a more existential feedback mechanism to boost local production and reduce reliance on to consider: biodiversity contributes to the health and imports – in a reaction to current geopolitical and resilience of soil, plants and animals, and its decline supply pressures – could come at the cost of puts both food production yields and nutritional value 18 ecosystem preservation. Technology will provide at risk. This could then fuel deforestation, increase partial solutions in the countries that can afford it. For food prices, threaten local livelihoods and contribute example, the global vertical farming market has been to diet-related diseases and mortality (explored in predicted to grow at a compound annual rate of Chapter 2.3: Human health). It may also lead to 10 26% and hit $34 billion by 2033. These agricultural Large-scale involuntary migration, a new entrant production techniques increase food output per unit in the Top 10 rankings in the GRPS survey (Figure area with a smaller water and biodiversity footprint, 2.1) and analysed in last year’s Global Risks Report but can actually be more carbon-intensive and may chapter ‘Barriers to Migration’. have an indirect land footprint that exceeds open- 11 昀椀eld farming in some regions. New battlefronts between ecosys- Given a highly uncertain economic outlook, tems and “green” energy sources developing and emerging markets may struggle to close the funding gap to increase agricultural productivity. Pressure on biodiversity will likely be The transition to clean energy is critical for the further ampli昀椀ed by continued deforestation for mitigation of climate change by reducing the carbon agricultural processes, with an associated demand for footprint of energy compared to fossil fuels. Yet 12 additional cleared cropland, especially in subtropical the rapid expansion of green infrastructure in a and tropical areas with dense biodiversity such as quest for energy security may have unintended 13 Sub-Saharan Africa and Southeast Asia. Biodiversity impacts on domestic and broader ecosystems, and ecosystem preservation could be supported as the dependencies on and risks to natural through the expanded use of concessional 昀椀nancing ecosystems of these technologies are, presently, and debt restructuring: 58 developing countries less well understood. Although renewable energy exposed to climate change have almost $500 billion infrastructure can be “nature-positive” – for example, in collective debt reservicing payments due in the wind farms acting as a “safe haven” for the recovery 14 next four years. Increased deployment of debt-for- of marine populations and the seabed – green nature swaps, for example, could be targeted towards sources of energy can also cause environmental conservation and restoration. In fact, this type of degradation, such as habitat loss, sound and restructuring is being pursued by Ecuador, Sri Lanka electromagnetic pollution, introduction of non- 15 and Cape Verde. However, these mechanisms indigenous species and changes to animal migratory could contribute to shorter term challenges of patterns.19 food insecurity, rising cost of living and declining government revenue.16 In addition, indigenous Renewable energy technologies are also reliant communities can be disproportionately at risk from on non-renewable, abiotic natural capital (metals these activities. “Fortress conservation” can encroach and minerals, as explored in Chapter 3: Resource on indigenous land tenure and has previously been Rivalries). These are sourced from the geosphere, 17 linked to forced evictions, even fatalities. which, together with the hydrosphere, provide the physical habitat for the global ecosystem. These resources are often concentrated in countries with poor governance of nascent, artisanal and illicit mining, or less stringent environmental and social regulations – increasing the likelihood of more widespread destruction of nature and devastation of local communities and indigenous groups. Mining of rare earth elements in Myanmar and the Democratic Republic of the Congo have already caused widespread deforestation, habitat destruction of endangered species and water pollution, and have been linked to human rights abuses and 昀椀nancing of militia groups.20 While offering the possibility of socioeconomic development and diversi昀椀cation, the expansion of green metals mining in nature-rich or ecologically sensitive areas, such as the Plurinational State of Bolivia and Greenland, has the potential to 21 destabilize water tables and disrupt ecosystems. The pressure to push ahead with deep-sea mining also entails signi昀椀cant risks, due to the unknown impacts to critical oceanic ecosystems.22 It is clear that both the scale and pace needed to transition to a green economy require new technologies. However, some of these technologies Global Risks Report 2023 33
risk impacting natural ecosystems in new ways, restoring 30% of the planet’s degraded ecosystems. with limited opportunity to “昀椀eld-test” results. The These signi昀椀cant steps con昀椀rm that the global urgency of climate change mitigation is incentivizing community recognizes that the risks associated the deployment of new technologies, potentially with nature loss, food production, energy generation with less stringent testing and protocols. Carbon and climate change cannot be fully mitigated in removal technologies will be particularly essential to isolation. However, the translation into public- and achieve a net zero world if anthropogenic emissions private-sector action remains to be seen, particularly do not suf昀椀ciently decline, or emissions from natural given limited progress on previous biodiversity – and resources continue to increase. Gene editing to climate – targets to date. enhance natural carbon capture productivity, 23 geoengineering for carbon removal, and solar Although the relationship between climate and nature radiation management all pose major future risks heightens the likelihood of a series of escalating and – from enhanced water stress, nutrient “robbing” potentially irreversible feedback loops, it can equally and redistribution of diseases to termination shock be leveraged to broaden the impact of risk mitigation and the weaponization of stratospheric aerosol activities. Given increasing 昀椀nancial and capacity 24 technologies. Unintended consequences relating to trade-offs, investment in resilience must focus technological “edits” to the atmosphere, biosphere, on solutions that build preparedness for multiple hydrosphere and geosphere can occur at speed, risks. By restoring biodiversity in soils, for example, raising the risk of accidental extinction events. regenerative agriculture has the potential to store large amounts of carbon. Acting today A focus on biodiversity preservation should drive and prioritize local adaptation and community resilience – and in doing so, contribute to the mitigation of Averting tipping points requires a combination of climate change globally. Altered land management conservation efforts, interventions to transform the practices like afforestation, micro-irrigation and food system, accelerated and nature-positive climate agroforestry are a low-cost way to increase resilience mitigation strategies, and changes to consumption to extreme weather. The protection and restoration and production patterns. This involves realigning of marine biodiversity, such as mangrove systems, incentives and upgrading governance structures, can enhance rather than compete with domestic fueled by better data and tools to capture the food web productivity and security. It can also interdependencies of food, climate, energy and support local industries and livelihoods and provide ecosystems. protection from extreme weather. Such activities also produce co-bene昀椀ts at a global level, such There are already initial signs of shifts in this as enhancing carbon sequestration and climate direction. The increasing visibility and in昀氀uence of regulation, offering potential revenue streams for multilateral and market-led initiatives such as the developing nations in the form of carbon credits. Taskforce for Nature-related Financial Disclosures Similarly, scaling up practices such as biocultural (TFND) set to launch later this year, are positive preservation, indigenous community management developments. The 15th Conference of Parties to and integration of traditional knowledge into the Convention of Biological Diversity (CBD COP15) food production and cultivation can provide dual 25 resulted in the Montreal-Kunming agreement, setting socioeconomic and environmental bene昀椀ts. out new global targets for 2030 such as reforming environmentally damaging subsidy systems and Global Risks Report 2023 34
2.3 Human health: perma-pandemics and chronic capacity challenges Global public health is under growing pressure and health systems around the world are at risk of becoming un昀椀t for purpose. The COVID-19 pandemic further ampli昀椀ed ever-present spectres and emerging risks to physical and mental health, including antimicrobial resistance (AMR), vaccine hesitancy and climate-driven nutritional and infectious diseases (described in ‘False Positive: Health Systems under New Pressures’ in our 2020 edition, published before the pandemic took hold). Given current crises, mental health may also be exacerbated by increasing stressors such as violence, poverty and loneliness. There is also a rising risk of a “panic-neglect” cycle. As COVID-19 recedes from the headlines, complacency appears to be setting in on preparing for future pandemics and other global health threats. Healthcare systems face worker burnout and continued shortages at a time when 昀椀scal consolidation risks de昀氀ecting attention and resources elsewhere. More frequent and widespread infectious disease outbreaks amidst a background of chronic diseases over the next decade risks pushing exhausted healthcare systems to the brink of failure and nature loss are heightening the emergence 26 around the world. and re-emergence of diseases, including invasive fungal diseases, while global warming is increasing the number of months suitable for transmission Pandemic aftershocks meet of existing diseases such as malaria and dengue 30 silent health crises fever. Climate change is also expected to exacerbate malnutrition as food insecurity grows. Increased levels of carbon dioxide in the atmosphere Global health outcomes have been weakened by can result in nutrient de昀椀ciencies in plants, and even the COVID-19 pandemic, with lingering effects. accelerated uptake of heavy minerals, which have Early evidence points to a post-COVID-19 condition been linked to cancer, diabetes, heart disease and impacting the quality of life and occupational status impaired growth.31 of individuals – contributing to work absences and early retirements, tighter labour markets and Expanding sources of disease will combine with a decline in economic productivity. The resulting persistent disease burdens to entrench a growing economic hit is estimated to be from roughly health burden in developing and advanced $140-600 billion to up to $3.7 trillion in the United economies alike. There has been a noticeable shift States of America, and close to AUD$5 billion per towards non-communicable diseases over the past year in Australia if current costs persist, re昀氀ecting decade (Figure 2.5), linked to population growth loss of quality of life, lost earnings and output, and and ageing alongside lagging coverage by health 27 higher spending on medical care. The pandemic systems. A key implication is the resulting loss of also diverted resources from other diseases functional health and rise in disabilities, rather than such as cancer screening and tuberculosis,28 deaths. Medical advances have made it possible and immunization campaigns were put on hold. for people to live with multiple co-morbidities Vaccination rates for polio fell to the lowest level in (such as diabetes, hypertension, heart disease 14 years, perhaps ushering in the return of the wild and depression), but these remain complex and 29 strain to Africa in 2021. expensive to manage. People are living more years in poor health, and we may soon face a more Beyond the lingering impact of COVID-19, the sustained reversal in life expectancy gains beyond potential stresses imposed by climate change and the in昀氀uence of the pandemic. nature loss on health are likely to grow, ranging from air pollution and heightened exposure to wet Notably, although some disease burdens are heatwave days (which increase heat stress on growing, all health-related risks fell into roughly humans), to disrupted access to safe water and the bottom third of the GRPS’ global risk rankings sanitation and increases in waterborne diseases over both the two- and 10-year period (Figure due to 昀氀oods. Urbanization, land use change 2.2). “Infectious diseases” plummeted in risk Global Risks Report 2023 35
FIGURE 2.5 Loss of functional health Higher share Lower back pain Headache disorders Depressive disorders Headache disorders Age rAge related and other hearing losselated and other hearing loss Other musculoskeletal disorOther musculoskeletal disordersders Diabetes mellitusDiabetes mellitus e of all YLD Gynecological diseases Shar Anxiety disorders Lower share -100% -50% 0 +50% +100% Percentage change (2009-2019) Disease types Non-communicable Communicable, maternal, neonatal and nutritional Source Note IHME, 2020.32 Annual percentage change to years lived with disability (YLD) from 2009 to 2019. perceptions, from the sixth-most severe risk on a outcomes may have been far worse in the absence global scale over the next 10 years in last year’s of rapid action, the comparisons highlight the Global Risks Report, to 27th place this year. Further, potential of silent crises to create compounding, female respondents to the GRPS consistently runaway damage. assessed health-related risks as more severe than their male counterparts. Chronic diseases and health conditions and Severe mental health Chronic capacity challenges deterioration were ranked 13th and 14th by female respondents, with the related Collapse or lack of public infrastructure and services in 19th place, As disease burden grows and innovation widens compared to rankings of 23rd, 28th and 27th, the scope of what medicine can treat, inexorable respectively, by male respondents. demand for healthcare is running up against chronic capacity challenges. The COVID-19 pandemic The decline in risk perception is likely driven by disrupted the delivery of prevention and treatment pandemic fatigue and the human tendency to services, resulting in a backlog for hospital and focus on fresh, recent and more visible crises. community care that may prove challenging to clear. Yet “silent” crises with cumulative impacts can More than 7 million people in the United Kingdom of quickly outpace a one-off, catastrophic event. The Great Britain (more than one-tenth of the population) COVID-19 pandemic has been linked to nearly were waiting for non-emergency medical care in 6.6 million deaths globally at the time of writing September 2022, while 10% of job posts remained noting that this 昀椀gure will likely increase with China’s vacant as the National Health Service struggled to 36 lifting of stringent COVID-19 restrictions after three retain staff. 33 years. In comparison, an estimated 4.95 million deaths were associated with drug-resistant bacteria Health systems are likely to face intensifying 昀椀nancial (AMR) in 2019 alone, with roughly 1.27 million of pressure – with budget cuts or revenue loss as well 34 these considered directly attributable to AMR. as higher costs of goods and labour – as in昀氀ation Air pollution was estimated to be responsible persists, economies grow slowly or stagnate, and for a further 9 million deaths in the same year, governments reprioritize expenditure to address 35 corresponding to one in six deaths worldwide. more salient social and security concerns. Even While there are limitations to the collection and before the COVID-19 pandemic aggravated staff analysis of data in all three cases, and COVID-19’s shortages, the World Health Organization (WHO) Global Risks Report 2023 36
predicted a global shortfall of 15 million health 37 workers by 2030. Some health systems are seeing productivity decline as experienced employees leave due to exhaustion, burnout and concerns about staff and patient safety. Skills and infrastructure gaps undermine capacity further as staff become overwhelmed by challenges for which they are not adequately equipped or supported to solve, leading to more strikes over pay and staf昀椀ng levels. Medical in昀氀ation is expected to continue to outstrip 38 GDP growth in many countries, and 昀椀nancial pressures on working populations will intensify as dependency ratios rise. The United States of America already spends nearly 20% of its GDP on healthcare, even before its largest population cohort (the “Baby Boomers”) has retired.39 Governments, insurers or employers may respond by limiting coverage and shifting a greater proportion of the costs to individuals, reducing access and affordability of healthcare. Two-tier health systems, already prevalent in many advanced and developing economies, may become further entrenched, with a pro昀椀table private sector catering to patients with greater ability and willingness to pay, while poorer environment, some of which could have unintended people remain reliant on increasingly threadbare compounding effects on speci昀椀c diseases. For 40 public provision. example, a lack of LGBTQ protection has been linked to poorer health outcomes relating to HIV, 43 A persistent mismatch between demand and supply due to the resulting avoidance of healthcare. gradually weakens the ability of health systems even Current crises might further derail health outcomes in richer countries to cope and adapt, eroding care and equity. Chronic 昀椀nancial stress and rationing quality and shrinking healthcare access. Fragile of essentials – such as having to choose between health systems could quickly become overwhelmed heating and eating – will have long-term physical 44 by one or more catastrophic events. A large-scale and psychological impacts even on healthy people. cyberattack, war, extreme weather event or new or Lower con昀椀dence in public institutions has already re-emergent infectious diseases could trigger health resulted in less effective pandemic responses, and system collapse within one or more regions, resulting growing misinformation and disinformation could in a sudden surge of deaths from all causes. More further increase vaccine hesitancy, which has gradual deterioration of health systems would also already led to the re-emergence of locally-eradicated 45 weaken overall health, widen health disparities, diseases such as polio. These patterns may be slow economic activity and undermine political and reinforced as there is a clear rise in the erosion societal stability as a safety net disintegrates. of social cohesion (see Chapter 1.2: Societal polarisation). Socioeconomic syndemics Geopolitical tensions could limit the co-development and sharing of new scienti昀椀c breakthroughs, limiting respective abilities to address ever-present Combined with fragile health systems, there is a risk risks such as AMR as well as new ones. Export of a rise in “syndemics”: a set of concurrent, mutually restrictions applied to medicine and medical enhancing health problems that impact the overall products could cause a humanitarian crisis and spiral health status of a population, within the context of into controls over even more existential resources – 41 political, structural or social environments. The most notably food – with compounding effects on concept has long been applied to HIV research. health. Disparities in healthcare access may also More recently, it has been considered in the context worsen across and within countries as a result of of the COVID-19 pandemic and chronic disease economic inequality. For example, while advances burdens, which have resulted in higher morbidity such as in personalized, genomic and proteomic and mortality rates among socially disadvantaged medicine can vastly improve health outcomes for 42 communities. A similar pattern could now play out chronic and degenerative conditions, they come with at a systemic level: deteriorating social, economic hefty price tags that may constrain widespread use; 46 and political contexts will contribute to endemic gene therapies can cost upwards of $2 million. A diseases and lead to poorer health outcomes for rise in state instability and con昀氀ict would further limit select communities. the delivery of aid, disrupt vaccination programmes and put health workers at risk. This was evident Inequality and con昀氀icts in societal values could in the case of polio vaccination workers killed in precipitate regulatory changes regarding education, Afghanistan last year.47 employment, housing, gender, immigration and the Global Risks Report 2023 37
In parallel, national and global health institutions Acting today and systems need to be strengthened in the face of multiple challenges. Innovation in care delivery, It is essential that we embed hard-earned lessons in staf昀椀ng and funding models are required for health preparedness for the next iteration of health crises. systems to provide disease prevention, early A continued focus on public health policy and detection and complex care cost-effectively for interventions can have outsized impacts at national an increasingly frail and chronically ill population. and regional levels, as a great deal of chronic There is also potential for healthcare to reap the 48 disease burden is, in fact, preventable. Realizing advantages of technological advances and digital public health gains will require governments and transformation that other sectors have embraced, business to promote the conditions that underpin such as augmenting capacity with technology and wellbeing and encourage healthy lifestyles, such combining virtual and in-person care to reduce as good food, clean air, secure housing and social costs. cohesion. Opportunities to strengthen public health exist Public health agencies, healthcare providers and across countries, too, especially in the areas of funders can play a key role by improving interactions pandemic surveillance and preparedness, scienti昀椀c and coordination between different parts of the collaboration, and in mitigating global threat drivers health system to share information, expand capacity such as climate change and AMR. It is essential and improve overall population health. Planning for that health nationalism is avoided in the face the long run will help governments better assess of the geopolitical and security considerations and manage health system risks, as will aligning already underway today. Continued collaboration policies that directly or indirectly affect health (such and information 昀氀ows in the 昀椀eld of healthcare, as agricultural policies that drive antibiotic use and pharmaceuticals and life sciences underpin efforts increase AMR risk). Governments and businesses to ensure that our understanding and capability can will also need to add a health dimension to crisis continue to effectively address emerging health risks. preparedness plans to withstand emerging risks. 2.4 Human security: new weapons, new con昀氀icts GRPS results suggest that economic and information clashes between global powers. Prior to 2022, warfare will continue to pose a more severe threat militarization had fallen in all regions, with recent than hot con昀氀ict over the next decade. Interstate data showing an overall decline in nearly 70% of the con昀氀ict and Use of weapons of mass destruction countries covered by the Global Peace Index 2022 49 were ranked lower in anticipated severity over the past 15 years. Even between 2021 and compared to “Geoeconomic confrontation” and 2022, the holdings of nuclear and heavy weapons, Misinformation and disinformation over the military expenditure, weapons imports and armed 10-year time frame (Figure 2.2). services personnel rates declined (Figure 2.6). Yet the world still became less peaceful, with more violent Past decades were de昀椀ned by the non-deployment demonstrations, external con昀氀ict and intense internal 50 of humanity’s most powerful weapons and no direct con昀氀icts during the same 昀椀fteen-year period. Global Risks Report 2023 38
FIGURE 2.6 Pre-2022 trends in militarization and conflict Nuclear and heavy weapons Deaths from external conflict Terrorism impact Military expernditure (% GDP) Incarceration rate Perception of criminality Weapons import Armed services personnel rate Violent demonstrations Police rate Homicide rate Internal conflicts fought External conflicts fought UN Peacekeeping funding Access to small arms Violent crime Political instability Refugees and IDPs Intensity of internal conflicts Neighbouring countries relations Intensity of internal conflicts Political terror scale Deaths from internal conflicts -6 -4 -2 0 +2 +4 +6 % Change in average score Source Note I EP, 2022. Percentage change in global score by indicator, 2021-2022. A reversal of the trend towards demilitarization will GDP, which, if met by all members, would represent 53 heighten the risk of con昀氀ict, on a potentially more an increase in total budget by 7% in real terms. destructive scale. Growing mistrust and suspicion Widespread defence spending, particularly on between global and regional powers has already research and development, could deepen insecurity led to the reprioritization of military expenditure and and promote a race between global and regional stagnation of non-proliferation mechanisms. The powers towards more advanced weaponry.54 diffusion of economic, technological and, therefore, military power to multiple countries and actors is The private sector is set to increasingly drive the driving the latest iteration of a global arms race. development of military technologies, yielding Unlike previous power dynamics that were shaped advancements in semiconductor manufacturing, by weapons of deterrence, the next decade could AI, quantum computing, biotechnology and even 55 be de昀椀ned by devastation from precision attacks and nuclear fusion, among other technologies. Many expanded con昀氀icts. of these are general purpose in nature with civilian applications, but are also a force multiplier of military power, enhancing the capabilities of autonomous New military architects and weapons, cyberwarfare and defensive capabilities. architecture Emerging technologies will be increasingly subject to state-imposed limits to cross-border 昀氀ows of talent, IP, data and underlying technologies (such The 2010s saw global military expenditure growing as extreme ultraviolet lithography equipment) and in line with GDP and government budgets (5% of resources (such as critical metals and minerals), 51 expenditure, down from 12% in the early 1990s). to constrain the comparative rise of foreign rivals. However, today, global military expenditure as Enhanced focus and investment will drive innovations proportion of GDP is rising, driven predominantly by – global research and development expenditure 56 higher spending by the United States of America, hit 2.63% in 2021, the highest in decades. There the Islamic Republic of Iran, Russia, India, China are sure to be multiple architects (Figure 2.7), with and Saudi Arabia. Japan announced a proposal to parallel innovations and interoperable ecosystems double its defence budget to $105 billion (2% of that will not only undermine ef昀椀ciencies and its GDP) in May last year, and Qatar has increased duplicate efforts – even prior to the tightening of spending by 434% since 2010 in response to market conditions, technological fragmentation was 52 blockades. The war in Ukraine – as well as estimated to result in losses of up to 5% GDP for lukewarm condemnation by a few key geopolitical many economies57 – but may also increase risk. players – has driven recent pledges by NATO members to meet or exceed the target of 2% of Military-driven innovations in relevant 昀椀elds will Global Risks Report 2023 39
FIGURE 2.7 Diffuse research and development 50 45 40 35 United States 30 25 China e of R&D investment (%)20 15 Relative shar10 Japan Germany 5 Korea France Russia 0 1990 1995 2000 2005 2010 2015 2020 Source Note Congressional Research Service, 2022.58 Share of Global R&D of selected economies, 2000-2020. Global R&D includes the expenditures of the OECD countries, Argentina, China, Romaina, Russia, Singapore, South Africa and Taiwan, China. Share computed in Purchasing Power Parity terms. 62 have knock-on bene昀椀ts for economic productivity some states. Directed Energy Weapons are and societal resilience, including personalized expected to make signi昀椀cant progress over the and preventative medicine, climate modelling and next decade, with the potential to disable satellites, material science development. The in昀氀uence of blocs electronics, communications and positioning will grow, closely tying together alliances across systems, and some of these weapons may be more 63 security, investment, trade, innovation, talent and cost-effective than traditional munitions. Quantum standards. For example, Australia, Japan, South computing may be harnessed to identify new Korea and New Zealand were recently invited to materials for use in stealth technologies, and cyber 59 participate at a NATO summit for the 昀椀rst time. and information warfare will be deployed to target As developing economies seek to enhance their vulnerabilities in increasingly sophisticated military security in the new military architecture, they will be technologies, which could range from disinformation pulled deeper into the wider economic and military campaigns to hacking hardware in nuclear defence 60 64 expansion of larger powers. However, the Global systems. South also risks being priced out of security and broader technological advancements. For example, Importantly, these technologies are emerging in the diffusion of dual-use technologies may be parallel – with the potential for simultaneous and 65 constrained or subject to high royalties, widening compounding impacts on global security. The global inequality. testing and demonstration of enhanced capabilities could destabilize geopolitical relationships and accelerate an arms race, even in the absence of Next-generation technologies and triggering conventional or nuclear strikes. This race multi-domain con昀氀icts will also slow the development of and adherence to norms, standards and safety protocols governing the development and use of these technologies, leaving New technologies will change the nature of the fundamental questions unanswered – such as how threat to national and international security, with a to pursue 昀椀elds like quantum computing, without rise in multi-domain con昀氀icts that blur the de昀椀nition simultaneously destabilizing the world’s encryption 66 of conventional warfare. “Future battle昀椀elds” systems and accelerating a global arms race. As a and methods of confrontation are expanding, result, self-regulation by the private sector will likely encompassing the land, sea, air, cyberspace rise, as will consumer campaigning against military and outer space (explored in the Crowding and applications of technologies, such as the “Stop Killer Competition in Space Chapter in last year’s Global Robots” coalition. 61 Risks Report). Anti-satellite and hypersonic weapon capabilities have already been demonstrated by While social and global norms constraining the use Global Risks Report 2023 40
of nuclear weaponry remain high, the unconstrained largest number of annual ballistic missiles launches pursuit of lower-yield weaponry and stronger last year, and there is escalating rhetoric in the 71 defensive military technologies could undermine the context of the war in Ukraine. The possibility of perceived security provided by nuclear weapons, nuclear-sharing arrangements or even potential putting in jeopardy a delicate strategic balance. acquisition in limited circumstances has been raised Emerging technologies heighten the actual or in some non-nuclear states, such as Japan and 72 perceived vulnerability of countries to attack, the South Korea. Negotiations on the revival of 67 including nuclear-armed ones. Advanced sensing the Joint Comprehensive Plan of Action (JCPOA) 73 technologies, particularly once enabled by quantum have also stalled. Although both the United computing, could theoretically expose second-strike States of America and Russia have continued to capabilities (mobile nuclear weapons) to real-time adhere to the New START Treaty, and disarmament 68 targeting and elimination. The potential for lower- technically continues, the usable military stockpiles yield, more targeted nuclear weaponry has already of both countries - accounting for 90% of all nuclear brought into question the viability of the current weapons - remained stable in 2021.74 threshold of activation for the “nuclear umbrella” of the United States of America. An escalating arms race may cause countries to roll back the no-昀椀rst- A rise in rogue actors use principle to enhance deterrence. Together, these new technologies are escalating Proliferation of more destructive and new-tech rhetoric and the pressure on existing governance military weaponry may enable newer forms of mechanisms. This could lead to an increase in asymmetric warfare, allowing smaller powers and the global inventory of nuclear warheads for the individuals to have a greater impact at a national and 昀椀rst time since the Cold War,69 raising the risk of global level. Financial, information and intelligence accidental, miscalculated or deliberate clashes, thresholds are lower in many dual-use technologies. with devastating results. Nuclear-armed countries For example, advances in biotechnologies could continue to modernize arsenals and develop new enable the creation of pathogens by small groups or types of delivery systems; late last year, the United even individuals.75 Low-cost drones utilizing swarm States of America unveiled its 昀椀rst new nuclear- intelligence can be used to attack high-value units, 76 capable strategic bomber in more than three including bases and fuel tanks. The most recent decades. The Treaty on the Prohibition of Nuclear available data suggests a consolidation of arms Weapons, which entered into force in early 2021, exports, with North America and Europe accounting continues to be opposed by all nine declared for 87% of all arms exports from 2017-2021, 70 nuclear-armed states. North Korea conducted the alongside an accompanying decline from China and FIGURE 2.8 Key drivers of interstate conflict Widespread cybercrime and cyber insecurity Interstate conflict Terrorist attacks Ineffectiveness of multilateral institutions Misinformation and disinformation Geoeconomic confrontation Use of weapons State collapse of mass destruction Reference Large-scale involuntary migration Erosion of social cohesion Natural resource crises Nodes EdgesEdges Risk influence Relative influence High High Medium Medium Low Low Risk categories Economic Environmental Geopolitical Societal Technological Source World Economic Forum, Global Risks Perception Survey 2022-2023. Global Risks Report 2023 41
Russia.77 However, any future diffusion of market with breakthroughs in dual-use technologies, most share will increase the likelihood of advanced military notably quantum computing. systems being shared with more adversaries, across 78 a broader geographic area. Acting today The lower cost and potential spread of conventional or chemical, biological, or nuclear weaponry to rogue An international environment that is at greater actors will further erode the government’s “monopoly risk of con昀氀ict and the less transparent attribution on violence". This can increase the vulnerability of of unconventional engagement may weaken the states and fuel migration, corruption and violence shared moral, reputational and political costs 79 that can spill over borders. Drones have already that partially act as a deterrent to the deployment been used by non-state actors in Syria, Libya and of destructive weaponry, including nuclear Yemen, and both military and civilian drones have engagement. Undoubtedly, the strengthening of been used by formal security forces, paramilitary arms control, disarmament and non-proliferation 80 groups and non-combatants in Ukraine. Despite agreements and norms, covering both existing and limited transparency and accountability, there has newer forms of military technologies, are essential also been a growing reliance on private militia and to provide transparency. This can also reduce the security services to protect assets and infrastructure, risk of unintended escalation, for example by limiting including vessels, commercial shipping, offshore the spillover of con昀氀icts across domains, such as platforms and ports. The use of these proxy, hybrid a cyberattack on critical infrastructure escalating and private armies in multiple security contexts into a targeted destructive exchange with lethal has been linked to violations of human rights autonomous weapons.83 Establishing norms will be and international law in con昀氀ict, post-con昀氀ict and essential to ensuring the right balance is struck so 81 peacetime settings. that technological innovation can continue to be harnessed to improve socioeconomic outcomes for The distinction between civilian and military spheres humanity. is blurring further: these technologies expose populations to direct domestic threats, often with However, achieving effective arms control will the objective of shattering societal functioning. be even more challenging than in the past. It will This includes the physical and virtual disruption require engagement with a broader range of actors of critical resources and services at both a local – including academic researchers and the private and national level, such as agriculture and water, sector – given the dual-usages of many of these 昀椀nancial systems, public security, transport, technologies. Developments are quickly outpacing energy, and domestic, space-based and undersea global governance processes. An escalating communication infrastructure. “Breakdown of arms race will further hinder collaboration, but the critical information infrastructure” was ranked regulation of new weapons technologies to control tied 16th by GRPS respondents in terms of proliferation and usage can only be achieved through perceived severity over the next 10 years, but transnational cooperation. The 昀椀rst step should its relationship with Interstate con昀氀ict was not include greater recognition by global powers of highlighted (Figure 2.8). Concerted attempts at the strategically bene昀椀cial value to agreements on cyberattacks against Ukraine were made last year, key arms control issues. In the longer term, new including against communication services, 昀椀nancial strategies for global governance that can adapt websites and electricity grids. Data theft and deep- to this new security context must be explored to fake technology also sought to prevent access to assuage the concerns of nations and avoid a spiral services, targeting 昀氀ows of refugees, medicines, of instability and accidental or intentional destruction. 82 food and relief supplies. The critical functioning of whole economies will only become more exposed 2.5 Digital rights: privacy in peril Digital tools - increasingly sophisticated AI applications, As highlighted in last year’s Global Risks Report chapter interoperable edge computing and Internet of Things ‘Digital Dependencies and Cyber Vulnerabilities’, (IOT) devices, autonomous technologies - underpin the malicious activity in cyberspace is growing, with more functioning of cities and critical infrastructure today and aggressive and sophisticated attacks taking advantage will play a key role in developing resilient solutions for of more widespread exposure. It was seen as a tomorrow’s crises. Yet these developments also give persistent threat by GRPS respondents as well as a rise to new challenges for states trying to manage the strong driver of other risks (Figure 2.9). existing physical world and this rapidly expanding digital domain. The proliferation of data-collecting devices and data- dependent AI technologies could open pathways Based on GRPS results, “Widespread cybercrime to new forms of control over individual autonomy. and cyber insecurity” is a new entrant into the top 10 Individuals are increasingly exposed to the misuse of rankings of the most severe risks over the next decade. personal data by the public and private sector alike, Global Risks Report 2023 42
FIGURE 2.9 Risk interconnections: cyber insecurity Adverse outcomes Widespread cybercrime of frontier technologies and cyber insecurity Digital power concentration Interstate conflict Digital inequality Terrorist attacks Misinformation and Breakdown of critical disinformation information infrastructure Reference Proliferation of illicit economic activity Nodes EdgesEdges Risk influence Relative influence High High Medium Medium Low Low Risk categories Economic Environmental Geopolitical Societal Technological Source World Economic Forum, Global Risks Perception Survey 2022-2023. ranging from discrimination of vulnerable populations sophisticated through new technologies and 84 and social control to potentially bioweaponry. techniques for gathering and analyzing data. The oft-cited examples are biometric identi昀椀cation Not all threats to the digital autonomy and technologies. In recognition of the potential risks sovereignty of individuals are malicious in nature. posed to privacy and the freedom of movement, Larger data sets and more sophisticated analysis some companies have self-regulated the sale of also heighten the risk of the misuse of personal facial recognition to law enforcement, and the use of information through legitimate legal mechanisms, this technology in public spaces faces an upcoming 85 88 weakening the human right to privacy, even ban in the EU. Concerns also extend to the use in democratic and strongly regulated regimes. of biometric technologies to analyze emotions. Legal incursions on privacy can be motivated by Other forms of monitoring are already becoming public safety considerations, crime prevention and commonplace. Automated AI-based tools such as response, economic development and better health chatbots collect a wide amount of personal data to outcomes. The privacy of personal and sensitive function effectively. The mass move to home working data is coming under increasing pressure by during the pandemic has led to tracking of workers national security concerns, combining the protection through cameras, keystroke monitoring, productivity of societies and states and the desire to gain a software and audio recordings – practices which are competitive technological and economic advantage. permitted under data-protection legislation in certain circumstances, but which collect deeper and more 89 sensitive data than previous mechanisms. Commercialized privacy More insidiously, the spread of networked data is increasing surveillance potential by a growing The right to privacy as it applies to information about number of both public- and private-sector actors, 90 individuals incorporates two key elements: the right despite stringent regulatory protection. As our not to be observed and the right to control the 昀氀ow lives become increasingly digitalized over the 86 of information when observed. As more data is next decade, our “everyday experience” will be collected and the power of emerging technologies recorded and commodi昀椀ed through internet-enabled increases over the next decade, individuals will be devices, more intelligent infrastructure and “smart” targeted and monitored by the public and private cities – a passive, pervasive and persistent form of sector to an unprecedented degree, often without networked observations that are already being used 87 91 adequate anonymity or consent. to create targeted pro昀椀les. This pattern will only be enhanced by the metaverse, which could collect Surveillance technologies are becoming increasingly and track even more sensitive data, including facial Global Risks Report 2023 43
expressions, gait, vital signs, brainwave patterns and companies, particularly as it relates to terrorist 92 vocal in昀氀ections. investigations, despite broader implications to the 104 ongoing security of civilians’ data. Individuals have usually consented to the collection of data for the associated bene昀椀cial use of the service Potential for misuse will be especially problematic or product, given the wave of new and stronger data for users residing in countries with poor digital 93 protection policies in many markets. However, as rights records, inadequate regulatory protection the collection, commercialization and sharing of data frameworks, or authoritarian tendencies. Forms grows, consent in one area may reveal far more than of digital repression to quell politically motivated intended when aggregated with other data points. uprisings, such as the use of spyware to track This is known as the “mosaic effect”, which gives rise activist activities, are already driving signi昀椀cant 105 to two key privacy risks: re-identi昀椀cation and attribute human rights violations in the Middle East. 94 disclosure. Research suggests that 99.98% of US Recent reports have also highlighted potential residents could be correctly re-identi昀椀ed in any data digital rights violations in Africa stemming from set – including those that are heavily sampled and the rapid expansion of biometric programmes 95 anonymized – using 15 demographic attributes. that include voter registration, CCTV with facial Researchers have used this theory to uncover the recognition, mandatory SIM card registration and 96 106 political preferences of streaming users, match refugee registration. As more emerging markets DNA from publicly-available research databases to look towards progressing their smart city plans, the 97 randomly selected individuals, and link medical collection of sensitive citizen data could expose billing records from an open data set to individual societies to additional peril if poorly governed and 98 107 patients. protected. In consequential terms, this means that an Security concerns posed by sensitive data and its international organization may share anonymized data potential abuse are well-recognized by governments. with partner governments to support effective and Countries have adopted more widespread data ef昀椀cient crisis responses. However, when combined localization policies, tightened regulation of with other data sets, it could allow the identi昀椀cation research collaborations, and banned some foreign- and tracking of vulnerable refugees and displaced owned companies from certain markets, including persons – or compromise the location of camps telecommunications, surveillance equipment and 99 and the supply chains of critical goods. Data on mobile applications, to limit the collection and 108 race, ethnicity, sexual orientation and immigration possession of sensitive data by non-allied states. status can be legally obtained in some markets Yet, less attention is being paid to the potential for and re-identi昀椀ed to varying degrees, enabling civil overreach and abuse of this data in the name of harassment and abuse. In one such example, the national security. The slow and legal erosion of the sexual orientation of a priest was obtained through digital sovereignty of individuals can have unintended the purchase of smartphone location data and and far-reaching consequences for social control and announced by a religious publication.100 the erosion of democracies – including, for example, by compromising freedom of the press. Data-enabled anocracies The right to privacy is not absolute; it is traded-off against government surveillance and preventative policing for the purposes of national security. However, the surveillance potential of data has meant that access to sensitive information can increasingly be obtained without due process or 101 transparency. In some cases, data protection laws that require consent effectively waive the legal protections against electronic surveillance of private 102 communications and location data. In the United States of America, data is aggregated and sold on the open market with limited regulatory restrictions, meaning enforcement agencies can purchase GPS location data without warrants or public disclosure.For example, theoretically, police could use automated licence plate data (obtained by both private- and public-sector organizations) to prosecute out-of-state abortions – leading Google to announce that it would auto-delete location 103 data for users that visit related centres. There is also increasing political and regulatory pressure to weaken encryption mechanisms adopted by private Global Risks Report 2023 44
Growing trade-offs between innovation and security Data is an important factor of production, and collection and 昀氀ows are essential to fuel innovation for enhanced economic productivity (including 109 automation), as well as socially bene昀椀cial uses. More expansive and innovative applications of AI and other emerging technologies will require cross-industry and public-private data aggregation. The centralization and consolidation of some types of data can lend a competitive advantage to economies, such as through improved health outcomes associated with advances in 110 biotechnology. Yet governments may also increasingly struggle to balance the potential harm of privacy loss against the bene昀椀ts of more rapid development of emerging technologies. At the same time, to address the growing concentration of data in the hands of a small number of private-sector companies, governments may increasingly push for open-data policies from both public- and private-sector sources, mirroring level will enable more effective, less complicated recent regulatory moves by the EU around data cross-border data-sharing mechanisms to power 111 spaces and marketplaces. Such policies – like the innovation while still ensuring adequate protection creation of public data trusts for research purposes for individuals. – will likely affect both domestic companies and industries, as well as allied countries. This may Developing a more globally consistent taxonomy, bene昀椀t more widespread and diffused innovation, data standards, and legal de昀椀nition of personal but it will also expand risks as they enable privacy and sensitive information is a key enabler. These breaches at a much larger scale. Privacy will frameworks should recognize that sensitivity can strongly in昀氀uence these agreements: the US rise from data-driven inferences that are enabled government recently committed to heightened by large data sets, the proliferation of online social safeguards for transatlantic data 昀氀ows, including networks, and the blurring of personal and industrial 112 from US intelligence activities. data in the roll-out of the IOT and implementation of 115 “smarter” cities. For example, one company was However, many of these data sets may still be recently 昀椀ned under the EU’s GDPR (General Data subject to the threat of re-identi昀椀cation, even Protection Regulation) for targeted advertising that with recent developments in privacy-enhancing inferred a medical condition (deemed as a special 116 technologies such as synthetic data, federated category of data) on the basis of purchase history. 113 learning and differential privacy. Research suggests that sensitive databases and technologies, Historically severe 昀椀nes for data loss are also such as pools of biological data and DNA helping change the cost-bene昀椀t assessment 114 sequencing, are already vulnerable to attack. around investment in cybersecurity measures, Sensitive health data is governed inconsistently but questions remain around the individual rights and the creation of large pools of personal data to action, damage and compensation in cases of 117 are creating lucrative targets for cybercriminals, breach. It will be incumbent on organizations to particularly given the less stable geopolitical consider the ethics of data collection and usage environment and limited norms currently governing to minimize reputational considerations beyond cyberwarfare. The potential consequences of the regulatory compliance. In addition, spurred by both large-scale theft of biometric or genomic information increased cyberattacks and tighter data laws, the are largely unknown but may allow for targeted voluntary disposal and destruction of personal data bioweaponry. may become a stronger priority – with potential environmental co-bene昀椀ts of minimizing data storage needs. Finally, governments will also need Acting today to development emergency capabilities to respond to data breaches and violation of privacy to minimize follow-on repercussions. At a national level, a patchwork of fragmented data policy regimes at local or state levels raises the risk of accidental and intentional abuses of data in a manner that was not considered by the individual’s original consent. Harmonizing policies at a national Global Risks Report 2023 45
2.6 Economic stability: global debt distress The threat of a sovereign debt crisis has been brewing, with public debt growing as interest rates have fallen. Governments have leveraged cheap money to invest in future growth and help stabilize distressed 昀椀nancial systems, providing massive 昀椀scal support during the pandemic and to shield households and businesses from the current cost- of-living crisis. However, high levels of debt may not be sustainable under tighter economic conditions. The rapid and widespread normalization of monetary policies, accompanied by a stronger US dollar and weaker risk sentiment, has already increased debt vulnerabilities that are likely to remain heightened for years. Stag昀氀ation on a global scale, combined with historically high levels of public debt, could have 118 vast consequences. Even with a softer landing, the consequences of debt-trap diplomacy and rockier restructuring raise the risk of debt distress – and even default – spreading to more systemically important markets, paralysing the global economic system. Further, even comparatively orderly 昀椀scal may exacerbate wage in昀氀ation – meaning there may consolidation is likely to impact spending on human need to be a material increase in unemployment to capital and development, ultimately threatening the contain consumer in昀氀ation. Extended supply-driven resilience of economies and societies in the face of in昀氀ation could drive more painful interest rate rises, the next global shock, whatever form it might take. even amidst a slowdown in growth, leading to a harder landing and more widespread debt distress. A more systemically important emerging and The rising price of debt developing economy – the likes of Mexico, South Africa and Poland – could face distress in coming 124 years, raising the risk of 昀椀nancial contagion. General government gross debt in advanced economies hit 112% of GDP in 2022, compared As cautioned by the International Monetary Fund to roughly 65% of GDP for emerging and (IMF), miscalibration between 昀椀scal and monetary 119 developing markets. Yet as identi昀椀ed in Chapter policies could exacerbate this further, and in 125 1.2, Economic downturn, some developing unexpected markets. Questions around the and emerging markets are feeling the impacts independence of central banks risk de-anchoring of tightening monetary policy and deteriorating market expectations, and monetary intervention economic conditions 昀椀rst and most acutely. For to counteract in昀氀ationary 昀椀scal policies will only example, Ghana recently reached an agreement with heighten the risk of longer economic malaise. The the IMF regarding a $3 billion bailout and Zambia is United Kingdom of Great Britain's near-crisis in seeking to conclude restructuring of $15 billion in September last year is an example of the potential external debt early this year. A broad-based global instability that could arise. The interest payable on 120 recession within the year could temper in昀氀ation the country's public debt is expected to hit £120.4 and cap interest rate rises, but there is a higher risk billion for the 昀椀nancial year ending March 2023, up 126 of balance-of-payments crisis in the short-term, from £69.9 billion, the highest on record. The Bank alongside a credit crunch over the mid to longer of England raised rates from 0.1% in December 121 term. Emerging market banks also hold a larger 2021 to 3.5% in December 2022, yet was forced proportion of domestic public debt, with the potential to intervene with an emergency quantitative easing for distress to spread to banks, households and programme in September to counter the market 122 pension funds. Larger emerging markets exhibiting reaction to the UK government’s proposed 昀椀scal 127 a heightened risk of default include Argentina, Egypt, stimulus. In the absence of a global shock, the 123 Ghana, Kenya, Tunisia, Pakistan and Türkiye. “veto power” of the markets will increasingly limit 128 昀椀scal expansion, even in advanced economies. Downside risks loom large, and another global shock could result in deeper and more prolonged economic disorder. Stag昀氀ation remains a severe risk for many The new geopolitics of debt economies. Current crises, such as the war in Ukraine and lingering impacts of COVID-19, are still impacting basic inputs, including labour, energy and For now, the ratio of defaulted versus total global food. Continued tightness in major labour markets public debt remains very low by historic standards Global Risks Report 2023 46
and far lower than peaks experienced in the 1980s other state creditors, as well as the private sector will (Figure 1.6). However, this partially re昀氀ects the continue to complicate attempts at restructuring. For growth in absolute public debt levels. Despite record example, only three countries – Chad, Ethiopia and IMF emergency lending and a $650 billion allocation Zambia – are currently undergoing treatment under 129 in special drawing rights, more than 54 countries the G20 Common Framework for Debt Treatments. are currently in need of debt relief, representing All remain unresolved, re昀氀ecting challenging less than 3% of the global economy. Yet these geopolitical and economic dynamics as well as a 131 countries represent 18% of the global population lack of transparency. and account for more than 50% of people living in 130 extreme poverty. Fears of contagion and further The call for wealthier economies to intervene capital 昀氀ight could weaken debt sustainability in a bilaterally is growing – likely increasing longer-term growing number of lower-income countries. The geopolitical tensions. China has become a large scale of debt defaults will in昀氀uence the depth of bilateral creditor to many low-income countries available restructuring, with some creditor countries and, by some estimates, has become the largest 132 hesitant to bail out distressed states on suf昀椀ciently of昀椀cial creditor globally. Energy exporters, such as concessionary terms, due to their own tightening the Middle East and the United States of America, 昀椀scal space and rising domestic needs. There may are also well-placed to step into the gap over the also be a shift away from overseas development medium-term. Renewed soft power approaches assistance towards loans to continue to support and debt-trap diplomacy could redraw regional development and wield economic power. This has and global political lines, driving currency blocs a lower domestic cost but exacerbates the debt and possibly exacerbating pressures on developing burden on these markets and increases the risk of a countries as supply chains shift to mirror economic larger wave of defaults in the future. alliances.133 This trend could also destabilize security dynamics, as debt is leveraged to pull developing It is not only the scale but the complexity of potential economies into the military expansion of larger debt restructuring and need for global cooperation powers (see Chapter 2.4: Human security). that will determine the extent to which defaults can be contained (Figure 2.10). Creditors have expanded Yet as the number of sovereign defaults grow, to include quasi-sovereign entities and the private creditor countries and companies could become sector, such as commodity traders and producers. more exposed to debt contagion, including Although this expansion has provided new avenues systemically important banks, pension funds and of 昀椀nancing, the coordination of relief between state creditors. This will interact with other domestic international organizations, the “Paris Club” and debt vulnerabilities, including the private sector FIGURE 2.10 The composition of public debt A. Bilateral general government debt 180B Other Bilateral 160B India Saudi Arabia 140B 120B 100B China 80B US$ (billions) 60B 40B Paris Club 20B 0 1980 1985 1990 1995 2000 2005 2010 2015 2020 Source Note World Bank, International Debt Statistics database.134 Bilateral Government Debt for 68 of the 72 Debt Service Suspension Initiative (DSSI) countries by creditor. Global Risks Report 2023 47
FIGURE 2.10 The composition of public debt B. General government debt 300B 250B Multilateral 200B 150B US$ (billions) Bilateral, excluding 100B China China Private creditors, 50B bonds Private creditors, banks Private creditors, 0 others 1980 1985 1990 1995 2000 2005 2010 2015 2020 Source Note World Bank, International Debt Statistics database.134 General Government Debt for 68 of the 72 Debt Service Suspension Initiative (DSSI) countries by creditor type. 135 and state-owned entities, to raise aggregate from the areas of greatest social need, including exposure and place pressure on the solvency of expenditure in public goods and infrastructure. even advanced and large emerging economies. A Beyond the growing 昀椀nancial cost of natural sovereign debt default in a systemically important disasters, emerging and developing economies will economy could result in systemic proliferation with a need to spend a higher proportion of GDP on the devastating impact on a global scale. green transition and sustainable infrastructure, with knock-on rami昀椀cations for other public spending 137 and services. By contrast, within the limits of A looming investment shortfall in昀氀ationary pressures, advanced economies can continue to leverage more accessible 昀椀nancing for economic development, such as stronger industrial Even in the absence of a global crisis, the 1980s policy, to underpin the energy transition, widening “lost decade” of development in Latin America and the divide between countries. Necessary 昀椀scal Sub-Saharan Africa provides a very real example of consolidation in emerging and developing economies the economic and humanitarian crisis that can arise may also rely heavily on spending cuts, which from a sovereign debt default, including currency could rapidly remove social protection available to free falls, collapses in output, cost-of-living crises low-income and vulnerable populations, increasing and rapid increases in poverty. The 41 countries poverty and inequality within countries, alongside that defaulted on their debt in the 昀椀rst half of the social and political unrest. decade required eight years, on average, to reach 136 their pre-crisis GDP per capita. Debt distress and Yet in a structurally different low-growth, low- restructuring will also have an impact on investment. investment economic era, even advanced economies According to GRPS results, the risk of Debt crises will need to make trade-offs. Rising unemployment, drops in perceived severity over the longer-term social unrest and political polarization, and even time frame, but the Collapse or lack of public technologically-driven churn in both blue- and white- infrastructure and services becomes more severe. collar jobs may in昀氀uence the prioritization of current The ability to 昀椀nance continued productivity and expenditure over longer-term capital expenditure, resilience will be hampered by economic and political while security considerations may mean there is dynamics on both a global and national level. less 昀椀scal headroom for social and environmental development over the medium term. The potential Advanced economies will have more autonomy result is the de-prioritization of investment and slow to invest in future priorities, while developing decay of public infrastructure and services in both 138 markets may be more beholden to the demands developing and advanced markets. Around two- of the creditor, meaning money could be diverted 昀椀fths of low- and lower-middle-income countries Global Risks Report 2023 48
cut expenditure on education by an average of increased deployment of debt-for-development deals 13.5% since 2020, which, despite a minor rebound, (see Chapter 2.2: Natural ecosystems), particularly 139 fell again in 2022. As referenced in Chapter 2: relating to climate-positive adaptation, to help break Human health, the lingering economic, educational the correlation between exposure to climate change 141 and healthcare overhang of the pandemic continues and debt vulnerability. However, this should not to weaken the capacity of public systems that also just be limited to environmental concerns. Social face compounding pressure from ageing populations bond issuances have already jumped sevenfold, to in advanced economies, and rapidly expanding $148 billion in 2022, targeting healthcare, education 142 populations in some developing markets. This is a and small and medium-sized enterprises. While slow-burning risk: impacts are subtle, lagged and debt swaps may not create 昀椀scal space beyond the cumulative in nature, but can be highly corrosive in speci昀椀c objective, SDG-linked conditionality may overall impact to the strength of human capital and enhance the willingness of creditors to consider debt development – a critical mitigant to the impact and relief, particularly for countries where other forms of likelihood of other global risks. 昀椀scal support, including write-downs and conditional grants, may be less likely.143 Acting today Finally, we are unlikely to be able to double down on debt to the same extent to cushion the next crisis. A more proactive approach to countries that are not In recognition of the risks posed to broader 昀椀nancial yet on the verge of debt distress could help mitigate stability, timely and deeper debt write-downs could the systemic risk of sovereign debt contagion. allow a faster return to developmental progress for Recognition of simultaneous crises – debt, climate vulnerable countries and render a future default less impacts and food security – could be integrated likely. The private sector could be incentivized to into greater 昀氀exibility and more concessional forms participate in debt restructuring through a variety of 昀椀nancing available to vulnerable markets. With of mechanisms, including issuing of new bonds particular respect to the climate agenda, there is with stronger legal protections, loss reinstatement a growing expectation that packages will include commitments and value recovery instruments – with grants, rather than rely solely on loans that add to 144 the latter enabling private creditors to gain from overall debt burdens. Bilateral and multilateral upside developments in debtor countries in the underwriting of risk could also enable much-needed future, such as GDP-linked instruments in Costa 昀氀ows of private capital, while support for longer-term 140 Rica, Argentina, Greece and Ukraine. projects that can help crowd-in private capital, such as the IMF’s Resilience and Sustainability Trust, is 145 As a complementary mechanism to more also critical. comprehensive debt restructuring, there may be Global Risks Report 2023 49
Endnotes 1. Intergovernmental Science-Policy Platform on Biodiversity and Ecosystem Services (IPBES), The global assessment report on biodiversity and ecosystem services, 2019, https://ipbes.net/sites/default/ 昀椀les/2020-02/ipbes_global_assessment_report_summary_for_policymakers_en.pdf. 2. Surminski, Swenja, Claudio Saf昀椀oti and Sumer Drall, “Embracing Nature: How Businesses Can Engage with New Environmental Imperatives”, Marsh McLennan, 27 September 2022, https://www.marshmclennan. com/content/dam/mmc-web/insights/publications/2022/september/Marsh%20McLennan%20 Embracing%20Nature_Sep27.pdf. 3. World Wildlife Foundation (WWF), Living Planet Report 2022: Building a nature-positive society, 2022, https://ww昀氀pr.awsassets.panda.org/downloads/lpr_2022_full_report.pdf; Habibullah, Muzafar Shah, Badariah Haji Din, Siow-Hooi Tan and Hasan Zahid, “Impact of climate change on biodiversity loss: global evidence”, Environmental Science and Pollution Research, vol. 9, 3 August 2021, pp. 1073-1081. 4. World Wildlife Foundation (WWF), Living Planet Report 2022: Building a nature-positive society, 2022, https://ww昀氀pr.awsassets.panda.org/downloads/lpr_2022_full_report.pdf. 5. Pörtner, Hans-Otto (Ed.), et al., Climate Change 2022: Impacts, Adaptation and Vulnerability, Intergovernmental Panel on Climate Change (IPCC), 2022, https://www.ipcc.ch/report/ar6/wg2/. 6. Ibid. 7. Over one-昀椀fth of the total buffer pool has been depleted in less than a decade. See: Badgley, Grayson, et. al, “California’s forest carbon offsets buffer pool is severely undercapitalized”, Frontiers in Forests and Global Change, 5 August 2022. 8. Gatti, Luciana V,. et al., “Amazonia as a carbon source linked to deforestation and climate change”, Nature, vol. 595, 2021, pp. 388-393; World Meteorological Organization, Greenhouse Gas Bulletin, 2022; Hook, Leslie and Chris Campbell, “Methane hunters: what explains the surge in the potent greenhouse gases?”, Financial Times, 23 August 2022. 9. World Wildlife Foundation (WWF), Living Planet Report 2022: Building a nature-positive society, 2022, https://ww昀氀pr.awsassets.panda.org/downloads/lpr_2022_full_report.pdf. 10. Kenneth Research, Vertical Farming Market Analysis 2022-2033, 31 October 2022. 11. Weidner, Till, “A holistic look at vertical farming’s carbon footprint and land use”, Agritecture, 9 May 2022. https://www.agritecture.com/blog/2022/5/9/a-holistic-look-at-vertical-farmings-carbon-footprint-and-land- use; Weidner, Till, Aidon Yang, Florian Forster and Michael W. Hamm, “Regional conditions shape the food- energy-land nexus of low-carbon indoor farming”, Nature Food, vol. 3, 2022, pp. 206-216, https://www. nature.com/articles/s43016-022-00461-7. 12. Lambin, Eric F. and Patrick Meyfroidt, “Global Land Use Change, Economic Globalization, and the Looming Land Scarcity”, Proceedings of the National Academy of Sciences 108, vol. 9, 2011, pp. 3465–3472, https://doi.org/10.1073/pnas.1100480108. 13. Tilman, David, Michael Clark, David R. Williams, Kaitlin Kimmel, Stephen Polasky and Craig Packer, “Future Threats to Biodiversity and Pathways to Their Prevention”, Nature, vol. 546, no. 7656, 2017, pp. 73–81, https://doi.org/10.1038/nature22900. 14. White, Natasha, “Debt-for-Nature swaps gain traction among developing countries”, Bloomberg, 7 November 2022, https://www.bloomberg.com/news/articles/2022-11-07/debt-for-nature-swaps-offer- option-for-developing-countries?leadSource=uverify%20wall. 15. Baldwin, Clare, Marc Jones and Simon Jesspo, “Bankers bet billions on new wave of debt-for-nature deals”, Reuters, 17 November 2022, https://www.reuters.com/business/cop/bankers-bet-billions-new- wave-debt-for-nature-deals-2022-11-17/. 16. Karlsruher Institut für Technologie. “Trade-off between biodiversity and food security in land use”, Science Daily, 18 February 2022, https://www.sciencedaily.com/releases/2022/02/220218100712.htm. 17. Tzay, José Francisco Calí, “Indigenous Peoples Still Suffer from Poverty, Climate Change and Loss of Ancestral Lands, Delegates Highlight in Third Committee”, United Nations General Assembly Seventy- Seventh Session, 16th Meeting, New York, 12 October 2022, https://press.un.org/en/2022/gashc4350. doc.htm. 18. FAO Commission on Genetic Resources for Food and Agriculture, Biodiversity for Food and Agriculture, 2019, https://www.fao.org/state-of-biodiversity-for-food-agriculture/en/,. 19. Gasparatos, Alexandros, et al., “Renewable energy and biodiversity: Implications for transitioning to a Green Economy”, Renewable and Sustainable Energy Reviews, vol. 70, 2017, pp 161-184, https://www. sciencedirect.com/science/article/pii/S1364032116304622#s0060. 20. Kang, Dake, Victoria Milko and Lori Hinnant, “'The Sacri昀椀ce Zone': Myanmar bears cost of green energy”, AP News, 9 August 2022, https://apnews.com/article/technology-forests-myanmar-75df22e8d7431a675 7ea4a426fbde94c; UN Environment Programme (UNDEP), Can the Democratic Republic of the Congo’s mineral resources provide a pathway to peace?, 20 September 2022; Global Witness, Myanmar’s poisoned mountains, 9 August 2022, https://www.globalwitness.org/en/campaigns/natural-resource-governance/ myanmars-poisoned-mountains/. Global Risks Report 2023 50
Endnotes 21. Marsh, René, “Billionaires are funding a massive treasure hunt in Greenland as ice vanishes”, CNN, 8 August 2022, https://edition.cnn.com/2022/08/08/world/greenland-melting-mineral-mining-climate/index. html; Pearce, Fred, “Why the rush to mine lithium could dry up the High Andes”, Yale Environment 360, 19 September 2022, https://e360.yale.edu/features/lithium-mining-water-andes-argentina. 22. Miller, K. A., et al., “Challenging the Need for Deep Seabed Mining From the Perspective of Metal Demand, Biodiversity, Ecosystems Services, and Bene昀椀t Sharing”, Frontiers in Marine Science, 29 July 2021, https:// www.frontiersin.org/articles/10.3389/fmars.2021.706161/full. 23. IPCC, Climate Change 2021: The Physical Science Basis, 2021, https://report.ipcc.ch/ar6/wg1/IPCC_ AR6_WGI_FullReport.pdf. 24. Trisos, Christopher, et al., “Potentially dangerous consequences for biodiversity of solar geoengineering implementation and termination”, Nature Ecology & Evolution, vol. 2, 2018, pp. 475-482; Innovative Genomics Institute, Supercharging Plants and Soils to Remove Carbon from the Atmosphere, 14 June 2022; Gibbens, Sarah, “Activists fear a new threat to biodiversity – renewable energy”, National Geographic, 26 May 2022; Gasparatos, Alexandros, et al., “Renewable energy and biodiversity: Implications for transitioning to a Green Economy”, Renewable and Sustainable Energy Reviews, vol. 70, 2017, pp. 161- 184; Sovacool, Benjamin K., Chad Baum and Sean Low, “Risk-risk governance in a low-carbon future: Exploring institutional, technological, and behavioural tradeoffs in climate geoengineering pathways”, Risk Analysis, 4 May 2022, https://onlinelibrary.wiley.com/doi/10.1111/risa.13932; Parker, Andy and Peter Irvine, “The Risk of Termination Shock from Solar Geoengineering”, Earth’s Future, 11 March 2018, https://agupubs.onlinelibrary.wiley.com/doi/full/10.1002/2017EF000735; Carlson, Colin J., et. al., “Solar geoengineering could redistribute malaria risk in developing countries”, Nature Communications, vol. 13, 20 April 2022, https://www.nature.com/articles/s41467-022-29613-w. 25. Abulu, Latoya, “On Indigenous Peoples’ Day, 昀椀ve inspirational conservation stories in the US”, Mongabay, 10 October 2022, https://news.mongabay.com/2022/10/on-indigenous-people-day-昀椀ve-inspirational- nature-conservation-stories/. 26. Hariharan, Kavitha, Adrienne Cernigoi, and Jordan Lee, “Life support: A people prescription for resilient health systems", Marsh McLennan, November 2022, https://www.marshmclennan.com/insights/ publications/2022/november/life-support-a-people-prescription-for-resilient-health-systems.html. 27. Erinoso, Olufemi, “Post-COVID-19 condition: current evidence and unanswered questions”, The Lancet, vol. 10, iss. 9, September 2022; David M., “The Economic Cost of Long COVID: An Update”, Harvard University, 16 July 2022, https://scholar.harvard.edu/cutler/news/long-covid,; Mirin, Arthur A., “A preliminary estimate of the economic impact of long COVID in the United States”, Fatigue: Biomedicine, Health & Behaviour, vol. 10, iss. 4, 17 July 2022, pp. 190-199, https://www.tandfonline.com/doi/abs/10.1080/216 41846.2022.2124064; Black, Euan, “Long COVID-19 costing Australia $100m a week”, Financial Review, 9 September 2022, https://www.afr.com/work-and-careers/workplace/long-covid-19-costing-australia- 100m-a-week-20220909-p5bgq1. 28. World Health Organization (WHO), Tuberculosis deaths and disease increase during the COVID-19 pandemic, [Press release], 27 October 2022, https://www.who.int/news/item/27-10-2022-tuberculosis- deaths-and-disease-increase-during-the-covid-19-pandemic. 29. Chumakov K, E. Ehrenfeld, V.I. Agol and E. Wimmer, “Polio eradication: falling at the 昀椀nal hurdle?”, The Lancet, 1 October 2022. 30. Romanello, Marina, et al., “The 2022 report of the Lancet Countdown on health and climate change: health at the mercy of fossil fuels”, The Lancet, vol. 400, iss. 10363, 25 October 2022, pp. 1619-1654. 31. McKeever, Amy, “Why climate change is still the greatest threat to human health”, National Geographic, 9 September 2021, https://www.nationalgeographic.com/science/article/why-climate-change-is-still-the- greatest-threat-to-human-health. 32. Institute for Health Metrics and Evaluation (IHME), Global Burden of Disease Study 2019, https://ghdx. healthdata.org/gbd-2019, accessed 21 November 2022. 33. WHO, WHO Coronavirus (COVID-19) Dashboard, https://covid19.who.int/, accessed 21 November 2022; Mallapaty, Smriti, “China COVID wave could kill one million people, models predict”, Nature, 19 December 2022, https://www.nature.com/articles/d41586-022-04502-w. 34. Murray, C.J.L., “Global burden of bacterial antimicrobial resistance in 2019: a systematic analysis”, The Lancet, vol. 399, iss. 10325, 12 February 2022, pp. 629-655. 35. Fuller, Richard, et al., “Pollution and health: a progress update”, The Lancet Planetary Health, vol. 6, iss. 6, 17 May 2022. 36. Financial Times, Backlog Britain: How public-sector delays spiralled to record levels, 27 November 2022, https://www.ft.com/content/ffdbd69b-1c7e-4fb2-b10a-d62c644bb988. 37. See World Health Organization: https://www.who.int/health-topics/health-workforce#tab=tab_1. Accessed 28 November 2022. 38. Mercer, Global insurer report: MMB health trends 2023, https://www.mercer.com/our-thinking/health/ health-trends-report.html, 2022. Global Risks Report 2023 51
Endnotes 39. Statistica Research Department, U.S. health expenditure as percent of GDP 1960-2020, 1 December 2022, https://www.statista.com/statistics/184968/us-health-expenditure-as-percent-of-gdp-since-1960/. 40. Hariharan, Kavitha, Adrienne Cernigoi and Jordan Lee,"Life Support: A People Prescription for Resilient Health Systems", Marsh McLennan, 2022, https://www.marshmclennan.com/insights/publications/2022/ november/life-support-a-people-prescription-for-resilient-health-systems.html. 41. Singer, Merrill, “A dose of drugs, a touch of violence, a case of AIDS: conceptualising the SAVA syndemic”, Free Inquiry in Creative Sociology, vol. 24, no. 2, 1 May 1996. 42. McGowan, Victoria, “COVID-19 mortality and deprivation: a pandemic, syndemic and endemic health inequalities”, The Lancet Public Health, vol. 7, iss. 11, 1 November 2022; Mendenhall, Emily, Brandon A. Kohrt, Carmen H. Logie and Alexander Tsai, “Syndemics and clinical science”, Nature Medicine, vol. 28, 21 July 2022, pp. 1359-1362. 43. Schwartz, Sheree R., et al., "The immediate effect of the Same-Sex Marriage Prohibition Act on stigma, discrimination, and engagement on HIV prevention and treatment services in men who have sex with men in Nigeria: analysis of prospective data from the TRUST cohort”, The Lancet HIV, vol. 2, no. 7, 1 June 2015. 44. Marmot, Michael, “A generation of Britons face long-term illness from being cold and poor this winter”, The Guardian, 1 September 2022, https://www.theguardian.com/commentisfree/2022/sep/01/generation- britain-long-term-illness-cold-poor-winter-cost-of-living-crisis. 45. Lazarus, Jeffrey V., et. al., “Revisiting COVID-19 Vaccine Hesitancy around the World Using Data from 23 Countries in 2021”, Nature Communications, vol. 13, July 1, 2022. Bhanani, L. Y. and B. Franz, “A meta-analysis of COVID-19 vaccine attitudes and demographic characteristics in the United States”, Public Health, vol. 27, June 2022, pp 31-38. 46. Kuchler, Hannah,“Revolutionary Crispr gene editing speeds from lab to treatment room”, Financial Times, 19 August 2022, https://www.ft.com/content/e3c12117-190c-4fc9-9988-57eb9ab9de56. 47. United Nations, UN condemns brutal killing of eight polio workers in Afghanistan, 24 February 2022, https:// news.un.org/en/story/2022/02/1112612. 48. Institute for Health Metrics and Evaluation (IHME), The Lancet: Latest global disease estimates reveal perfect storm of rising chronic diseases and public health failures fuelling COVID-19 pandemic, 15 October 2020, https://www.healthdata.org/news-release/lancet-latest-global-disease-estimates-reveal-perfect- storm-rising-chronic-diseases-and. 49. Institute for Economics and Peace (IEP), Global Peace Index 2022: Measuring peace in a complex world, 2022, https://www.visionofhumanity.org/wp-content/uploads/2022/06/GPI-2022-web.pdf. 50. Ibid. 51. Ibid. 52. Mason, Ra, “Commentary: Japan’s Militarisation Gets a Boost from Ukraine War despite Paci昀椀st Constitution”, CNA, 17 May 2022, https://www.channelnewsasia.com/commentary/japan-increase-military- spending-paci昀椀st-constitution-ukraine-china-2687661; Stockholm International Peace Research Institute (SIPRI), World Military Expenditure Passes $2 Trillion for First Time, 25 April 2022, https://www.sipri.org/ media/press-release/2022/world-military-expenditure-passes-2-trillion-昀椀rst-time. 53. Institute for Economics and Peace (IEP), Global Peace Index 2022: Measuring peace in a complex world, 2022, https://www.visionofhumanity.org/wp-content/uploads/2022/06/GPI-2022-web.pdf. 54. Perlo-Freeman, Samuel, Rethinking Unconstrained Military Spending, United Nations Of昀椀ce for Disarmament Affairs, UNODA Occasional Papers, No. 35, April 2020. 55. Carafano, James Jay, “Rapid Advancements in Military Tech.” GIS Reports (blog), 19 January 2022, https:// www.gisreportsonline.com/r/military-technology/. 56. United Nations Education Scienti昀椀c Culture Organization (UNESCO), Launch of the 2022 Survey of Research and Experimental Development Statistics for SDG 9.5 [Press release], 6 September 2022, http:// uis.unesco.org/en/news/launch-2022-survey-research-and-experimental-development-statistics-sdg-9-5. 57. Cerdeiro, Diego, et al., “Sizing Up the Effects of Technological Decoupling”, International Monetary Fund, IMF Working Papers, 12 March 2021, https://www.imf.org/en/Publications/WP/Issues/2021/03/12/Sizing- Up-the-Effects-of-Technological-Decoupling-50125. 58. Congressional Research Service, Global Research and Development Expenditure: Fact Sheet, 14 September 2022, https://sgp.fas.org/crs/misc/R44283.pdf. 59. North Atlantic Treaty Organization (NATO), NATO leaders meet with key partners to address global challenges, Indo-Paci昀椀c partners participate in a NATO summit for the 昀椀rst time [Press release], 29 June 2022, https://www.nato.int/cps/en/natohq/news_197287.htm. 60. McCarthy, Simone, “China and Cambodia break ground at naval base in show of ‘iron-clad’ relations”, CNN, 9 June 2022, https://edition.cnn.com/2022/06/09/asia/china-cambodia-naval-base-military-intl-hnk/ index.html. 61. Muggah, Robert, “The war against Ukraine has reached outer space”, iPolitics, 17 March 2022, https:// www.ipolitics.ca/opinions/the-war-against-ukraine-has-reached-outer-space. Global Risks Report 2023 52
Endnotes 62. Howarth, Josh, “6 Military Technology Trends to Watch (2022-2025)”, Exploding Topics, 22 April 2022, https://explodingtopics.com/blog/military-technology-trends. 63. Congressional Research Service, Defense Primer: Directed Energy Weapons, 14 November 2022, https:// sgp.fas.org/crs/natsec/IF11882.pdf. 64. Kallenborn, Zachary, The role of electronic warfare, cyber and space capabilities in air littoral, Atlantic Council, 30 August 2022; Lewis, Patricia and Beyza Unal, “Cyberattacks on Missile Systems”, Chatham House, 2 July 2019; Dunn, Will, “Can nuclear weapons be hacked?”, The New Statesman, 7 May 2018. 65. Institute for Peace Research and Security Policy (IFSH), Negative Multiplicity: Forecasting the Future Impact of Emerging Technologies on International Stability and Human Security, 2022, https://ifsh.de/en/ publications/research-report/research-report-010. 66. Shoup, Timothy and August Leo Liljenberg, “Destruction Democratised”, Farsight, 1 November 2022, https://farsight.cifs.dk/destruction-democratised/. 67. European Commission, Changing security paradigm, 2022, https://knowledge4policy.ec.europa.eu/ changing-security-paradigm_en, accessed 31 October 2022; Gottemoeller, Rose, “The Case Against A New Arms Race: Nuclear Weapons Are Not The Future”, Foreign Affairs, 9 August 2022. 68. Gottemoeller, Rose, “The Case Against A New Arms Race: Nuclear Weapons Are Not The Future”, Foreign Affairs, 9 August 2022. 69. Stockholm International Peace Research Institute (SPIRI), SPIRI Yearbook 2022: Armaments, Disarmament and International Security, 13 June 2022; Grego, Laura, “A nuclear arms race is unavoidable without serious intervention”, Financial Times, 27 October 2022. 70. ICAN, States reaf昀椀rm support for Nuclear Weapons Ban Treaty at UN First Committee, 29 October 2022, https://www.icanw.org/people_and_structure. 71. The Nuclear Threat Initiative, The CNS North Korea Missile Test Database, https://www.nti.org/analysis/ articles/cns-north-korea-missile-test-database/, accessed 31 October 2022; Stockholm International Peace Research Institute (SPIRI), SPIRI Yearbook 2022: Armaments, Disarmament and International Security, 13 June 2022. 72. Dunn, Lewis A., The disarmament, arms control, and non-proliferation implications of the invasion of Ukraine: what next for reducing global nuclear dangers, United Nations Institute for Disarmament Research, 2022. 73. Vohra, Anchal, “The Post-Iran-Nuclear-Deal World Won’t Be Pretty”, Foreign Policy, 17 November 2022, https://foreignpolicy.com/2022/11/17/the-post-iran-nuclear-deal-world-wont-be-pretty/. 74. The decline in total number of nuclear weapons between 2021 and 2022 has been attributed to the dismantling of retired warheads. Institute for Economics and Peace, Global Peace Index 2022: Measuring peace in a complex world, 2022, https://www.visionofhumanity.org/wp-content/uploads/2022/06/GPI- 2022-web.pdf. 75. Shoup, Timothy and August Leo Liljenberg, “Destruction Democratised”, Farsight, 1 November 2022, https://farsight.cifs.dk/destruction-democratised/. 76. Zou, Bingun and Xingguang Peng, “A Bilateral Cooperative Strategy for Swarm Escort under the Attack of Aggressive Swarms”, Electronics, 8 November 2022. 77. Wezeman, Pieter D., Alexandra Kuimova and Siemon T. Wezeman, Trends in international arms transfers, 2021, Stockhom International Peace Research Institute (SIPRI), SPIRI Fact Sheet, March 2022, https:// www.sipri.org/sites/default/昀椀les/2022-03/fs_2203_at_2021.pdf. 78. European Commission, Developments and Forecasts on Changing Security Paradigm, 2022, https:// knowledge4policy.ec.europa.eu/foresight/topic/changing-security-paradigm/developments-and-forecasts- on-changing-security-paradigm_en, accessed 1 November 2022. 79. Morgan, Forrest E. and Raphael S. Cohen, Military Trends and the Future of Warfare: The Changing Global Environment and Its Implications for the US Air Force, RAND Corporation, 2020. 80. The Economist, Why Drones are Becoming Iran’s Weapons of Choice, 13 November 2021, https://www. economist.com/middle-east-and-africa/why-drones-are-becoming-irans-weapons-of-choice/21806199; Yousif, Elias, “Drone Warfare in Ukraine: Understanding the Landscape”, Stimson, 30 June 2022, https:// www.stimson.org/2022/drone-warfare-in-ukraine-understanding-the-landscape/. 81. United Nations, Rise in mercenary forces trigger ‘rampant’ human rights violations [Press release], 20 September 2022, https://news.un.org/en/story/2022/09/1127171; De Groot, Tom and Salvador Santino F. Regilme, Jr., “Private Military and Security Companies and The Militarisation of Humanitarianism”, Journal of Developing Societies, vol. 38, iss. 1, 25 December 2021. 82. Przetacznik, Jakub and Simona Tarpova, Brie昀椀ng: Russia’s war on Ukraine: Timeline of cyber-attacks, European Parliamentary Research Service, June 2022, https://www.europarl.europa.eu/RegData/etudes/ BRIE/2022/733549/EPRS_BRI(2022)733549_EN.pdf. 83. Moodie, Michael and Jerry Zhang, “Bolstering Arms Control in a Contested Geopolitical Environment”, Stimson, 31 October 2022. Global Risks Report 2023 53
Endnotes 84. Robbins, Sam and Chia-Shuo Tang, “How Asia’s Digital Governance Beacon Balances Data Privacy and the ‘Public Good’”, The Diplomat, 20 October 2022. 85. The right to privacy is enshrined by Article 12 of the Universal Declaration on Human Rights. 86. Sætra, Henrik Skaug, “Privacy as an aggregate public good”, Technology in Society, vol. 63, November 2020, https://www.sciencedirect.com/science/article/pii/S0160791X20310381. 87. Organisation for Economic Co-operation and Development (OECD), Enhancing access to and sharing of data: reconciling risks and bene昀椀ts for data re-use across societies, 2020, https://www.oecd-ilibrary.org/ sites/15c62f9c-en/index.html?itemId=/content/component/15c62f9c-en. 88. Goujard, Clothilde, “Europe edges closer to a ban on facial recognition”, Politico, 20 September 2022, https://www.politico.eu/article/europe-edges-closer-to-a-ban-on-facial-recognition/; Heilweil, Rebecca, “Big tech companies back away from selling facial recognition to police. That’s progress.”, Vox, 11 June 2020, https://www.vox.com/recode/2020/6/10/21287194/amazon-microsoft-ibm-facial-recognition-moratorium- police. 89. Information Commissioner’s Of昀椀ce, Employment practices: monitoring at work draft guidance, 12 October 2022. 90. Sætra, Henrik Skaug, “Privacy as an aggregate public good”, Technology in Society, vol. 63, November 2020, https://www.sciencedirect.com/science/article/pii/S0160791X20310381. 91. Cohen, Julie E., “What privacy is for”, Harvard Law Review, 20 May 2013; Taylor, L., L. Floridi and B. Van der Sloot, Group Privacy: New Challenges of Data Technologies, Springer, 2016; Taaffe, Ouida, “Will smart cities tilt the balance between data capture and personal privacy?”, Raconteur, 5 September 2022, https:// www.raconteur.net/technology/will-smart-cities-tilt-the-balance-between-data-capture-and-personal- privacy/. 92. European Data Protection Supervisor, Metaverse, https://edps.europa.eu/press-publications/publications/ techsonar/metaverse_en, accessed 29 November 2022. 93. Rahnama, Hossein and Alex Pentland, “The New Rules of Data Privacy”, Harvard Business Review, 25 February 2022. 94. Of昀椀ce of the Privacy Commissioner of Canada, Privacy Tech-Know blog: When what is old is new again – The reality of synthetic data, 12 October 2022, https://www.priv.gc.ca/en/blog/20221012/? id=7777-6-493564; Platzer, Michael, “AI-based re-Identi昀椀cation attacks – and how to protect against them”, Mostly AI, 22 April 2022, https://mostly.ai/blog/synthetic-data-protects-from-ai-based-re-identi昀椀cation- attacks/. 95. Rocher, Luc, Julien M. Hendrickx and Yves-Alexandre de Montjoye, “Estimating the success of re- identi昀椀cation in incomplete datasets using generative models”, Nature Communications, 2019, https:// www.nature.com/articles/s41467-019-10933-3. 96. Narayanan, Arvind and Vitaly Shmatikov, “Robust de-anonymization of large sparse datasets”, IEEE, 28 May 2008, https://ieeexplore.ieee.org/document/4531148. 97. Kolata, Gina, “Poking holes in genetic privacy”, The New York Times, 16 June 2013, https://www.nytimes. com/2013/06/18/science/poking-holes-in-the-privacy-of-dna.html. 98. Culnane, Chris, Benjamin I. P. Rubinstein and Vanessa Teague, “Health Data in an Open World”, Cornell University, 15 December 2017, https://arxiv.org/abs/1712.05627. 99. Capotosto, Jill, “The mosaic effect: the revelation risks of combining humanitarian and social protection data”, Humanitarian Law and Policy, 9 February 2021, https://blogs.icrc.org/law-and-policy/2021/02/09/ mosaic-effect-revelation-risks/. 100. NBC News, Priest outed via Grindr app highlights rampant data tracking, 22 July 2021, https://www. nbcnews.com/tech/security/priest-outed-grindr-app-highlights-rampant-data-tracking-rcna1493. 101. UNESCO, The right to privacy in a digital age: UNESCO’s inputs for the preparation of the thematic report of the Of昀椀ce of the United Nations High Commissioner for Human Rights, 2022, https://www.ohchr.org/ sites/default/昀椀les/documents/issues/digitalage/reportprivindigage2022/submissions/2022-09-06/CFI-RTP- UNESCO.pdf, accessed 3 November 2022. 102. McKenna, Anne Toomey, “Customer Data Can Be Used As Evidence in Government Surveillance”, Marsh McLennan, 13 November 2022, https://www.brinknews.com/customer-data-can-be-used-as-evidence-in- government-surveillance/. 103. Senate Finance Subcommittee on Fiscal Responsibility and Economic Growth, Testimony of Samm Sacks: Hearing on Promoting Competition, Growth and Privacy Protection in the Technology Sector, 7 December 2021; Sherman, Justin, “The Open Data Market and Risks to National Security”, Lawfare, 3 February 2022, https://www.lawfareblog.com/open-data-market-and-risks-national-security; Cadell, Cate, “China harvests masses of data on western targets, documents show”, The Washington Post, 31 December 2021 ; Benson, Thor, “The Danger of License Plate Readers in Post-Roe America”, WIRED, 7 July 2022; Grant, Nico, “Google Says It Will Delete Location Data When Users Visit Abortion Clinics”, The New York Times,1 July 2022. 104. Collins, Barry, “Mission Impossible: 7 Countries Tell Facebook to Break Encryption”, Forbes, 11 October 2020. Global Risks Report 2023 54
Endnotes 105. Silic, Anamaria, “Pegasus Spyware Used against Dozens of Activist Women in the Middle East”, The Intercept, January 18, 2022. https://theintercept.com/2022/01/18/pegasus-spyware-nso-group-women- activists-journalists/. 106. CIPESA, State of Internet Freedom in Africa 2022: The Rise of Biometric Surveillance, September 2022, http://104.152.168.205/~cipesa/old/?wpfb_dl=505. 107. Hoster, Ben, Swati Khurana and Rachel Juay, “Still Buffering: Time for a Smart City Reboot”, Marsh McLennan, October 2022, https://www.marshmclennan.com/insights/publications/2022/october/still- buffering-time-for-a-smart-city-reboot.html. 108. Das, Shanti and Vincent Ni, “Fears over China’s access to genetic data of UK citizens”, The Guardian, 20 August 2022; Needham, Kirsty and Clare Baldwin, “China’s gene giant harvests data from millions of women”, Reuters, 7 July 2021; Mallapaty, Smriti, “China expands control over genetic data used in scienti昀椀c research”, Nature, 6 May 2022. 109. Senate Finance Subcommittee on Fiscal Responsibility and Economic Growth, Testimony of Samm Sacks: Hearing on Promoting Competition, Growth and Privacy Protection in the Technology Sector, 7 December 2021; Senate Finance Subcommittee on Fiscal Responsibility and Economic Growth, Written Testimony of Stacey Gray, Senior Counsel, Future of Privacy Forum, 7 December 2021. 110. Robbins, Sam and Chia-Shuo Tang, “How Asia’s Digital Governance Beacon Balances Data Privacy and the ‘Public Good’”, The Diplomat, 20 October 2022. 111. European Parliament, Data governance: why is the EU data sharing law important?, 6 April 2022, https:// www.europarl.europa.eu/news/en/headlines/society/20220331STO26411/data-governance-why-is-the-eu- data-sharing-law-important. 112. US White House, Executive Order on Enhancing Safeguards for United States Signals Intelligence Activities, 7 October 2022. 113. Organisation for Economic Co-operation and Development (OECD), Enhancing access to and sharing of data: reconciling risks and bene昀椀ts for data re-use across societies, 2019, https://www.oecd-ilibrary. org/sites/15c62f9c-en/index.html?itemId=/content/component/15c62f9c-en; Of昀椀ce of the Privacy Commissioner of Canada, Privacy Tech-Know blog: Privacy Enhancing Technologies for Businesses, 12 April 2021, https://www.priv.gc.ca/en/blog/20210412/; Stadler, Theresa, Bristea Oprisanu and Carmela Troncoso, Synthetic Data – Anonymisation Groundhog Day, Cornell University, 24 January 2022, https:// arxiv.org/abs/2011.07018; Sei, Yuichi, Hiroshi Okumura and Akihiko Ohsuga, “Re-identi昀椀cation in differentially private incomplete datasets”, IEEE Open Journal of the Computer Society, vol. 3, 20 May 2022, https://ieeexplore.ieee.org/document/9779455. 114. Fayans, Iliya, et al., “Cyber security threats in the microbial genomics era: implications for public health”, Eurosurvellance, vol. 25, no. 6, 2020; Vinatzer, Boris A., et al., “Cyberbiosecurity Challenges of Pathogen Genome Databases”, Frontiers in Bioengineering and Biotechnology, vol. 7, 15 May 2019; Arshad, S., et al., “Analysis of security and privacy challenges for DNA-genomics applications and databases”, Journal of Biomedical Informatics, July 2021. 115. Saglam, Rahime Belene, Jason R.C. Nurse and Duncan Hodges, “Personal information: Perceptions, types and evolution”, Journal of Information Security and Applications, vol. 66, May 2022. 116. Information Commissioner’s Of昀椀ce, Catalogue retailer Easylife 昀椀nes £1.48 million for breaking data protection and electronic marketing laws, 6 October 2022, https://ico.org.uk/about-the-ico/media-centre/ news-and-blogs/2022/10/catalogue-retailer-easylife-昀椀ned-148-million/. 117. Marsh and Microsoft, “The State of Cyber Resilience 2022”, 2022, https://www.marsh.com/us/services/ cyber-risk/insights/the-state-of-cyber-resilience.html. 118. Roubini, Nouriel, “We’re Heading for a Stag昀氀ationary Crisis Unlike Anything We’ve Ever Seen”, TIME, 13 October 2022, https://time.com/6221771/stag昀氀ation-crisis-debt-nouriel-roubini/. 119. International Monetary Fund, General government gross debt: percent of GDP, https://www.imf.org/ external/datamapper/GGXWDG_NGDP@WEO/OEMDC/ADVEC/WEOWORLD, accessed 11 December 2022. 120. The World Bank. 2022. Risk of Global Recession in 2023 Rises Amid Simultaneous Rate Hikes. 15 September 2022. https://www.worldbank.org/en/news/press-release/2022/09/15/risk-of-global-recession- in-2023-rises-amid-simultaneous-rate-hikes 121. Ibid. 122. Pazarbasioglu, Ceyla and Carmen Reinhart, “Shining a light on debt”, International Monetary Fund (IMF). March 2022. https://www.imf.org/en/Publications/fandd/issues/2022/03/Shining-a-light-on-debt- Pazarbasioglu-Reinhart. 123. Subran, Ludovic, “Reverse Currency War Is Hitting Emerging Markets Hard”, South China Morning Post, October 20, 2022, https://www.scmp.com/comment/opinion/article/3196468/federal-reserves-in昀氀ation- 昀椀ght-leaves-emerging-markets-scrambling-answers. 124. Allianz, “Reverse currency war puts emerging markets at risk”, 29 September 2022, https://www. allianz-trade.com/en_global/news-insights/economic-insights/emerging-markets-debt-sustainability-risks. html. Global Risks Report 2023 55
Endnotes 125. Adrian, Tobias and Gaspar, Vitor. 2022. “How Fiscal Restraint Can Help Fight In昀氀ation”. IMF blog. 21 November 2022. 126. Government of the United Kingdom Of昀椀ce for National Statistics, Public sector 昀椀nances, UK: October 2022, 22 November 2022, https://www.ons.gov.uk/economy/governmentpublicsectorandtaxes/ publicsector昀椀nance/bulletins/publicsector昀椀nances/october2022; Government of the United Kingdom Of昀椀ce for National Statistics, Public sector 昀椀nances, UK: March 2022, 26 April 2022, https://www.ons.gov.uk/ economy/governmentpublicsectorandtaxes/publicsector昀椀nance/bulletins/publicsector昀椀nances/march2022. 127. Bank of England, Why have interest rates gone up?, 4 November 2022, https://www.bankofengland. co.uk/knowledgebank/why-are-interest-rates-in-the-uk-going-up#:~:text=On%203%20November%20 2022%2C%20we,loan%2C%20mortgage%20or%20savings%20account. 128. Carlsson-Szlezak, Philipp and Paul Swartz, “Why the market vetoed the UK’s budget – and what it means for the changing nature of stimulus around the world”, Fortune, 27 September 2022, https://fortune. com/2022/09/27/market-vetoed-uk-budget-truss-pound-changing-nature-stimulus-economy-carlsson- szlezak-swartz/. 129. Georgieva, Kristalina and Ceyla Pazarbasioglu, “The G20 Common Framework for Debt Treatments Must Be Stepped Up”, IMF blog, 2 December 2021, https://www.imf.org/en/Blogs/Articles/2021/12/02/ blog120221the-g20-common-framework-for-debt-treatments-must-be-stepped-up. 130. Jensen, Lars, Avoiding ‘Too Little Too Late’ on International Debt Relief, United Nations Development Programme (UNDP), UNDP Development Futures Series Working Papers, 11 October 2022, https://www. undp.org/publications/dfs-avoiding-too-little-too-late-international-debt-relief. 131. Ibid. 132. Ibid. 133. Sharma, Ruchir, “A post-dollar world is coming”, Financial Times, 28 August 2022, https://www.ft.com/ content/989b2e50-e8b5-474c-86a3-190c6881b235?desktop=true&segmentId=7c8f09b9-9b61-4fbb- 9430-9208a9e233c8#myft:noti昀椀cation:daily-email:content. 134. The World Bank, International Debt Statistics, https://databank.worldbank.org/source/international-debt- statistics, accessed 13 December 2022. 135. World Bank Group, World Development Report 2022: Finance for an Equitable Recovery, 2022, https:// www.worldbank.org/en/publication/wdr2022. 136. Ibid. 137. Wolf, Martin, “Delay only makes climate action more urgent”, Financial Times, 8 November 2022, https:// www.ft.com/content/5198e3ba-997f-4db5-8310-3a68ae91d9f2?emailId=153c65f9-db1b-495c-8385- 7912d487ef5c&segmentId=22011ee7-896a-8c4c-22a0-7603348b7f22. 138. World Bank Group, World Development Report 2022: Finance for an Equitable Recovery, 2022, https:// www.worldbank.org/en/publication/wdr2022. 139. The World Bank, Two-Thirds of Poorer Countries are Cutting Education Budgets Due to COVID-19 [Press release], 22 February 2021, https://www.worldbank.org/en/news/press-release/2021/02/22/two-thirds-of- poorer-countries-are-cutting-education-budgets-due-to-covid-19; The World Bank, Financing for Education Stagnant or Declining Despite Chronic Learning Needs Post-COVID-19 [Press release], 28 June 2022, https://www.worldbank.org/en/news/press-release/2022/06/28/昀椀nancing-for-education-stagnant-or- declining-despite-chronic-learning-needs-post-covid-19. 140. Lee, Nancy, “Restructuring Sovereign Debt to Private Creditors in Poor Countries: What’s Broken?”, Center for Global Development, 5 August 2020, https://www.cgdev.org/publication/restructuring-sovereign-debt- private-creditors-poor-countries-whats-broken. 141. Jensen, Lars, Avoiding ‘Too Little Too Late’ on International Debt Relief, United Nations Development Programme (UNDP), UNDP Development Futures Series Working Papers, 11 October 2022, https://www. undp.org/publications/dfs-avoiding-too-little-too-late-international-debt-relief. 142. World Bank Group, World Development Report 2022: Finance for an Equitable Recovery, 2022, https:// www.worldbank.org/en/publication/wdr2022. 143. Chamon, Marcos, Erik Klok, Vimal Thakoor and Jeromin Zettelmeyer, Debt-for-Climate Swaps: Analysis, Design, and Implementation, International Monetary Fund (IMF), IMF Working Papers, 12 August 2022, https://www.imf.org/en/Publications/WP/Issues/2022/08/11/Debt-for-Climate-Swaps-Analysis-Design-and- Implementation-522184. 144. Pilling, David, Joseph Cotterill and Camilla Hodgson, “South Africa warns $8.5bn climate package risks fuelling debt burden”, Financial Times, 4 November 2022, https://www.ft.com/content/ e6653b1d-2302-4e44-81bb-38dc608d303d?desktop=true&segmentId=7c8f09b9-9b61-4fbb-9430- 9208a9e233c8#myft:noti昀椀cation:daily-email:content. 145. Wolf, Martin, “Delay only makes climate action more urgent”, Financial Times, 8 November 2022, https:// www.ft.com/content/5198e3ba-997f-4db5-8310-3a68ae91d9f2?emailId=153c65f9-db1b-495c-8385- 7912d487ef5c&segmentId=22011ee7-896a-8c4c-22a0-7603348b7f22. Global Risks Report 2023 56
January 2023 Global Risks Report 2023 Resource Rivalries: Four Emerging Futures 3 Resource Rivalries: Four Emerging Futures 3.1 Anticipating “polycrises” Chapter one and Chapter two highlighted newly unexpected consequences. Bearing this in mind, emerging and rapidly accelerating risks over the this chapter explores how connections between the current, two- and 10-year time frame to provide emerging risks outlined in previous sections may analysis on risks currently unfolding or those that evolve by 2030. This year, we explore Resource may become the next global shock. However, these Rivalries - a potential cluster of interrelated present and future risks can also interact with each environmental, geopolitical and socioeconomic risks other to form a “polycrisis” – a cluster of related relating to the supply of and demand for natural global risks with compounding effects, such that the resources. The intent is not to exhaustively outline 1 overall impact exceeds the sum of each part. all scenarios but to provide a structured approach to identifying potential futures for the polycrisis that Scenario thinking can be a useful tool to enable may be triggered, providing a framework for better better anticipation of polycrises, as key drivers preparedness and risk mitigation efforts today. can interact in unanticipated ways and lead to 3.2 Polycrisis: natural resources, climate and cooperation A growing demand-supply gap for natural resources Supply-chain crises of recent years have highlighted the need for resilience in traditional strategic sectors. Reliable and cheap access to the most basic of necessities – food, water and energy – underpins the critical functioning of societies. Early data suggests that current crises are driving a worrying reversal of recent progress. An additional 200 million people faced acute food insecurity last year compared to 2019,and the number of people worldwide without electricity rose to an estimated 774 million, 2 the equivalent of pre-pandemic levels. As noted in Chapter 1.2, Cost-of-living crisis, supply crises of this nature can be highly destabilizing, exposing the fragility of states and leading to loss of life, widespread violence, political upheaval and involuntary migration. Demand for food, water and critical metals and minerals is escalating. This re昀氀ects a range of is projected to increase by 1.4% annually over the factors, including continued population growth, next decade, concentrated in low- to middle-income 3 anticipated to reach 8.5 billion by 2030, and countries, versus a 1.1% per annum increase in 4 socioeconomic advancement, with a push to achieve production. One estimate places the gap between the UN’s Sustainable Development Goals (SDGs) by water demand and supply at 40% by 2030, with a the target date of 2030. Global food consumption dramatic and unequal increase in demand between Global Risks Report 2023 57
5 countries. The continued expansion into secure, Together, the set of emerging demand and supply renewable energy and related infrastructure will also concerns around natural resources are already drive exponential demand for 昀椀nite critical metals and becoming an area of growing alarm. GRPS 6 minerals. Signi昀椀cant even in absolute terms, annual respondents identi昀椀ed strong relationships and two- demand for these resources, such as graphite, way linkages between “Natural resource crises” lithium and cobalt, is anticipated to hit 450% of 2018 and the other risks identi昀椀ed in previous chapters 7 production levels by 2050. (Figure 3.1), pointing to the potential polycrisis that may evolve over the medium term. FIGURE 3.1 Natural resource polycrisis Biodiversity loss and ecosystem collapse Failure to mitigate Natural resource crises climate change Environmental Failure of climate-change adaption damage incidents Natural disasters and extreme weather Reference Geoeconomic confrontation Interstate conflict Collapse of a systemically important supply chain Cost-of-living crisis Nodes EdgesEdges Risk influence Relative influence High High Medium Medium Low Low Risk categories Economic Environmental Geopolitical Societal Technological Source World Economic Forum, Global Risks Perception Survey 2022-2023. cannot be avoided. Persistently high commodity Cooperation and climate as key forces for disruption prices slow climate mitigation – despite ambitions – and add to in昀氀ationary pressures in broader value chains, while water stress leads to a In the 2030 time frame, two critical factors will growing, but comparatively contained, health and determine the trajectory of our ability to match humanitarian crisis in developing nations. supply and demand for these resources as well as the scale of the associated polycrisis: 1) the • Resource constraints – the danger of degree of global cooperation that allows the 昀氀ow of divergent distress: current crises draw focus resources across national borders, and 2) the impact and slow climate action, exposing the most of climate change on the supply of natural resources vulnerable countries to hunger and energy and speed of the low-carbon transition (Box 3.1). shocks, even as countries cooperate to partially address constraints. In the absence of Together, these two axes lead to four hypothetical intervention, the water and mineral shortages futures for 2030: experienced in the Resource collaboration scenario act as a multiplier to broader risks. A • Resource collaboration – the danger of multi-resource, humanitarian crisis emerges in natural scarcity: effective climate action developing markets as food and water resources measures and 昀氀exible supply chains enabled by are impacted by the physical consequences of global cooperation largely absorb the impacts climate change, alongside global disruptions to of climate change on food production. However, trade, political stability and economic growth. shortages in water and metals and minerals Global Risks Report 2023 58
• Resource competition – the danger of geopolitical dynamics exacerbate climate- resource autarkies: distrust drives a push induced shortages in food and water. This for self-suf昀椀ciency in high-income countries, results in a truly global, multi-resource crisis, with limiting the need for rivalry over food and water widespread socioeconomic impacts that exceed to a degree, but widening divides between those faced in other futures in both scope countries. State intervention is centred on the and scale, including famine and water scarcity resource most exposed to a concentration in refugees. Geoeconomic warfare is widespread, supply – critical metals and minerals – leading but more aggressive clashes between states to shortages, price wars and the transformation become one of the few means to ensure supply of business models across industries. Resource of basic necessities for populations. power shifts, driving the formation of new blocs as well as wedges in existing alliances between Given the nature of the polycrisis in each scenario, mineral-rich and -poor countries, while the we face various environmental and socioeconomic potential for accidental or intentional con昀氀ict upsides and downsides. The following section escalates. outlines an illustrative, but non-exhaustive set of mid- term futures to help support business leaders and • Resource control – the danger of resource policy-makers in preparing for – and preventing – the wars: alongside the weaponization of metals and progression of the crises we are facing today. minerals explored in Resource competition, BOX 1 Futures framework FIGURE 3.2FIGURE 3.2 Natural rNatural resouresource polycrisis: ce polycrisis: other climate mitigation efforts as well as more futurfutures frameworkes framework rapid adaptation. Accelerated climate actionAccelerated climate action • Slow climate action: trade-offs between environmental, social and security goals slow the prioritization of attention and resources to address climate change. By 2030, there ResourResourcece ResourResourcece Geoeconomic cooperationGeoeconomic cooperation competitioncompetition collaborationcollaboration has been insuf昀椀cient or ineffective progress ontationontation towards the adaptation support required to protect infrastructure and populations from changing climactic conditions. Paired with relatively slow efforts at mitigation, this has Geoeconomic confrGeoeconomic confrResourResourcece ResourResourcece resulted in continued damage to natural contrcontrolol constraintsconstraints ecosystems and an increasing 昀椀nancial and humanitarian impact. Slow climate actionSlow climate action In parallel, the intensity of the demand-supply gap SourSourccee in natural resources will re昀氀ect the mechanisms Global Global Risks Risks Report Report 2023.2023. by which states look to boost security in key resources. We consider the extent to which We use two global drivers – geoeconomic the evolution of Geoeconomic confrontation, confrontation and speed of climate action – highlighted in Chapter 1.2, Economic warfare, to create four futures we may face by 2030, could create conditions of scarcity, by considering considering potential implications based on the two ends of a continuum (x-axis): evolution of these risks and their interactions (Figure 3.2). • Geoeconomic cooperation: characterized by open dialogue and broadscale, but not always First, we explore the potential risks of a failure of successful, economic and trade collaboration climate-change adaptation and failure of climate between powers through relevant bilateral and mitigation efforts, described in Chapter 1.2, multilateral mechanisms and forums. Well- Climate action hiatus, and the extent to which established principles governing trade policies these failures could result in conditions of scarcity, and state aid are respected. on a continuum (y-axis): • Geoeconomic confrontation: direct and • Accelerated climate action: climate action indirect clashes between global and regional and associated funding and innovation are powers through the extensive exercise of hard prioritized. By 2030, we see persistently or soft economic, industrial and technological expanding but largely well-managed impacts of power. There is limited collaboration on global climate change, nature loss, natural disasters economic and trade issues and a breakdown and extreme weather events at a global level, or paralysis of mechanisms of cooperation, as alongside a more rapid energy transition and well as alliances. Global Risks Report 2023 59
3.3 Four futures for 2030 Risks remain: some natural resources are scarce, Resource collaboration – even in a climate-adapted, geopolitically cooperative the danger of natural scarcity world. Demand for geographically concentrated critical metals and minerals has risen dramatically, re昀氀ecting a push for secure, renewable energy Accelerated climate action sources in the wake of the war in Ukraine, and renewed urgency of net-zero ambitions over recent Resource Resource Geoeconomic cooperationyears. Despite suf昀椀cient resource deposits in most competition collaboration 9 minerals, this exponential increase in demand has ontation proved dif昀椀cult to meet through a rapid expansion of supply. Shortages initially stemmed from limited exploration and signi昀椀cant capital requirements, Geoeconomic confrResourceResource control constraints but the rise in commodity prices have subsequently helped to scale production, with companies now Slow climate action targeting deposits previously deemed unextractable for economic or technological reasons. By 2030, the world is subject to more widespread However, shortages in key materials remain a near- and dramatic climate impacts – but we are prepared. and mid-term concern, given time lags to production. Capital, intellectual property and technological Further, environmental concerns have limited innovations 昀氀ow relatively freely across borders (x-axis). domestic extraction in several advanced and some Multilateral and market-led initiatives have unlocked emerging economies, as well as by multinational a range of 昀椀nancing mechanisms and innovation to mining companies headquartered in the West. support climate-proo昀椀ng against future disasters Scrutiny from investors, downstream industries and and a rapid shift to climate mitigation efforts (y-axis). the public have led to longer approval processes and In response to public pressure, governments have more stringent environmental and social standards. broadly prioritized spending towards adaptation – and For example, since the early 2020s, the expansion in some cases mitigation – alongside other social and of lithium mining in Portugal has been signi昀椀cantly security concerns, dampening the impact of climate delayed due to environmental approvals; projects change on societal vulnerabilities. In this future, the in Canada and Australia have slowed based on scaling of food has been supported by international concerns relating to indigenous communities; and 昀氀ows of 昀椀nancing and technology, and shortages a rare species of buckwheat has limited domestic muted by 昀氀exible supply chains. Downside impacts mining in key locations in the United States of are primarily focused on resources that face barriers to America.10 trading or scaling: water and critical minerals. Higher commodity prices have driven in昀氀ationary Climate-driven declines in agricultural productivity impacts along the wider value chain, explored further have been met with a range of measures in (and felt more acutely) in the section on Resource most countries, with climate and nature-based competition. This has encouraged some countries interventions helping to transform food systems to and multinational companies to accelerate efforts be regenerative, climate-smart and healthy. Global to turn towards the circular economy as a means sharing of data and technologies has allowed of securing and diversifying the supply of critical more effective pre-emptive adaptation measures minerals and metals, reducing the need for extraction to be taken, such as the targeted use of 昀氀ood- and associated emissions. Industry coalitions are and drought-resilient seeds in some vulnerable working with future-focused governments to establish geographies. Although environmental degradation the incentives, policy frameworks, standards and continues to threaten aquaculture and 昀椀sheries, certi昀椀cations, and circularity-focused capabilities that 11 targeted nature-based adaptation measures have are necessary to scale. In some markets, business shored up domestic food networks (see Chapter models are being transformed to decrease demand 2.2: Natural Ecosystems). and increase both the recovery potential and actual recovery of metals and minerals, partially mitigating The allocation of risk has begun to shift away from the demand-supply gap going forward. vulnerable workforces and communities. The burden of continued weather shocks has been partially Despite these efforts and continued climate offset through adaptation actions, 昀椀nanced by 昀椀t-for- ambitions, higher prices and shortages are slowing purpose 昀椀nancial products, including weather-based momentum for the green energy transition in the index insurance, climate-related loan products, short-term. In lower-income economies without local guaranteed credit lines, and well-managed risk- minerals and metals assets, the promise of support 8 based exits from extreme-event-prone geographies. with green energy infrastructure is partly unful昀椀lled, Supply shocks stemming from natural disasters are and some are considering reverting to carbon- quickly absorbed by 昀氀exible, market-driven supply intensive energy sources to secure energy.12 chains, and global food insecurity continues to slowly trend downwards. The ability to scale water supply has similarly been Global Risks Report 2023 60
FIGURE 3.3 Level of water stress by major river basin, 2018 Water stress No stress (0-25%) Low (25-50%) Medium (50-75%) High (75-100%) Critical (>100%) Source Note 13 FAO, Aquastat database, 2022. Level of water stress (SDG 6.4.2) by major river basin (reference year 2018). It is calculated as the ratio between (a) the amount of total freshwater resources withdrawn in the three economic sectors (Agriculture, Service and Industry) and (b) the total renewable freshwater resources after detracting the amount of water needed to support existing environmental services. constrained. Water monitoring, ef昀椀ciency and Despite strong headwinds in the early 2020s, production measures have been prioritized by cities, geoeconomic cooperation resumes in the latter local and national governments to address more half of the decade, with stronger global trade as frequent and severe droughts and the growing water well as efforts on climate cooperation (x-axis), footprint of food production. Water remains heavily mirroring Resource collaboration. However, subsidized, but pricing is used to curb demand and domestic funding – and therefore overall investment encourage investment by the private sector and – in adaptation measures as well as technological households in water-ef昀椀cient, re-usable solutions, innovation has not kept pace with climate impacts including rainwater harvesting and stormwater to date (y-axis), given competing priorities, a runoffs. Some countries have limited the use of price growing insurance gap and continued costs of controls to industrial use, while others apply them disaster recovery. In this future, even international more broadly across populations, further fueling coordination cannot address triple-shortages in in昀氀ation, cost-of-living pressures and unrest. But even food, water and energy in the most vulnerable signi昀椀cant drops in water demand and waste have not nations, with extended climate-induced distress kept pace with the impact of climate change on water and disruptions to trade, and political and economic resources in the most exposed regions (Figure 3.3). stability. The capacity to scale supply through mechanisms such as desalinization and puri昀椀cation differ between In the absence of appropriate intervention, countries for geographical and economic reasons. water availability is now a concern in all regions. Water security continues to be threatened in some of Snowmelt, glacial melt and groundwater availability these countries, with growing regional impacts from has diminished, while 10% of global land area has hygiene and health crises, urban migration, internal experienced an increase in extremely high and displacement and involuntary migration. low river 昀氀ows in the same location. Continued geopolitical cooperation is evident through widespread engagement in the range of multilateral Resource constraints – mechanisms governing these resources, from the the danger of divergent distress 1992 Convention on the Protection and Use of Transboundary Watercourses and International Lakes Accelerated climate action (Water Convention) and the 1997 Convention on the Law of the Non-navigational Uses of International Watercourses (Watercourses Convention), to bilateral Resource Resource competition collaboration Geoeconomic cooperationand regional agreements. ontation However, water stress acts as a multiplier to shortages of other key resources. In the absence Geoeconomic confrResourceResource of effective adaptation, agricultural productivity is control constraints severely impacted by climate change, diverging in intensity between regions. Crop yields have fallen in Slow climate action volume and nutritional value due to heat, changing Global Risks Report 2023 61
including Brazil, South Africa, China, Germany and the United States of America, increasingly turning these markets towards alternate energy sources. Even in the absence of geopolitically fuelled shocks or constraints, continued price pressures on food, water and energy have resulted in an elongated cost-of-living crisis in selected markets, ushering in wage strikes, violent protests and state instability. Socioeconomic impacts have also begun to spread to more advanced economies, with a risk of partial deindustrialization caused by combined energy-water shortages. The shutdown of waterborne transport of trade is more regularly disrupting global supply chains, placing pressure on road and rail transports and dampening global economic growth.19 Energy- and water-intensive strategic industries, such as semiconductor manufacturing, located in resource- weather patterns, dry and wet precipitation extremes, insecure areas, have become new geopolitical and shifts to the distribution of insects, pests and hotspots, raising the risk of prolonged disputes and diseases.14 Agricultural output in the United States possible con昀氀icts. of America has declined overall due to decreased 15 production of rice, corn, soy and wheat. Russian agricultural yields have fallen in the country’s most Resource competition – productive southern regions and have not been the danger of resource autarkies fully balanced by the expansion of arable land in the 16 country’s north, where soils remain less productive. Accelerated climate action Climate change has reduced rice, wheat and 17 corn yields by 8% in China. Without focused conservation and restoration efforts, ocean warming Resource Resource Geoeconomic cooperation competition collaboration and acidi昀椀cation has caused broadscale declines in ontation aquaculture and 昀椀sheries, threatening not only food security but also livelihoods in some of the most climate-exposed countries. Geoeconomic confrResourceResource control constraints High-latitude, high-income and high-tech countries are comparatively less impacted, either due to Slow climate action contained climate impacts for now, or leveraging of rapid innovation to address food and water security 18 challenges. Free-昀氀owing global supply chains have In this future, there is accelerated climate action by helped distribute the overall hit to food production 2030 (y-axis) but global powers are aiming for self- levels, but the most resource-insecure countries are suf昀椀ciency in key resources, leaving many emerging those vulnerable to two prolonged crises: debt and and developing countries comparatively exposed. climate change. Given the extended capital 昀氀ight Heightened geopolitical confrontation is focused earlier in the decade, and without the 昀椀scal space to in the most geographically concentrated resource: speed up adaptation measures (see Chapter 1.2, metals and minerals (x-axis). Economic downturn), these countries have become even more heavily import-dependent, unable to scale In anticipation of a deteriorating geopolitical food production to meet the demands of population environment, self-suf昀椀ciency in sources of food growth, given water stress and deteriorated soil production has been scaled up in countries that conditions. can afford it, alongside a focus on adaptation, as considered in Resource collaboration. Food Green-energy supply is also at risk. Companies productivity has been enhanced, in part via mining critical metals and minerals in water-stressed technology, such as gene editing of crops, even in regions face regular interruptions to operations or the absence of extensive multilateral cooperation on closures, or are forced to invest in water sources that such technology. A sharper focus on productivity do not directly compete with human consumption, of existing farmlands, dietary shifts and reductions partially exacerbating shortages, as described in in food loss and waste are being utilized as levers. Resource collaboration. This elevates commodity Ef昀椀ciency in agricultural practices, land-use and food prices further, slowing the roll-out of green energy systems have allowed some countries to decouple infrastructure. In parallel, the frequency and severity food security and biodiversity trends, partially of heatwaves and droughts has forced green energy addressing the estimated 33% of global food sources – biofuels, hydropower and nuclear – into production previously wasted through unsustainable periodic production cuts, and some are on the verge production and consumption. of becoming stranded assets. Electrical supply has been destabilized in the near-term for many countries, While this has led to enhanced food production Global Risks Report 2023 62
FIGURE 3.4 Relevance of critical metals and minerals Indicative supply chains: key producers and consumers Oil and gas Upstream Refining/minstream Consumption Oil US Saudi Arabia Russia US China Russia US China India Natural Gas US Russia Iran Russia Qatar Australia US Russia China Clean technologies Mining Processing Battery material Battery cell/pack Electric vehicle deployment Copper Chile Peru China Chile China Korea Japan China US Korea China US EU Mining Processing Polysilicon Solar panel Photovoltaic system installation Lithium Australia Chile China Chile China Korea Germany China Korea Canada China EU US Nickel Indonesia China Indonesia China Korea Germany China Korea Canada China EU US Mining Processing Wind turbine & components Wind installation Cobalt DRC China China India US Spain Germany China EU US Rare earths China China China India US Spain Germany China EU Source Note Leruth, et al. 2022.20 Largest producers and consumers are indicative only. overall in many advanced economies, the bene昀椀ts geographic diversi昀椀cation. For example, in the early have not been widely shared, with signi昀椀cant half of the 2020s, the United States was 100% divergence in the level of food security between net import-reliant for 14 critical minerals, including 22 countries. Even as some global trade in protein has gallium, natural graphite, indium and vanadium. continued, shortages and higher prices have hit At the time, China was the leading producer for lower socioeconomic groups, and developing and 16 of the 32 strategic minerals, including the emerging countries the hardest, particularly those aforementioned resources, representing 98%, 82%, least able to scale food production in the absence 58% and 66%, respectively, of the world’s total 23 of international support. This includes parts of production. Africa, Central and South America, Small Island Developing States (SIDS) and South Asia, where With a trend towards remilitarization (see Chapter many economies have faced nearly decade-long 2.4: Human security), these strategic resources triple crises: debt, population growth and climate have become one of the primary fronts of economic change. Global poverty, climate-sensitive livelihood warfare over the latter half of the decade. Despite crises, malnutrition and diet-related diseases, competing 昀椀scal priorities, more states have sought state instability and involuntary migration have all to diversify supply through domestic extraction risen, elongating and spreading the instability and where available, although many face environmental humanitarian crises described in Chapter 1.2, constraints outlined in Resource collaboration. Cost-of-living crisis. Enhanced capacity in processing and re昀椀ning has been targeted in particular by states with Critical metals and minerals are a key area of limited resource reserves (Figure 3.5). Resilience, geopolitical confrontation due to their geographic particularly for import-reliant markets, has partially concentration. These resources are not only translated into redundancies, with the building of essential to renewable energy capture, storage stockpiles of key materials exacerbating supply and ef昀椀ciency, but also continue to be leveraged crises. Inbound investment screening – which only for a wide range of other industrial applications, advanced economies have been able to afford including technological and military end-uses (Figure the opportunity cost – has been expanded to 21 3.4). Indium is part of touch screens as well as mining and related industries to minimize foreign solar panels; lithium compounds are utilized by interference. Other countries have followed the the pharmaceutical industry; cobalt has multiple lead of Canada, ordering certain foreign companies aerospace applications but is also of increasing to unwind investments in mining due to the 24 interest as a catalyst for green hydrogen production; perceived threats to national security. With limited and vanadium is used as an input for industrial-scale options, outbound investment screening is now batteries as well as a steel alloy in nuclear reactors, being contemplated by import-reliant markets space vehicles and aircraft carriers. The resulting as a potential lever, although most major powers demand-supply gap described in Resource continue to leverage increasingly state-directed collaboration is exacerbated in this future because investment in emerging export markets across Latin of geopolitical rivalries, exposing the brittleness of America and Africa as a means of securing access global supply chains with limited opportunities for to these resources. Global Risks Report 2023 63
FIGURE 3.5 Reserves of critical metals and minerals Australia Cuba Democratic Rep. of the Congo Indonesia Morocco, 1% Russia Other Cobalt 18% 3% 7% 46% 8% 3% 3% 8% Canada China, 1% Philippines USA, 1% Brazil China Madagascar North Korea, 1% Türkiye Graphite 22% 23% 8% 8% 6% 28% India, 3% Mozambique Tanzania Uzbekistan, 2% Argentina Australia Chile China Other Lithium 10% 26% 42% 7% 3% 12% Portugal, 1% USA Australia Brazil China Indonesia Russia Other Nickel 22% 17% 3% 22% 5% 8% 21% Canada, 2% Philippines USA, 1% Russia South Africa Zimbabwe, 2% Platinum 6% 90% group metals Canada, 1% USA, 1% Source Note IEA, World Energy Outlook Special Report: The Role of Critical References to 1% refer to
recent creation of OMEC: an organization of mineral 30 exporting countries, similar to OPEC. While the resource boom has offered a path to growth for some of these countries, for others the focus on these assets has created a “Dutch Disease” phenomenon, or led to increased corruption, 31 inequality, violence and humanitarian crises. Further, illicit activities and the risk of accidental or intentional escalation into hot warfare over resources has risen, particularly in the border zones and global commons. Export constraints on minerals have placed upwards pressure on broader international governance and enforcement mechanisms that oversee new exploration zones – including those relating to mining in international waters, polar regions and in space. As the hunt for new mineral sources turns to the ocean, national marine jurisdictions are increasingly contentious, with a 32 growing proportion of territory under dispute. Resource control – the danger of resource wars resulted in even more emissions, including the very Accelerated climate action potent methane. Intensive and inef昀椀cient farming has exacerbated soil degradation, water stress, pollution and the decline in production capacity. This has Resource Resource competition collaboration Geoeconomic cooperation created broader domestic trade-offs, particularly with ontation sectors directly dependent on biological resources, with knock-on impacts for economic growth and productivity and the speed of the green transition. Geoeconomic confrResource Resource Arable land has been increasingly prioritized for control constraints agriculture, shifting away from biofuels and green energy infrastructure. Slow climate action Similar to Resource constraints, water stress is now widespread. In developing countries, this By 2030, investment in adaptation measures has particularly impacts women and girls responsible not kept pace with climate impacts to date (y-axis). for water collection, with knock-on impacts for At the same time, geopolitical dynamics have turned health and education outcomes. More widespread the natural resource crisis from one of affordability scarcity, combined with paralysis of international to one of availability (x-axis), creating a cascading cooperation mechanisms, has necessitated a degree economic, environmental and humanitarian crisis in of water nationalism, resulting in prolonged disputes 34 all but a handful of select countries – but even these between neighbouring countries. In the face of remain exposed through cross-border effects. In this spreading humanitarian crises and state instability, future, the resulting socioeconomic fall-out exceeds water infrastructure continues to be used both as the scope and scale of all other futures, and state a weapon and target, mirroring past water con昀氀icts 35 intervention turns even more aggressive, expanding and terrorism in India, Pakistan and Afghanistan. In beyond economic confrontation to secure supply of addition, there is less visible abuse and depletion of necessities for populations. shared “non-renewable” groundwater reserves, such as in Saharan Africa and the Middle East, raising the Building on Resource constraints, both affordability risk of con昀氀ict.36 and availability concerns are widening inequality. Re昀氀ecting Resource competition, self-suf昀椀cient Conditions of scarcity initially consolidated the sources of food production have been scaled in昀氀uence of geopolitical blocs, heavily re昀氀ecting raw up, but with limited sharing of innovation and resource trade dependences, as well as innovation 昀椀nancing, the tipping point of overall productivity and information 昀氀ows. Increasingly however, distrust growth in agriculture has already passed. Without between global powers is arti昀椀cially exacerbating effective policy, 昀椀nancing and technological support supply crises on a global scale. Beyond Resource for adaptation practices, lower socioeconomic competition, all three resources are weaponized communities and countries have resorted to changes by resource-rich countries where possible, as in crop choice and large shifts in land-use patterns to both offensive and defensive tools in a more 33 maintain current production growth. Agriculture has zero-sum geopolitical environment (see Chapter become an even larger driver of global emissions. 1.2, Economic warfare). In this world, the export Land-clearance for crops and grazing have led of resources will soon supplant investment as a to deforestation, and an increase in livestock has measure of global soft power, although economic Global Risks Report 2023 65
power will continue to be leveraged to achieve energy and water insecurity becomes a driver of strategic objectives by more subtle, indirect means. social polarisation, civil unrest and political instability Facing actual or perceived shortages, states in advanced and developing economies alike. It also continue to quickly and regularly exercise control becomes a driver for cross-border terrorism, with over key resources to protect their own population, devastating impacts given the proliferation of high- which will fracture alliances, deepen conditions of tech weaponry (see Chapter 2.4: Human security). scarcity, and result in escalating trade tensions that restrict the 昀氀ow of climate technologies. Exposed on In this future, there has been little incentive – or multiple fronts, state intervention grows in a broader 昀椀scal room – to invest in climate change and range of industries, including renationalization of environmental protection. Overexploitation and industries. pollution – the tragedy of the global commons – has expanded, but continues to go unpunished Confrontations regularly extend beyond the or undiscovered, and existing agreements and economic sphere. Transboundary con昀氀icts and regulations are regularly breached or not enforced. violence have become more common as one of Famine has returned at a scale not seen in the the few ways in which states can secure supply last century. The sheer scale of humanitarian and of strategic resources. Hotspots re昀氀ect shifts to environmental crises showcases broader paralysis biodiversity patterns, heightened competition over and ineffectiveness of key multilateral mechanisms terrestrial and marine foodstocks, and the pressing in addressing crises facing the global order, need for metals and minerals that underpin secure spiralling downwards into a self-perpetuating and energy and technological development. Food, compounding polycrises. Global Risks Report 2023 66
Endnotes 1. Tooze, Adam, “Welcome to the world of the polycrisis”, Financial Times, 28 October 2022, https://www. ft.com/content/498398e7-11b1-494b-9cd3-6d669dc3de33. . 2. World Food Programme, Acute food insecurity: Numbers explained, 11 November 2022, https://docs. wfp.org/api/documents/WFP-0000130762/download/; Cozzi, Laura, et al., “For the 昀椀rst time in decades, the number of people without access to electricity is set to increase in 2022”, International Energy Agency (IEA), 3 November 2022, https://www.iea.org/commentaries/for-the-昀椀rst-time-in-decades-the- number-of-people-without-access-to-electricity-is-set-to-increase-in-2022. 3. UN, UN Population Division Data Portal, https://population.un.org/dataportal/home, accessed 28 November 2022. 4. Organisation for Economic Co-operation and Development (OECD) and Food and Agricultural Organization of the United Nations (FAO), OECD-FAO Agricultural Outlook 2022-2031, OECD and FAO, 29 June 2022. 5. UN Environment Programme International Resource Panel, Options for Decoupling Economic Growth from Water Use and Water Pollution, 2015, https://www.resourcepanel.org/reports/options-decoupling- economic-growth-water-use-and-water-pollution. 6. International Energy Agency (IEA), The Role of Critical Minerals in Clean Energy Transitions, 2021, https:// www.iea.org/reports/the-role-of-critical-minerals-in-clean-energy-transitions. 7. Hund, Kirsten, et al., Minerals for Climate Action: The Mineral Intensity of the Clean Energy Transition, International Bank for Reconstruction and Development and The World Bank, 2020, https://pubdocs. worldbank.org/en/961711588875536384/Minerals-for-Climate-Action-The-Mineral-Intensity-of-the- Clean-Energy-Transition.pdf. 8. Jack, Kelsey and Nick Wilkinson, Risk and resilience: Agricultural adaptation to climate change in developing countries, International Growth Centre (IGC), 2022, https://www.theigc.org/wp-content/ uploads/2022/03/Kelsey-and-Wilkinson-Growth-brief-March-2022.pdf. 9. KPMG, Resourcing the Energy Transition: Making the World Go Round, 2021, https://assets.kpmg/ content/dam/kpmg/xx/pdf/2021/03/resourcing-the-energy-transition.pdf; Arndt, Nicholas T., et al., “Future Global Mineral Resources”, Geochemical Perspectives, vol. 6, no. 1, 2017, pp. 1-171, https:// www.geochemicalperspectives.org/online/v6n1/. 10. Fleming, Sam, Alice Hancock and Peter Wise, “EU digs for more lithium, cobalt and graphite in green energy push”, Financial Times, 16 August 2022, https://www.ft.com/content/363c1643-75ae-4539- 897d-ab16adfc1416; Karim, Naimul, “Australian miner bails on Quebec rare earth projects amid First Nation resistance”, Financial Post, 13 October 2022, https://昀椀nancialpost.com/commodities/mining/ australian-miner-bails-on-quebec-rare-earth-projects-amid-昀椀rst-nation-resistance; Donnelly, Patrick, “Lawsuit Launched Seeking Final Endangered Species Protection for Nevada’s Rare Tiehm’s Buckwheat” [Press Release], Center for Biological Diversity, 25 October 2022; Barber, Gregory, “The Lithium Mine versus the Wild昀氀ower”, Wired, 17 June 2022, https://www.wired.com/story/lithium-mine-for-batteries- versus-the-wild昀氀ower/. 11. World Economic Forum, “Circular Transformation of Industries: Unlocking New Value in a Resource- Constrained World”, 2023. 12. Thomas, Helen, “Mining isn’t living up to its own hype”, Financial Times, 9 November 2022, https://www. ft.com/content/140fb908-ba2e-4fcf-8a02-74e80991b5cf?desktop=true&segmentId=7c8f09b9-9b61- 4fbb-9430-9208a9e233c8#myft:noti昀椀cation:daily-email:content. 13. Food and Agriculture Organization of the United Nations (FAO), Level of Water Stress (SDG 6.4.2) by major river basin, https://data.apps.fao.org/catalog/iso/40bc32f6-1467-44ac-8f7c-3d67cbb1cbd7, accessed 16 December 2022. Conley, Heather A. and Cyrus Newlin, “Climate Change Will Reshape Russia”, Center for Strategic and International Studies, 2021, https://www.csis.org/analysis/climate- change-will-reshape-russia. 14. The Intergovernmental Panel on Climate Change (IPCC), Special Report on Climate Change and Land: Food Security, 2022. 15. Environmental Defense Fund, How Climate Change Will Impact U.S. Corn, Soybean and Wheat Yields: A County-Level Analysis of Climate Burdens and Adaptation Needs in the Midwest, 2022. 16. Conley, Heather A. and Cyrus Newlin, “Climate Change Will Reshape Russia”, Center for Strategic and International Studies, 2021, https://www.csis.org/analysis/climate-change-will-reshape-russia.Ibid. 17. Li, Man, “Climate Change to Adversely Impact Grain Production in China by 2030”, International Food Policy Research Institute (IFPRI) blog, 13 February 2018, https://www.ifpri.org/blog/climate-change- adversely-impact-grain-production-china-2030. 18. The Intergovernmental Panel on Climate Change (IPCC), Sixth Assessment Report: Working Group II (WGII), 28 February 2022, https://www.ipcc.ch/assessment-report/ar6/. 19. Thomas, Helen, “Climate is a supply chain problem that can’t be ignored”, Financial Times, 17 August 2022, https://www.ft.com/content/94375406-fb66-4f51-bb70-03e5ac7ec8ec?desktop=true&segmentId =7c8f09b9-9b61-4fbb-9430-9208a9e233c8#myft:noti昀椀cation:daily-email:content. Global Risks Report 2023 67
Endnotes 20. Leruth, Luc, Adnan Mazarei, Pierre Régibeau and Luc Renneboog, 22-12 Green Energy Depends on Critical Minerals. Who Controls the Supply Chains?, Peterson Institute for International Economics, https://www.piie.com/publications/working-papers/green-energy-depends-critical-minerals-who- controls-supply-chains. 21. Dempsey, Harry, “Rio Tinto warns of excess globalisation in supply chains for critical metals”, Financial Times, 11 October 2022, https://www.ft.com/content/6da95eb8-6def-43a9-9eb0-8a026781c31c?deskt op=true&segmentId=7c8f09b9-9b61-4fbb-9430-9208a9e233c8#myft:noti昀椀cation:daily-email:content. 22. US Department of the Interior US Geological Survey, Mineral Commodity Summaries 2022, 31 January 2022, https://pubs.usgs.gov/periodicals/mcs2022/mcs2022.pdf. 23. Ibid. 24. Sevastopulo, Demetri and Edward White, “Canada orders Chinese companies to divest stakes in lithium mines”, Financial Times, 3 November 2022, https://www.ft.com/content/6ca9a470- 59ee-4809-8a5b-35f6073c9907?desktop=true&segmentId=7c8f09b9-9b61-4fbb-9430- 9208a9e233c8#myft:noti昀椀cation:daily-email:content. 25. International Energy Agency (IEA), World Energy Outlook Special Report: The Role of Critical Minerals in Clean Energy Transitions, https://www.iea.org/reports/the-role-of-critical-minerals-in-clean-energy- transitions, 2022; US Geological Survey, Mineral Commodity Summaries 2022: Nickel, https://pubs.usgs. gov/periodicals/mcs2022/mcs2022-nickel.pdf; Lithium, https://pubs.usgs.gov/periodicals/mcs2022/ mcs2022-lithium.pdf; Platinum Group Metals, https://pubs.usgs.gov/periodicals/mcs2022/mcs2022- platinum.pdf; Cobalt, https://pubs.usgs.gov/periodicals/mcs2022/mcs2022-cobalt.pdf; Graphite, https:// pubs.usgs.gov/periodicals/mcs2022/mcs2022-graphite.pdf. 26. Wilson Center, Critical Mineral Maps, 17 March 2022, https://www.wilsoncenter.org/article/critical- mineral-maps. 27. Natural Resources Canada, Joint Statement by Canada’s Minister of Natural Resources and the European Commissioner for Internal Market, 19 July 2021, https://www.canada.ca/en/natural-resources- canada/news/2021/07/joint-statement-by-canadas-minister-of-natural-resources-and-the-european- commissioner-for-internal-market.html. 28. Bond, David E., Francisco de Rosenzweig and Samuel Scoles, “Mexico nationalizes lithium; sets up state-owned company”, White & Case, 9 September 2022, https://www.whitecase.com/insight-alert/ mexico-nationalizes-lithium-sets-state-owned-company. 29. O’Kane, Sean, “Tesla con昀椀rms plans to build lithium re昀椀nery in Texas”, Bloomberg, 20 October 2022, https://www.bloomberg.com/news/articles/2022-10-19/tesla-con昀椀rms-plans-to-build-lithium-re昀椀nery-in- texas. 30. KPMG, Resourcing the Energy Transition: Making the World Go Round, 2021, https://assets.kpmg/ content/dam/kpmg/xx/pdf/2021/03/resourcing-the-energy-transition.pdf; Dempsey, Harry and Mercedes Ruehl, “Indonesia considers Opec-style cartel for battery metals”, Financial Times, 31 October 2022, https://www.ft.com/content/0990f663-19ae-4744-828f-1bd659697468?desktop=true&segmentId=7c8f 09b9-9b61-4fbb-9430-9208a9e233c8#myft:noti昀椀cation:daily-email:content. 31. Schipani, Andres, “How the DRC became the battleground of a proxy war over precious resources”, Financial Times, 27 October 2022, https://www.ft.com/content/26125730-3113-4946-982a-989e2ac be472?desktop=true&segmentId=7c8f09b9-9b61-4fbb-9430-9208a9e233c8#myft:noti昀椀cation:daily- email:content. 32. Kyodo News, China ship with largest-ever cannon enters Japan waters near Senkakus, 25 November 2022, https://english.kyodonews.net/news/2022/11/cf16e72c5cb6-china-ship-with-largest-ever-cannon- enters-japan-waters-near-senkakus.html. 33. Pugh, T.A.M., et al.,“Climate analogues suggest limited potential for intensi昀椀cation of production on current croplands under climate change”, Nature Communications, vol. 7, no. 12608, 20 September 2016, https://www.nature.com/articles/ncomms12608. 34. Al-Monitor, Egypt warns of stalemate in Nile dam dispute, 27 September 2022, https://www.al-monitor. com/originals/2022/09/egypt-warns-stalemate-nile-dam-dispute. 35. Ashraf, Tamanna and Shlomi Dinar, “Dams, Terrorism and Water Nationalism’s Response to Globalization and Development: The Case of South Asia”, Terrorism and Political Violence, vol. 34, no. 5, 3 June 2022, pp. 958-978, https://www.tandfonline.com/doi/abs/10.1080/09546553.2022.2069449. 36. UN Water, The United Nations Water Development Report 2022: Groundwater: Making the Invisible Visible, 21 March 2022. Global Risks Report 2023 68
January 2023 Global Risks Report 2023 Conclusion: is preparedness possible? 4 Conclusion: is preparedness possible? While ongoing shocks unfold, the world stands mixed. The underestimation of – and therefore lack at a crossroads. As we enter a low-growth, low- of preparedness for – emerging macro risks (like investment and low-cooperation era, the actions that “grey rhinos” and “black swans”) re昀氀ect challenges we take today will dictate our future risk landscape. posed by high levels of uncertainty, low levels of We must ensure that addressing current crises does information, con昀氀icting data and cognitive biases. not detract from the longer-term view. Yet systematic progress is possible. Enhanced risk identi昀椀cation and foresight can be a key enabler Recent and current events such as COVID-19 for strategic decision-making, agenda-setting and and the cost-of-living crisis are steadily eroding resilience measures, helping to prioritize areas that economic, educational and health-related gains would bene昀椀t from data collection and monitoring, in a widening proportion of the population, with risk controls and resources, and redundancies. a growing divergence between advanced and developing countries. This in turn is interacting with The 昀椀rst task of foresight is to identify future a multiplicity of environmental and geopolitical risks developments, risks and opportunities. Both horizon – climate change, ecosystem collapse, multi-domain scanning and scenario planning are useful tools con昀氀icts – to further threaten the security and that can examine and build on “weak signals” in stability of societies around the world. qualitative and quantitative data sources to better anticipate emerging trends. Established methods 1 In this context, defensive, fragmented and crisis- can help crystallize expert disagreements, while a oriented approaches are short-sighted and often greater distinction between risk and uncertainty – perpetuate vicious cycles. Lack of preparedness imperfect knowledge, such that likelihood cannot be for longer-term risks will destabilize the global risks scienti昀椀cally quanti昀椀ed or known – will help challenge landscape further, bringing ever tougher trade-offs core assumptions. Greater levels of uncertainty for policy-makers and business leaders scrambling should shift the focus from the probable to the to address simultaneous crises. A rigorous approach possible: the study of potential outcomes needs to foresight and preparedness is called for, as we to be expanded to ensure that risk mitigation and aim to bolster our resilience to longer-term risks and preparedness addresses the full scope of possible 2 chart a path forward to a more prosperous world. impacts. This is then complemented by risk monitoring, which focuses on providing early warning Each risk requires concerted, speci昀椀c and for when speci昀椀c risks are about to materialize to customized efforts but several cross-cutting enable advanced preparedness measures. principles can support preparedness across themes. In this concluding section, we outline four principles Another step to enhance risk foresight is to explore for preparedness in this new era of concurrent dynamics of change, to map interconnections shocks: 1) strengthening risk identi昀椀cation and between risks, including dependencies between foresight, 2) recalibrating the present value of “future” critical systems. More sophisticated methods risks, 3) investing in multi-domain risk preparedness, of analyzing interconnected risks (beyond linear and 4) strengthening preparedness and response relationships) can support the evaluation and cooperation. prioritization of risk resources. Risks that are most in昀氀uenced by or exposed to other risks will be the most challenging to mitigate, while those that exert Improving risk identi昀椀cation an outsized in昀氀uence on the outcome of the network and foresight can be prioritized as key points of intervention. The need for a systemic view of and approach to global risks is re昀氀ected in the rising call for the appointment A wide range of disciplines aim to gather intelligence of National Risk and Resilience Of昀椀cers, to mirror the about the future, ranging from economics, business increasingly important role of the Chief Risk Of昀椀cer management, investment funds and insurance, in the private sector. While the mandate of this role to urban planning, climatology, virology and civil may vary in practice, it re昀氀ects the need for a cross- protection – but the track record around the use of cutting and whole-of-society view around external 3 foresight to enhance risk mitigation efforts remains risk foresight, mitigation and crisis management. Global Risks Report 2023 69
Rethinking ‘future’ risks manage crises, especially when millions of lives and livelihoods are at risk. However, when such risks manifest, resources and attention are often diverted Cognitive biases channel public attention towards from addressing global risks, especially those that recent, “catastrophic” events. Business and form the root causes of local catastrophes or those political imperatives tend to prioritize risks with that may arise outside the time frames relevant to a direct, immediate and localized impact, such today’s leaders. as food, fuel or other commodities’ shortages or local environmental disasters. This is necessary to This can skew preparedness efforts in the public FIGURE 4.1 Perceptions around preparedness and governance Risk name Risk preparedness Risk governance Please indicate the current effectiveness of Which set of stakeholders can most effectively risk management, taking into account mechanisms manage the risk? in place to prevent the risk from occurring or prepare to mitigate its impact Terrorist attacks Infectious diseases Breakdown of critical information infrastructure Asset bubble bursts Chronic diseases and health conditions Use of weapons of mass destruction Collapse or lack of public infrastructure and services Prolonged economic downturn Adverse outcomes of frontier technologies Proliferation of illicit economic activity Widespread cybercrime and cyber insecurity Employment crises State collapse or severe instability Digital inequality and lack of access to digital services Collapse of a systemically important industry or supply chain Failure to stabilize price trajectories Debt crises Interstate conflict Ineffectiveness of multilateral institutions and international cooperation Geoeconomic confrontation Digital power concentration Severe mental health deterioration Large-scale environmental damage incidents Cost-of-living crisis Large-scale involuntary migration Erosion of social cohesion and societal polarization Natural disasters and extreme weather events Natural resource crises Biodiversity loss and ecosystem collapse Misinformation and disinformation Failure of climate-change adaption Failure to mitigate climate change 0 25 50 75 100 0 25 50 75 100 Risk category Perception Stakeholder Economic Highly ineffective Local government Environmental Ineffective National government Geopolitical Indeterminate effectiveness Bilateral Societal Highly effective Multi-country Technological Effective Regional International organization Businesses Source Public-Private cooperation World Economic Forum, Global Risks Perception Survey 2022-2023. Global Risks Report 2023 70
and private sector alike. For better planning and preparedness, institutions must de-anchor risk prioritization from shorter-term incentives. Despite regularly featuring in the top rankings, the most severe global risks – pertaining particularly to climate and nature – are those we are still the least prepared for. The majority of GRPS respondents assessed existing measures to prevent or prepare for the Failure to mitigate climate change, Failure of climate-change adaptation, and Biodiversity loss and ecosystem collapse as ineffective or highly ineffective (Figure 4.1). Similarly, most respondents considered preparedness to be inadequate for Misinformation and disinformation, Erosion of social cohesion and societal polarization, Involuntary migration and Cost-of-living crisis. The growing global awareness of these risks is clear, but further action will likely continue to be stymied, given perceived shorter-term and localized crises and trade-offs. Without minimizing the need for an effective response, the over-prioritization of current challenges can quickly descend into a doom-loop of continuous global shocks, whereby resources are absorbed by crisis management, rather than longer-term, multi-domain resilience. Not all global directed to preparedness for future risks. Complex risks pose a preparedness trade-off, and solutions challenges cannot be solely solved by short-term that address both current needs and future risks decision-making – and yet long-term thinking alone can rebalance the cost-bene昀椀t ratio for necessary is insuf昀椀cient in the face of currently unfolding crises. investment. For example, investment in health and education, key tenets of managing present needs To break the cycle, business leaders and policy- in all societies as well as longer-term human capital makers need to embrace complexity and adopt a and economic development, strengthens societal dual vision that more effectively balances current resilience to multiple shocks and risks including crisis management with a longer-term lens. For climate change. example, in the wake of the COVID-19 pandemic, governments will not only need to target resources Additionally, many global risks have the potential to to stabilize distressed healthcare systems, but at impact economies and societies in an analogous the same time work to ensure that environments way, with similar consequences. For example, conducive to zoonotic disease spread are cyberattacks, social unrest or extreme weather adequately monitored, gain-of-function research could each cause the outage of critical information is regulated, and that synthesis requests to bio- infrastructure; or, on a more catastrophic scale, laboratories are screened to prevent future outbreaks volcanic eruptions and war may disrupt food 4 5 from natural spillovers, accidents and threat actors. security. Strengthening resilience efforts in critical areas therefore pays off in all scenarios and improves preparedness for a multiplicity of risks, both known Investing in multi-domain, and unknown, and short and long term. cross-sector risk preparedness Following recent shocks – the pandemic, in昀氀ation, war, among others – national governments are In addition, actions taken to address current increasingly focusing on addressing vulnerabilities challenges should, at a minimum, avoid exacerbating in critical systems, including potential disruptions to future risks, such as the potential trade-off between food, water, shelter, basic communication services food security, nature loss and climate change. and public safety, and developing multi-domain Recent crises have seen an extraordinary level responses. A bill has been introduced in the United of 昀椀scal intervention to protect individuals and States of America to form an interagency committee companies from the 昀椀nancial impacts of crises – to assess all global catastrophic risks over the next from the COVID-19 pandemic to energy prices. 30 years and develop strategies to ensure continuity While necessary and perhaps unavoidable in the of operations and critical infrastructure if these risks 6 circumstances at hand, it remains to be seen how arise. In addition, the UK Government is developing signi昀椀cantly these rapid, large-scale actions will a tool to measure socioeconomic resilience to key result in debt sustainability concerns and how widely civil contingencies risks, to provide a more nuanced, they distracted decision-makers from other risks data-driven view on how risks impact across different highlighted in this report. communities and groups.7 Conversely, many shorter-term actions can also act As global risks become more intertwined, as wider stabilizers, embedding and accelerating preparedness also needs to become more of a Global Risks Report 2023 71
shared responsibility between sectors, with local landscape, leading to spiralling distrust, declining and national governments, business and civil society safeguards against mutually assured economic each playing to their strengths, rather than traditional destruction, and currency and technological tools models of governments addressing market failures that are less in昀氀uential. Even areas traditionally 8 when they occur. For example, private-public open to collaboration, such as international climate partnerships can help close key gaps in innovation, research, are under threat. For example, data 昀椀nancing, governance and implementation of regarding Russia’s boreal forests –the biggest land- preparedness measures for emerging and well- based carbon store on the planet – is no longer established risks, such as food and water insecurity, available for international scienti昀椀c research because 11 weakened education and healthcare systems, and of the war in Ukraine. insuf昀椀cient regulation of dual-use technologies, or addressing the looming insurance gap relating to International organizations will continue to play 9 cyberwarfare. Innovative collaborations can also an essential role in global preparedness, even as minimize overall exposure to potential impacts, as they face signi昀椀cant headwinds that risk degrading organizations across geographies and sectors are the guardrails in place to address well-established rarely exposed to the same risks at the same time. issues. There have been numerous examples of the For example, data centres of different institutions politicization and partial paralysis of key international in differing geographies are highly unlikely to be mechanisms and organizations in recent crises. exposed to the same cyber or extreme weather These pressures may impede the development risks, meaning effective mitigation could include of meaningful norms and agreements required to regular backups of each other’s systems.10 mitigate emerging global risks – from the proliferation of military technologies to governing the global commons. Re-invigorating multilateral processes and Re-building and strengthening organizations is critical to the future of preparing for global risk preparedness and managing global risks. cooperation Additionally, speci昀椀c cooperation at sectoral, bilateral and regional levels will become even more important While national risk preparedness can enhance the in this environment. Robust data exchange and ability of societies and economies to rebound from collaborative monitoring processes have already shocks, most global risks are ‘owned’ by no one been established for some global risks (natural and sit outside the direct control of any one public disasters, extreme weather events and terrorist or private sector entity – meaning many global risks attacks, among others). Further, open-source data are most effectively tackled through coordinated, and scenario development have helped increase global action. Respondents to the GRPS shared their the effectiveness of individual risk responses, such views on which stakeholders were best prepared as the extensive work undertaken by the IPCC to tackle the key risks covered in the survey (Figure to develop a range of climate scenarios that has 4.1). The majority consider national governments, improved understanding, informed decarbonization multi-country efforts and international organizations strategies and allowed for collective alignment on to be the most relevant stakeholders for governing science-based targets. However, efforts are more these global risks – recognizing that global risks are nascent or non-existent in other areas, such as the complex, and effective preparedness can require long-term trajectory and impact of transformative AI. action at local, national, regional and global levels. Greater collaboration across industries and between countries – in terms of coordinated funding, research International cooperation has reached levels that and data sharing – is critical to help identify weak may have been unimaginable even a century ago. signals of emerging threats at both a national and However, the recent overload of crises has turned the global level. focus of nations inwards and the emerging outlook for international cooperation is deteriorating. Actions In a complex risks outlook, there must be a better taken to shore up national resilience can be self- balance between national preparedness and perpetuating. For example, stockpiling and export global cooperation. We need to act together, to controls can directly exacerbate global shortages shape a pathway out of cascading crises and build and position trade, 昀椀nancial and technological collective preparedness to the next global shock, dependencies as a strategic vulnerability, spurring whatever form it might take. Leaders must embrace further disintegration. Similarly, the pursuit of complexity and act on a balanced vision to create a domestic and global security goals may have stronger, prosperous shared future. unintended consequences for the geopolitical Global Risks Report 2023 72
Endnotes 1. UK Government Of昀椀ce for Science, “The Futures Toolkit: Tools for Futures Thinking and Foresight across UK Government”, November 2017, https://assets.publishing.service.gov.uk/government/uploads/ system/uploads/attachment_data/昀椀le/674209/futures-toolkit-edition-1.pdf 2. Courtney, Hugh, Jane Kirkland and Patrick Viguerie, “Strategy Under Uncertainty”, Harvard Business Review, 1997, https://hbr.org/1997/11/strategy-under-uncertainty. 3. Foroohar, Rana, “Wanted: a resiliency tsar for the US government”, Financial Times, 23 May 2021, https://www.ft.com/content/add77982-a162-4a29-a588-47c5cf121b28; Wilson, Colin, “Should the UK have a Chief Risk Of昀椀cer?”, UK Government blog, 20 April 2022, https://actuaries.blog.gov. uk/2022/04/20/should-the-uk-have-a-chief-risk-of昀椀cer/. 4. Esvelt, K., "Delay, Detect, Defend: Preparing for a Future in which Thousands Can Release New Pandemic”, Geneva Centre for Security Policy (GCSP), November 2022, https://dam.gcsp.ch/昀椀les/doc/ gcsp-geneva-paper-29-22. 5. Avin, Shahar, Bonnie C. Wintle, Julius Weitzdörfer, Seán S. Ó hÉigeartaigh, William J. Sutherland and Martin J. Rees, “Classifying global catastrophic risks”, Futures, vol. 102, 2018, pp. 20-26. 6. U.S. Senate Committee on Homeland Security & Governmental Affairs, Peters Introduces Bipartisan Bill to Ensure Federal Government is Prepared for Catastrophic Risks [Press release], 30 June 2022, https://www.hsgac.senate.gov/media/majority-media/peters-introduces-bipartisan-bill-to-ensure-federal- government-is-prepared-for-catastrophic-risks-#:~:text=The%20Global%20Catastrophic%20Risk%20M- itigation,plans%20for%20the%20risks%20identi昀椀ed. 7. UK Government Cabinet Of昀椀ce, "The UK Government Resilience Framework", 19 December 2022, https://www.gov.uk/government/publications/the-uk-government-resilience-framework/the-uk- government-resilience-framework-html. 8. Smith-Bingham, Richard, "Partnering with Purpose," Marsh McLennan, November 2021, https://www. marshmclennan.com/content/dam/mmc-web/insights/publications/2021/november/Marsh_McLennan- National_Preparedness_Commission_Partnering-with-Purpose_vF.pdf. 9. LaMorte, Dylan and Joshua Gold, “Insurance Companies Move to Expand Scope of War Exclusions”, Risk Management Magazine, 23 November 2022, https://www.rmmagazine.com/articles/ article/2022/11/23/insurers-move-to-expand-scope-of-war-exclusions. 10. Kaplan, Robert S. and Annette Mikes, “Managing Risks: A New Framework”, Harvard Business Review, June 2012. 11. Heal, Alexandra, “The ancient subarctic forests at risk from climate change and war”, Financial Times, 11 September 2022, https://www.ft.com/content/e59c800f-3704-4504-91b0-06e583d9cd42?desktop=tru e&segmentId=7c8f09b9-9b61-4fbb-9430-9208a9e233c8#myft:noti昀椀cation:daily-email:content. Global Risks Report 2023 73
Appendix A Technical Notes: Global Risks Perception Survey 2022-2023 A “global risk” is the possibility of the occurrence To ensure legibility, the names of some of the global of an event or condition which, if it occurs, would risks have been abbreviated in the 昀椀gures. negatively impact a signi昀椀cant proportion of global The portion of the full name used in the abbreviation GDP, population or natural resources. is in bold. Table A.1 presents the list of 32 global risks and de昀椀nitions adopted in the Global Risks Perception Survey 2022-2023. TABLE A.1 De昀椀nitions of global risks Global risks Description Asset bubble bursts Prices for housing, investment funds, shares and other assets become increasingly disconnected from the real economy, leading to a severe drop in demand and prices. Includes, but is not limited to: cryptocurrencies, energy prices, housing prices, and stock markets. Collapse of a systemically important Collapse of a systemically important global industry or supply chain with an impact on the global economy, industry or supply chain financial markets or society leading to an abrupt shock to the supply and demand of systemically important goods and services at a global scale. Includes, but is not limited to: energy, food and fast-moving consumer goods. Debt crises Corporate or public finances struggle to service debt accumulation, resulting in mass bankruptcies or insolvencies, liquidity crises or defaults and sovereign debt crises. Failure to stabilize price trajectories Inability to control the general price level of goods and services, including commodities. Inclusive of an unmanageable increase (inflation) or decrease (deflation) of prices. Proliferation of illicit economic activity Global proliferation of illicit economic activities and potential violence that undermine economic advancement and growth due to organized crime or the illicit activities of businesses. Includes, but is not limited to: illicit financial flows (e.g. tax evasion); and illicit trade and trafficking (e.g. counterfeiting, human trafficking, wildlife trade). Prolonged economic downturn Near-zero or slow global growth lasting for many years leading to periods of stagnation; or a global contraction (recession or depression). Biodiversity loss and ecosystem Severe consequences for the environment, humankind and economic activity due to destruction of natural collapse capital stemming from a result of species extinction or reduction spanning both terrestrial and marine ecosystems. Failure of climate-change adaption Failure of governments, businesses and individuals to enforce, enact or invest in effective climate-change measures to adapt to climate change, such as a lack of climate-resilient infrastructure. Failure to mitigate climate change Failure of governments, businesses and individuals to enforce, enact or invest in effective climate-change mitigation measures, such as the decarbonization of economic activity. Large-scale environmental damage Loss of human life, financial loss and/or damage to ecosystems as a result of human activity and/or failure to incidents co-exist with animal ecosystems. Inclusive of deregulation of industrial accidents, oil spills and radioactive contamination. Natural disasters and extreme weather Loss of human life, damage to ecosystems, destruction of property and/or financial loss at a global scale due events to extreme weather events. Inclusive of land-based (e.g. earthquakes, volcanos wildfires), water-based (e.g. floods), atmospheric (e.g. heat-waves), and extra-terrestrial based (e.g. comet strikes and geomagnetic storms). Risk categories Economic Environmental Geopolitical Societal Technological Global Risks Report 2023 74
TABLE A.1 De昀椀nitions of Global Risks Global risks Description Natural resource crises Severe commodity and natural resource supply shortages at a global scale as a result of human overexploitation and/or mismanagement of critical natural resources. Includes, but is not limited to: chemicals, food, minerals and water. Geoeconomic confrontation Deployment of economic levers by global or regional powers to decouple economic interactions between nations, restricting goods, knowledge, services or technology with the intent of gaining geopolitical advantage and consolidate spheres of influence. Includes, but is not limited to: currency measures, investment controls, sanctions, state aid and subsidies, and trade controls on energy, minerals and technology. Ineffectiveness of multilateral Ineffectiveness of international cooperation mechanisms due to a weakening of global multilateral institutions institutions and international cooperation or marked geopolitical fragmentation. Includes, but is not limited to processes that underpin coordination on: finance, the environment, humanitarian aid, health pandemics and trade. Interstate conflict Belligerent bilateral or multilateral conflict between states manifesting as cyber attacks, proxy wars or hot war. State collapse or severe instability Collapse of a state with geopolitical significance due to the erosion of institutions and rule of law, internal civil unrest and military coups, or the effects of severe regional or global instability. Terrorist attacks Large-scale or persistent small-scale terrorist attacks carried out by non-state actors with ideological, political or religious goals, resulting in loss of life, severe injury or material damage caused by biological, chemical, nuclear or radiological weapons or other means. Use of weapons of mass destruction Deployment of biological, chemical, cyber, nuclear, radiological or autonomous AI weapons, resulting in loss of life, destruction and/or international crises. Chronic diseases and health conditions Widescale increase in chronic physical health conditions. Includes, but is not limited to, conditions linked to excessive consumption habits and economic activity that releases harmful pollutants in the air, water or food through agricultural, industrial and household practices. Collapse or lack of public infrastructure Non-existence, or widespread bankruptcy of social security systems and erosion of social security benefits, and services alongside inequitable or insufficient public infrastructure and services. Includes but is not limited to lack of disability and family benefits, as well as affordable and adequate housing, public education, child and elder care, healthcare, transportation systems and urban development. Cost-of-living crisis Significant inability among broad sections of populations to maintain their current lifestyle due to increases in the cost of essential goods which are not matched with a rise in real household income. Employment crises Structural deterioration of work prospects or standards of work. Includes, but is not limited to: erosion of workers' rights; stagnating wages; rising unemployment and underemployment; displacement due to automation; stagnant social mobility; and geographical or industry mismatches between labour supply and demand. Erosion of social cohesion and societal Loss of social capital and fracturing of communities leading to declining social stability, individual and collective polarization well-being and economic productivity. Includes, but is not limited to: persistent and potentially violent civil unrest; and actual or perceived inequalities in opportunities across age, income bracket, ethnicity and race, educational background, demographic characteristics, and political affiliation. Infectious diseases Massive and rapid spread of viruses, parasites, fungi or bacteria that cause an uncontrolled contagion of infectious diseases, resulting in an epidemic or pandemic with loss of life and economic disruption. Includes, but is not limited to: zootic diseases, accidental or intentional releases of natural or man-made pathogens, the resurgence of pre-existing diseases due to lower levels of immunity, and the rise of antimicrobial resistance. Large-scale involuntary migration Large-scale involuntary migration and displacement across or within borders, stemming from: persistent discrimination and persecution, lack of economic advancement opportunities, natural or human-made disasters, and internal or interstate conflict. Misinformation and disinformation Persistent false information (deliberate or otherwise) widely spread through media networks, shifting public opinion in a significant way towards distrust in facts and authority. Includes, but is not limited to, dissemination by: states, public figures, media organizations and networks of individuals. Severe mental health deterioration Widescale spread of mental health disorders or rising inequality globally across multiple demographics, which negatively impacts well being, social cohesion and productivity. Includes, but is not limited to: anxiety, dementia, depression, loneliness and stress. Risk categories Economic Environmental Geopolitical Societal Technological Global Risks Report 2023 75
TABLE A.1 De昀椀nitions of Global Risks Global risks Description Adverse outcomes of frontier Intended or unintended negative consequences of technological advances on individuals, businesses, technologies ecosystems and/or economies. Includes, but is not limited to: AI, brain-computer interfaces, biotechnology, geo-engineering, quantum computing and the metaverse. Breakdown of critical information Deterioration, overload or shutdown of critical physical and digital infrastructure or services leading to infrastructure the breakdown of internet, cellular devices, public utilities or satellites. Stemming from, but not limited to, cyberattacks, intentional or unintentional physical damage, or solar storms. Digital inequality and lack of access to Fractured or unequal access to digital networks and technologies stemming from underinvestment, low digital digital services skills, insufficient purchasing power, or government restrictions on technologies. Digital power concentration Concentration of critical digital assets, capabilities or knowledge among a small number of individuals, businesses or states that can control access to digital technologies and demand discretionary pricing. Stemming from, but not limited to, the failure of anti-trust regulation, inadequate investment in the innovation ecosystem, or state control over key technologies. Widespread cybercrime and cyber Increasingly sophisticated cyberespionage or cybercrimes. Includes, but is not limited to: loss of privacy, data insecurity fraud or theft, and cyber espionage. Risk categories Economic Environmental Geopolitical Societal Technological Technical notes modi昀椀ed and/or expanded to re昀氀ect new ways in which the risks may materialize and the potential adverse outcomes they may cause. However, to The Global Risks Perception Survey (GRPS) is the ensure comparability over time, although names and World Economic Forum’s source of original risks de昀椀nitions were modi昀椀ed, the fundamental concept data, harnessing the expertise of the Forum’s of each risk has remained consistent with that of extensive network of academic, business, previous versions of the survey. government, civil society and thought leaders. Survey responses were collected from 7 September to 5 October 2022 from the World Economic Methodology Forum’s multistakeholder communities. The GRPS 2022–2023 was further re昀椀ned this year Updates to the GRPS 2022-2023 to gather more granular perceptions of risk and to incorporate new approaches to risk management and analysis. The GRPS 2022–2023 was comprised The list of 32 global risks included in the survey was of six sections: updated in 2022. 1. Outlook for the World asked respondents to Two new risks were added in response to observed characterize their outlook for the world over economic, geopolitical and environmental trends: the short term (two years) and the long term (10 years). Respondents were provided with 1. “Cost-of-living crisis” 昀椀ve options: (1) Progressive tipping points and persistent crises leading to catastrophic 2. “Misinformation and disinformation” outcomes, (2) Consistently volatile across economies and industries with multiple shocks In addition, “Climate action failure” was delineated accentuating divergent trajectories, (3) Slightly into two separate risks: volatile with occasional localized surprises, (4) Limited volatility with relative stability, and 1. “Failure of climate-change adaption” (5) Renewed stability with a revival of global resilience. A simple tally for each of the 昀椀ve 2. “Failure to mitigate climate change” options was calculated. The result is illustrated in Figure 1.10. The names and de昀椀nitions of the remaining risks have been revised and, where applicable, merged, 2. Currently Manifesting Risks asked Global Risks Report 2023 76
respondents to rank the top 昀椀ve risks among into account any mechanism in place to prevent 14 pre-selected risks in order of how severe the risk from occurring or prepare to mitigate they believe their impact will be on a global its impact. The respondent was provided 10 level in 2023. The 昀椀nal rank is the average rank randomly selected global risks, and was asked estimated by the respondents, weighted by to rate current effectiveness based on 昀椀ve the number of respondents who selected the options: (1) Highly ineffective, (2) Ineffective, (3) particular risk. Options included: Continued Indeterminate effectiveness, (4) Effective, and (5) waves of COVID-19, Cost-of-living crisis, Highly effective. A simple tally of the number of Cyberattacks on critical infrastructure, times a risk was identi昀椀ed on each level of the Debt crisis, Deployment of chemical and 昀椀ve-point effectiveness scale was calculated on biological weapons on a catastrophic scale, this basis. The result is illustrated in Figure 4.1. Deployment of nuclear weapons on a catastrophic scale, Disruptions in global Respondents were then asked to identify supply chains for non-food goods, Energy up to three stakeholders who can effectively supply crisis, Failure to set and meet manage the most severe risks identi昀椀ed in national net-zero targets, Food supply crisis, Section 3. Respondents could choose among Rising in昀氀ation, Structural failures in health the following eight entities: local government, systems, Weakening of human rights, and national government, bilateral, multi-country, Weaponization of economic policy such as regional, international organization, businesses, sanctions and trade controls. To ensure legibility, public-private cooperation. A simple tally of the the names of some of the global risks have number of times a stakeholder was identi昀椀ed as been abbreviated in the 昀椀gures. The portion of effective was calculated on this basis. The result the full name used in the abbreviation is in bold. is illustrated in Figure 4.1. The result is illustrated in Figure 1.1. 6. Future Outlook for the World captured the 3. Global Severity 2 Years and 10 Years asked respondents’ outlook on global cooperation respondents to estimate the likely impact over the next 10 years. Respondents were (severity) for each of the 32 global risks, on a asked to select from among three options: 1-7 scale [1 – Low severity, 7 – High severity], (1) Broad-base convergence to a multilateral over both a two-year and 10-year period. rules-based order, (2) Fractures between Respondents were asked to evaluate the competing economies which consolidate into severity, considering the impact on populations, blocs and new structures for cooperation, GDP or environmental resources on a global and (3) Wide-scale division of economies into scale. They were also allowed to nominate competing blocks with divergent standards, any other risk considered missing from the 32 values and paradigms with limited collaboration. global risks. A simple average based on the A simple tally for each of the three options was scores selected was calculated. The results are calculated. illustrated in Figure 1.2 and Figure 2.1. Completion thresholds 4. Global Risks Consequences seeks to A total of 1,316 responses to the GRPS were understand of the potential consequences of received. From these, 1,249 were kept, using as a risks, to create a network map of the global threshold at least one non-demographic answer. risk landscape. Respondents were provided 10 randomly selected global risks (from the full • Outlook for the World: 1,244 respondents list of 32 global risks), and were then asked selected at least one of the short-term and long- to select up to 昀椀ve global risks (from the full term world outlook options. list) likely to be triggered by each of the 10 risks materializing. In visual results, “Nodes: – Short-term outlook for the world: 1,233 Risk in昀氀uence” is based on a simple tally of all bidirectional relationships identi昀椀ed by – Long-term outlook for the world: 1,231 respondents. “Edges: Relative in昀氀uence” is based on a simple tally of the number of times • Currently Manifesting Risks: 1,180 the risk was identi昀椀ed as a consequence. respondents ranked at least one manifesting risk. However, visual do not show all connections: weaker relationships identi昀椀ed by less than 25% • Global Severity 2 Years and 10 Years: 1,091 of respondents were not included as edges. respondents evaluated the severity of at least "Employment crises" was not offered as a one risk in one time frame. randomly selected risk, and is shown only as a consequence. “Prolonged economic downturn” – Short-term severity: 1,086 was not offered as a consequence, and is only shown as a cause. – Long-term severity: 999 5. Risk Preparedness and Governance • Global Risks Consequences: 877 respondents asked respondents to indicate the current paired at least one materializing risk with its effectiveness of risk management across consequence. economies and multiple stakeholders, taking Global Risks Report 2023 77
• Risk Preparedness and Governance: 869 • Sample distribution: the 1,249 respondent respondents answered at least one of the who answered at least one non-demographic preparedness and governance questions. question were used to calculate the sample distribution by place of residence (region), – 839 respondents scored the effectiveness gender, age, area of expertise and organization level for at least one risk type. – 789 respondents mapped at least one Figure A.2 presents some key descriptive stakeholder against at least one risk statistics and information about the pro昀椀les of the respondents. • Future Outlook for the World: 869 respondents answered the Future Outlook for the World question. FIGURE A.2 Survey sample composition Gender Age group 30% Other, 2% 23% Female, 20% 33% 10% 11% Male, 2% 4% 65% 69 Not filled Organization Region Non-governmental organization (NGO), 9% Latin America and the Caribbean, 11% Not filled, 1% Europe, 36% Sub-Saharan Private Sector, 54% International Organization, Africa, 12% 11% South Asia, 5% Government, 14% Middle East and Academia, North Africa, 6% East Asia and Other, 5% 13% the Pacific, 14% North America, Central Asia, 2% 13% Source World Economic Forum Global Risks Perception Survey 2022-2023. Global Risks Report 2023 78
Appendix B Executive Opinion Survey: National Risk Perceptions Figure B.1 presents the list of 35 risks that were To ensure legibility, the names of some of the global incorporated into the World Economic Forum’s risks have been abbreviated in the 昀椀gures. The 2022 Executive Opinion Survey (EOS), which was portion of the full name used in the abbreviation is administered between April and September 2022. in bold. The risks are comparable to those in the GRPS (Global Risks Perception Survey) but are applied at a more granular level to re昀氀ect the possible short-term and country-level manifestations of global risks. TABLE B.1 List of risks Asset bubble burst Terrorist attacks Collapse of a systemically important industry Weapons of mass destruction Debt crises Collapse or lack of social services and public infrastructure Proliferation of illicit economic activity Cost-of-living crisis Prolonged economic stagnation Employment and livelihood crises Rapid and/or sustained inflation Erosion of social cohesion and well-being Severe commodity price shocks or volatility Infectious diseases (e.g. energy, food, metals) Blue (marine/freshwater) biodiversity loss and Large-scale involuntary migration ecosystem collapse Failure of climate-change adaption Misinformation Failure of climate-change mitigation Pollution-driven harms to human health Terrestrial biodiversity loss and ecosystem collapse Severe mental health deterioration Human-made environmental damage Widespread youth disillusionment Natural disasters and extreme weather events Automation and displacement of jobs Severe commodity supply crises Breakdown of critical information infrastructure (incl. energy, food, water) through cyber attacks Geoeconomic confrontations Digital power concentration and monopolies (incl. sanctions, trade wars, investment screening) Geopolitical contestation of strategic resources Failure of cybersecurity measures (incl. loss of privacy, (incl. technology, energy, minerals) data fraud or theft, cyber espionage) Interstate conflict Lack of widespread digital services and digital inequality State collapse Risk categories Economic Environmental Geopolitical Societal Technological Source World Economic Forum Global Risks Perception Survey 2022-2023. Global Risks Report 2023 79
Figure B.2 presents the top 昀椀ve risks for each of the “Risk 1” indicates the most frequently selected 121 economies surveyed. risk in each economy. Tied risks are presented in alphabetical order, with the tie indicated by Over 12,000 respondents were presented with the numbering. For example, in Angola, two risks (“Rapid following question: “Which 昀椀ve risks are the most and/or sustained in昀氀ation” and “Employment and likely to pose the biggest threat to your country in livelihood crises”) are tied for 昀椀rst place and there is, the next two years?” and were asked to select these therefore, no risk listed in second place. from a list of 35 risks. TABLE B.2 Top five risks identified by the Executive Opinion Survey (EOS) Albania Armenia Bangladesh 1 Infectious diseases 1 Interstate conflict 1 Rapid and/or sustained inflation 2 Failure of cybersecurity measures 2 Rapid and/or sustained inflation 2 Debt crises 3 Rapid and/or sustained inflation 3 Erosion of social cohesion 3 Severe commodity price shocks 4 Geopolitical contestation of resources 4 Severe commodity price shocks 4 Human-made environmental damage 5 Severe commodity supply crises 5 Geoeconomic confrontation 5 Geopolitical contestation of resources Algeria Australia Barbados 1 Rapid and/or sustained inflation 1 Cost-of-living crisis 1 Natural disasters and extreme weather events 2 Cost-of-living crisis 2 Debt crises 2 Cost-of-living crisis 3 Digital inequality 2 Rapid and/or sustained inflation 3 Rapid and/or sustained inflation 4 Geopolitical contestation of resources 4 Geoeconomic confrontation 4 Severe commodity price shocks 5 Interstate conflict 5 Failure of climate-change adaptation 5 Debt crises Angola Austria Belgium 1 Rapid and/or sustained inflation 1 Rapid and/or sustained inflation 1 Cost-of-living crisis 1 Employment and livelihood crises 2 Severe commodity price shocks 2 Rapid and/or sustained inflation 3 Cost-of-living crisis 3 Breakdown of critical infrastructure 3 Failure of climate-change adaptation 4 Collapse of services and public 4 Geoeconomic confrontation 4 Debt crises infrastructure 5 Severe commodity supply crises 5 Geopolitical contestation of resources 5 Geoeconomic confrontation Argentina Bahrain Benin 1 Rapid and/or sustained inflation 1 Cost-of-living crisis 1 Cost-of-living crisis 2 Debt crises 2 Debt crises 2 Severe commodity price shocks 2 Proliferation of illicit economic activity 3 Severe commodity price shocks 3 Employment and livelihood crises 4 State collapse 4 Prolonged economic stagnation 4 Rapid and/or sustained inflation 5 Severe commodity supply crises 4 Rapid and/or sustained inflation 5 Severe commodity supply crises Risk categories Economic Environmental Geopolitical Societal Technological Global Risks Report 2023 80
TABLE B.2 Top five risks identified by the Executive Opinion Survey (EOS) Bolivia (Plurinational State of) Bulgaria Chad 1 Prolonged economic stagnation 1 Rapid and/or sustained inflation 1 Employment and livelihood crises 1 Digital inequality 2 Proliferation of illicit economic activity 2 Geopolitical contestation of resources 3 Employment and livelihood crises 3 Cost-of-living crisis 3 Terrestrial biodiversity loss and ecosystem collapse 4 State collapse 4 Interstate conflict 4 Blue biodiversity loss and ecosystem collapse 5 Human-made environmental damage 5 State collapse 5 Debt crises 5 Debt crises 5 Digital inequality Cambodia 5 Erosion of social cohesion 1 Geoeconomic confrontation 5 Digital power concentration 2 Cost-of-living crisis Bosnia and Herzegovina Chile 1 Severe commodity supply crises 2 Digital inequality 1 Rapid and/or sustained inflation 1 State collapse 4 Geopolitical contestation of resources 2 Erosion of social cohesion 3 Severe commodity price shocks 5 Failure of climate-change adaptation 3 Proliferation of illicit economic activity 4 Digital inequality 4 Severe commodity supply crises Cameroon 5 Cost-of-living crisis 1 Cost-of-living crisis 5 State collapse 2 Debt crises Botswana China 1 Cost-of-living crisis 3 Digital inequality 1 Geoeconomic confrontation 2 State collapse 4 Employment and livelihood crises 2 Natural disasters and extreme weather events 3 Severe commodity supply crises 5 Geopolitical contestation of resources 3 Rapid and/or sustained inflation 4 Failure of cybersecurity measures 4 Infectious diseases Canada 5 Debt crises 1 Cost-of-living crisis 5 Geopolitical contestation of resources 2 Debt crises 5 Asset bubble burst Brazil 1 Rapid and/or sustained inflation 3 Rapid and/or sustained inflation 5 Digital power concentration 2 Proliferation of illicit economic activity 4 Failure of climate-change adaptation Colombia 3 Geoeconomic confrontation 5 Asset bubble burst 1 Rapid and/or sustained inflation 4 Severe commodity price shocks 2 Digital inequality Cape Verde 4 Employment and livelihood crises 1 Debt crises 3 Employment and livelihood crises 2 Cost-of-living crisis 4 State collapse 3 Geoeconomic confrontation 5 Cost-of-living crisis 4 Rapid and/or sustained inflation 5 Employment and livelihood crises Risk categories Economic Environmental Geopolitical Societal Technological Global Risks Report 2023 81
TABLE B.2 Top five risks identified by the Executive Opinion Survey (EOS) Congo (Democratic Republic of) Denmark El Salvador 1 Digital inequality 1 Breakdown of critical infrastructure 1 Debt crises 2 State collapse 2 Rapid and/or sustained inflation 2 State collapse 3 Debt crises 3 Severe commodity price shocks 3 Cost-of-living crisis 5 Interstate conflict 4 Geoeconomic confrontation 4 Natural disasters and extreme weather events 5 Cost-of-living crisis 5 Asset bubble burst 5 Employment and livelihood crises 5 Digital power concentration Dominican Republic Estonia 1 Cost-of-living crisis 1 Severe commodity price shocks Costa Rica 1 Cost-of-living crisis 2 Debt crises 2 Geoeconomic confrontation 2 Debt crises 3 Rapid and/or sustained inflation 3 Interstate conflict 3 Breakdown of critical infrastructure 4 Natural disasters and extreme weather 5 Severe commodity supply crises events 4 Rapid and/or sustained inflation 5 Severe commodity price shocks 5 Rapid and/or sustained inflation 5 Natural disasters and extreme weather 5 Cost-of-living crisis events Ecuador 1 Prolonged economic stagnation Côte d'Ivoire Finland 1 Cost-of-living crisis 2 Digital inequality 1 Geoeconomic confrontation 2 Debt crises 3 Natural disasters and extreme weather 2 Prolonged economic stagnation events 3 Terrorist attacks 3 Employment and livelihood crises 3 Severe commodity price shocks 4 Rapid and/or sustained inflation 5 State collapse 4 Interstate conflict 5 Failure of cybersecurity measures 4 Rapid and/or sustained inflation Egypt 1 Debt crises Cyprus France 1 Rapid and/or sustained inflation 2 Rapid and/or sustained inflation 1 Debt crises 2 Cost-of-living crisis 3 Cost-of-living crisis 2 Severe commodity price shocks 3 Failure of climate-change adaptation 4 Prolonged economic stagnation 3 Rapid and/or sustained inflation 3 Geoeconomic confrontation 5 Severe commodity price shocks 3 Cost-of-living crisis 5 Severe commodity supply crises 3 Erosion of social cohesion Czechia 1 Rapid and/or sustained inflation 2 Severe commodity supply crises 3 Severe commodity price shocks 4 Geopolitical contestation of resources 5 Interstate conflict Risk categories Economic Environmental Geopolitical Societal Technological Global Risks Report 2023 82
TABLE B.2 Top five risks identified by the Executive Opinion Survey (EOS) Georgia Guatemala Hungary 1 Cost-of-living crisis 1 Natural disasters and extreme weather 1 Rapid and/or sustained inflation events 2 Interstate conflict 2 Collapse of services and public 2 Cost-of-living crisis infrastructure 3 Geoeconomic confrontation 3 Prolonged economic stagnation 3 Asset bubble burst 3 Digital power concentration 4 State collapse 4 Natural disasters and extreme weather events 5 Rapid and/or sustained inflation 5 Digital inequality 4 Breakdown of critical infrastructure Germany Honduras India 1 Rapid and/or sustained inflation 1 Rapid and/or sustained inflation 1 Digital inequality 2 Severe commodity price shocks 2 Natural disasters and extreme weather 2 Geopolitical contestation of resources events 3 Interstate conflict 3 State collapse 3 Cost-of-living crisis 4 Severe commodity supply crises 4 Employment and livelihood crises 4 Debt crises 4 Geopolitical contestation of resources 5 Cost-of-living crisis 5 Natural disasters and extreme weather events Ghana Hong Kong SAR, China Indonesia 1 Debt crises 1 Geoeconomic confrontation 1 Debt crises 2 Cost-of-living crisis 2 Prolonged economic stagnation 2 Interstate conflict 3 Human-made environmental damage 3 Asset bubble burst 2 Rapid and/or sustained inflation 4 Employment and livelihood crises 4 Cost-of-living crisis 4 Digital inequality 5 Failure of cybersecurity measures 5 Infectious diseases 5 Geopolitical contestation of resources Greece Hungary Ireland 1 Cost-of-living crisis 1 Rapid and/or sustained inflation 1 Rapid and/or sustained inflation 2 Severe commodity price shocks 2 Infectious diseases 2 Cost-of-living crisis 2 Rapid and/or sustained inflation 3 Geoeconomic confrontation 3 Geoeconomic confrontation 4 Debt crises 4 Cost-of-living crisis 4 Severe commodity price shocks 5 Interstate conflict 5 Natural disasters and extreme weather 5 Failure of climate-change adaptation events 5 Geoeconomic confrontation 5 Severe commodity price shocks Risk categories Economic Environmental Geopolitical Societal Technological Global Risks Report 2023 83
TABLE B.2 Top five risks identified by the Executive Opinion Survey (EOS) Israel Jordan Kuwait 1 Cost-of-living crisis 1 Debt crises 1 Rapid and/or sustained inflation 2 Terrorist attacks 2 Severe commodity supply crises 1 Cost-of-living crisis 3 Interstate conflict 2 Cost-of-living crisis 3 Severe commodity price shocks 4 Geoeconomic confrontation 4 Severe commodity price shocks 4 Human-made environmental damage 5 Asset bubble burst 5 Employment and livelihood crises 4 Interstate conflict Italy Kazakhstan Kyrgyzstan 1 Debt crises 1 Geoeconomic confrontation 1 Interstate conflict 2 Interstate conflict 2 Rapid and/or sustained inflation 2 Debt crises 2 Rapid and/or sustained inflation 3 Geopolitical contestation of resources 3 State collapse 4 Failure of climate-change adaptation 4 Interstate conflict 4 Severe commodity supply crises 5 Asset bubble burst 5 Severe commodity price shocks 5 Infectious diseases Jamaica Kenya Lao PDR 1 Rapid and/or sustained inflation 1 Debt crises 1 Rapid and/or sustained inflation 2 Cost-of-living crisis 2 Cost-of-living crisis 2 Severe commodity price shocks 3 Natural disasters and extreme weather 3 Employment and livelihood crises 3 Infectious diseases events 4 Proliferation of illicit economic activity 4 Geopolitical contestation of resources 4 Cost-of-living crisis 5 Severe commodity price shocks 5 Failure of climate-change adaptation 5 Employment and livelihood crises Japan Kosovo Latvia 1 Geoeconomic confrontation 1 Human-made environmental damage 1 Rapid and/or sustained inflation 2 Natural disasters and extreme weather 1 Rapid and/or sustained inflation 2 Interstate conflict events 3 Prolonged economic stagnation 1 Cost-of-living crisis 3 Cost-of-living crisis 4 Severe commodity price shocks 4 Geoeconomic confrontation 4 Employment and livelihood crises 5 Geopolitical contestation of resources 5 Failure of cybersecurity measures 5 Debt crises 5 Digital inequality Risk categories Economic Environmental Geopolitical Societal Technological Global Risks Report 2023 84
TABLE B.2 Top five risks identified by the Executive Opinion Survey (EOS) Lesotho Malaysia Mexico 1 Geopolitical contestation of resources 1 Cost-of-living crisis 1 Rapid and/or sustained inflation 2 Collapse of services and public 2 Rapid and/or sustained inflation 2 Proliferation of illicit economic activity infrastructure 3 Digital inequality 3 Debt crises 2 Prolonged economic stagnation 4 Collapse of a systemically important industry 4 Geoeconomic confrontation 4 State collapse 5 Proliferation of illicit economic activity 5 Human-made environmental damage 4 Erosion of social cohesion 5 Severe commodity supply crises Liberia Mongolia 1 Cost-of-living crisis 5 Severe commodity price shocks 1 Debt crises 2 Rapid and/or sustained inflation 5 Prolonged economic stagnation 2 Human-made environmental damage 3 Prolonged economic stagnation 5 Failure of cybersecurity measures 3 Geoeconomic confrontation 4 Employment and livelihood crises 4 Employment and livelihood crises Mali 5 Proliferation of illicit economic activity 1 Geopolitical contestation of resources 5 Interstate conflict 2 Employment and livelihood crises Lithuania Montenegro 1 Severe commodity price shocks 3 Geoeconomic confrontation 1 Cost-of-living crisis 2 Interstate conflict 4 Terrorist attacks 2 Geoeconomic confrontation 3 Rapid and/or sustained inflation 5 Breakdown of critical infrastructure 3 Prolonged economic stagnation 4 Geoeconomic confrontation 4 Failure of climate-change adaptation Malta 5 Severe commodity supply crises 1 Cost-of-living crisis 5 Human-made environmental damage 2 Human-made environmental damage 5 Severe commodity supply crises Luxembourg 1 Rapid and/or sustained inflation 3 Rapid and/or sustained inflation 5 Debt crises 2 Cost-of-living crisis 4 Severe commodity price shocks 5 Employment and livelihood crises 3 Severe commodity price shocks 5 Digital inequality Morocco 4 Severe commodity supply crises 1 Cost-of-living crisis Mauritius 5 Geoeconomic confrontation 1 Cost-of-living crisis 2 Rapid and/or sustained inflation 2 Debt crises 2 Severe commodity price shocks Malawi 1 Debt crises 3 Rapid and/or sustained inflation 4 Severe commodity supply crises 2 Cost-of-living crisis 4 Natural disasters and extreme weather 5 Debt crises events 3 Prolonged economic stagnation 5 Severe commodity price shocks 4 Rapid and/or sustained inflation 5 Failure of climate-change adaptation Risk categories Economic Environmental Geopolitical Societal Technological Global Risks Report 2023 85
TABLE B.2 Top five risks identified by the Executive Opinion Survey (EOS) Namibia Nigeria Panama 1 Debt crises 1 Terrorist attacks 1 Employment and livelihood crises 2 Cost-of-living crisis 2 Debt crises 2 Debt crises 3 Employment and livelihood crises 3 Cost-of-living crisis 3 Digital inequality 5 Failure of climate-change adaptation 4 Severe commodity supply crises 4 Cost-of-living crisis 5 Prolonged economic stagnation 5 Rapid and/or sustained inflation 5 Proliferation of illicit economic activity 5 Digital inequality 5 Employment and livelihood crises 5 Rapid and/or sustained inflation Nepal North Macedonia Paraguay 1 Geopolitical contestation of resources 1 Cost-of-living crisis 1 Prolonged economic stagnation 2 Debt crises 2 Debt crises 2 Collapse of services and public infrastructure 3 Human-made environmental damage 3 Human-made environmental damage 2 Digital inequality 4 Natural disasters and extreme weather 4 Rapid and/or sustained inflation 4 Natural disasters and extreme weather events events 5 Digital inequality 5 Prolonged economic stagnation 5 State collapse Netherlands Oman Peru 1 Failure of climate-change adaptation 1 Debt crises 1 State collapse 2 Rapid and/or sustained inflation 2 Natural disasters and extreme weather 2 Digital inequality events 3 Geoeconomic confrontation 3 Severe commodity price shocks 3 Rapid and/or sustained inflation 3 Geopolitical contestation of resources 3 Cost-of-living crisis 4 Proliferation of illicit economic activity 5 Cost-of-living crisis 5 Geopolitical contestation of resources 5 Employment and livelihood crises 5 Proliferation of illicit economic activity New Zealand Philippines 1 Cost-of-living crisis 1 Natural disasters and extreme weather Pakistan events 2 Rapid and/or sustained inflation 1 Digital power concentration 2 Debt crises 3 Natural disasters and extreme weather 2 Failure of cybersecurity measures 3 Rapid and/or sustained inflation events 4 Asset bubble burst 3 Rapid and/or sustained inflation 4 Misinformation 5 Debt crises 4 Debt crises 5 Geopolitical contestation of resources 5 State collapse Risk categories Economic Environmental Geopolitical Societal Technological Global Risks Report 2023 86
TABLE B.2 Top five risks identified by the Executive Opinion Survey (EOS) Poland Rwanda Sierra Leone 1 Rapid and/or sustained inflation 1 Rapid and/or sustained inflation 1 Cost-of-living crisis 2 Breakdown of critical infrastructure 1 Cost-of-living crisis 2 Rapid and/or sustained inflation 3 Geoeconomic confrontation 3 Severe commodity price shocks 3 Debt crises 4 Employment and livelihood crises 4 Natural disasters and extreme weather 4 Natural disasters and extreme weather events events 5 Interstate conflict 5 Interstate conflict 4 State collapse 4 Employment and livelihood crises Portugal Saudi Arabia 1 Rapid and/or sustained inflation 1 Cost-of-living crisis 4 Digital inequality 2 Cost-of-living crisis 2 Interstate conflict Singapore 3 Debt crises 3 Rapid and/or sustained inflation 1 Geoeconomic confrontation 4 Severe commodity price shocks 4 Severe commodity price shocks 2 Rapid and/or sustained inflation 5 Prolonged economic stagnation 4 Breakdown of critical infrastructure 3 Severe commodity supply crises 4 Failure of cybersecurity measures 4 Severe commodity price shocks Qatar 1 Cost-of-living crisis 5 Cost-of-living crisis Senegal 2 Natural disasters and extreme weather 1 Cost-of-living crisis events Slovakia 2 Geoeconomic confrontation 2 Debt crises 1 Rapid and/or sustained inflation 4 Geopolitical contestation of resources 2 Employment and livelihood crises 2 Severe commodity price shocks 4 Severe commodity price shocks 4 Rapid and/or sustained inflation 3 Severe commodity supply crises 4 Rapid and/or sustained inflation 5 Severe commodity supply crises 4 Asset bubble burst 4 Failure of cybersecurity measures 4 Interstate conflict Serbia 1 Geoeconomic confrontation Romania Slovenia 1 Rapid and/or sustained inflation 1 Severe commodity price shocks 1 Severe commodity price shocks 2 Geoeconomic confrontation 3 Interstate conflict 2 Geoeconomic confrontation 3 Interstate conflict 4 Cost-of-living crisis 3 Rapid and/or sustained inflation 4 Severe commodity price shocks 5 Asset bubble burst 4 Severe commodity supply crises 4 Cost-of-living crisis 5 Severe commodity supply crises 5 Geopolitical contestation of resources Risk categories Economic Environmental Geopolitical Societal Technological Global Risks Report 2023 87
TABLE B.2 Top five risks identified by the Executive Opinion Survey (EOS) South Africa Sweden Trinidad and Tobago 1 State collapse 1 Rapid and/or sustained inflation 1 Cost-of-living crisis 2 Debt crises 2 Cost-of-living crisis 2 Digital inequality 2 Collapse of services and public 3 Debt crises 3 Severe commodity supply crises infrastructure 2 Cost-of-living crisis 4 Failure of climate-change adaptation 3 Rapid and/or sustained inflation 5 Employment and livelihood crises 5 Terrorist attacks 5 Widespread youth disillusionment 5 Geoeconomic confrontation South Korea Tunisia 1 Rapid and/or sustained inflation 5 Collapse of a systemically important industry 1 Debt crises 2 Proliferation of illicit economic activity 2 State collapse Switzerland 3 Severe commodity supply crises 1 Severe commodity price shocks 3 Severe commodity supply crises 3 Severe commodity price shocks 2 Severe commodity supply crises 4 Cost-of-living crisis 5 Asset bubble burst 3 Geoeconomic confrontation 5 Rapid and/or sustained inflation 5 Debt crises 3 Rapid and/or sustained inflation Türkiye 5 Natural disasters and extreme weather 1 Rapid and/or sustained inflation Spain events 1 Rapid and/or sustained inflation 5 Geopolitical contestation of resources 2 Employment and livelihood crises 2 Debt crises 5 Breakdown of critical infrastructure through 3 Interstate conflict cyber attacks 3 Cost-of-living crisis 4 Severe commodity supply crises Taiwan, China 4 Employment and livelihood crises 1 Geoeconomic confrontation 5 Debt crises 5 Geopolitical contestation of resources 2 Rapid and/or sustained inflation 5 Severe commodity price shocks 5 Proliferation of illicit economic activity 3 Infectious diseases Ukraine 4 Natural disasters and extreme weather 1 Severe commodity supply crises Sri Lanka events 1 Debt crises 4 Severe commodity price shocks 2 Interstate conflict 2 Cost-of-living crisis 3 Large-scale involuntary migration Thailand 3 State collapse 1 Debt crises 3 Failure of cybersecurity measures 3 Rapid and/or sustained inflation 2 Cost-of-living crisis 5 Automation and displacement of jobs 5 Severe commodity supply crises 3 Human-made environmental damage 4 Digital inequality 5 Geoeconomic confrontation Risk categories Economic Environmental Geopolitical Societal Technological Global Risks Report 2023 88
TABLE B.2 Top five risks identified by the Executive Opinion Survey (EOS) United Arab Emirates Uruguay Zambia 1 Cost-of-living crisis 1 Severe commodity price shocks 1 Debt crises 2 Rapid and/or sustained inflation 2 Rapid and/or sustained inflation 2 Cost-of-living crisis 3 Severe commodity price shocks 3 Prolonged economic stagnation 3 Failure of climate-change adaptation 4 Geopolitical contestation of resources 3 Cost-of-living crisis 4 Geopolitical contestation of resources 5 Geoeconomic confrontation 5 Automation and displacement of jobs 5 Failure of climate-change mitigation 5 Failure of cybersecurity measures Venezuela (Bolivarian Republic of) Zimbabwe 1 Severe commodity supply crises 1 Rapid and/or sustained inflation United Kingdom of Great Britain 1 Cost-of-living crisis 2 Collapse of services and public 2 Cost-of-living crisis infrastructure 2 Debt crises 3 State collapse 3 Geoeconomic confrontation 3 Rapid and/or sustained inflation 3 Rapid and/or sustained inflation 4 Collapse of services and public infrastructure 4 Failure of climate-change adaptation 5 Geoeconomic confrontation 5 Severe commodity supply crises 5 Terrestrial biodiversity loss and ecosystem 5 Prolonged economic stagnation collapse 5 Interstate conflict 5 Digital inequality 5 Asset bubble burst Viet Nam 1 Rapid and/or sustained inflation United Republic of Tanzania 1 Rapid and/or sustained inflation 2 Infectious diseases 2 Debt crises 3 Geopolitical contestation of resources 3 Employment and livelihood crises 4 Natural disasters and extreme weather events 4 Geopolitical contestation of resources 5 Failure of cybersecurity measures 4 Cost-of-living crisis Yemen 1 Severe commodity supply crises United States of America 1 Debt crises 2 Collapse of services and public infrastructure 2 Rapid and/or sustained inflation 3 State collapse 3 Geoeconomic confrontation 4 Breakdown of critical infrastructure 4 Cost-of-living crisis 5 Proliferation of illicit economic activity 5 Failure of climate-change adaptation Risk categories Economic Environmental Geopolitical Societal Technological Global Risks Report 2023 89
Partner Institutes The World Economic Forum’s Centre for the New Economy and Society is pleased to acknowledge and thank the following organizations as its valued Partner Institutes: Albania Bangladesh Institute for Contemporary Studies, Tirana Centre for Policy Dialogue - CPD Business University and College Dr Fahmida Khatun, Executive Director Helton Cevi, Project Coordinator Dr Khondaker Golam Moazzem, Research Director Artan Hoxha, President of ISB and Administrator of Ratia Rehnuma, Research Associate TBU Chowdhury Fariha, Research Intern Oltjon Valisi, Assistant Project Coordinator Barbados Algeria University of West Indies Centre de Recherche En Economie Appliquée Jonathan G. Lashley, Senior Fellow Pour Le Développement - CREAD Don Marshall, Professor Yacine Belarbi, Director Kenisha Chase, Research Assistant Khaled Menna, Director of Macroeconomics and Economic Integration Benin Institut de Recherche Empirique en Economie Angola Politique - IREEP Jobartis Leonard Wantchekon, President João Freitas, Country Manager Stéphania Houngan, Research Associate Luis Verdeja, Director Plurinational State of Bolivia, Costa Rica, Argentina Dominican Republic, El Salvador, Honduras, IAE Business School, Universidad Austral Panama Eduardo Fracchia, Director of Academic Department INCAE Business School of Economics Ronald Arce, Researcher Martin Calveira, Research Economist Enrique Bolaños, President Octavio Martínez, Director Armenia Economy and Values Research Center Bosnia and Herzegovina Sevak Hovhannisyan, Board Member and Senior School of Economics and Business, University of Associate Sarajevo Jasmina Selimovic, Dean Australia, Belgium, Canada, Indonesia, Italy, Zlatko Lagumdzija, Professor Sweden, United Kingdom, United States Amra Kapo, Associate Professor Dynata Thomas Huff, Senior Project Manager Botswana Steffen Bott, Vice President, Sales Botswana National Productivity Centre Valentyna Chuikina, Associate Account Director Letsogile Batsetswe, Research Consultant and Statistician Austria Zelda Okatch, Information and Research Services Austrian Institute of Economic Research - WIFO Manager Gabriel Felbermayr, Director Christopher Diswai, Executive Director Michael Peneder, Project Lead Alexandros Charos, Survey Expert Brazil Fundação Dom Cabral Bahamas, The Carlos Arruda, Professor of Innovation and The Government and Public Policy Institute, Competitiveness University of the Bahamas Hugo Tadeu, Professor of Innovation Zhivargo Laing, Executive Director Miguel Costa, Research Assistant Jeannie D. Gibson, Policy Assistant Bulgaria Bahrain Center for Economic Development Bahrain Economic Development Board Maria Prohaska, Director Khalid Humaidan, Chief Executive Ivalina Simeonova, Project Manager Nada Al-Saeed, Executive Director Rima AlKilani, Executive Director Fatema Alatbi, Senior Executive Sara Ishaq, Senior Executive Global Risks Report 2023 90
Cambodia Ramatou Fall, Director of Business Climate Nuppun Research and Consulting Co., Ltd Simon Meledje, Head of Planning and Monitoring Pisey Khin, Director Bernadine Yeble N'Guessan, Research of昀椀cer Chanthan Tha, Researcher Dalen Vyla, Research Assistant Cyprus Cyprus Employers and Industry Confederation - Cameroon OEB Compétitivité Cameroon Antonis Frangoudis, Director Business Development Hermann Fotie Ii, Permanent Secretary and Economic Affairs Department Tanankem Belmondo Voufo, Expert Investment Bank of Cyprus Climate Kyriacos Antoniou, Governance Of昀椀cer Jean Baptiste Nsoe Nkouli, Competitiveness Andreas Alexandrou, Manager Strategy and Observatory Expert Customer Insights Cambodia Czech Republic Nuppun Research and Consulting Co., Ltd CMC Graduate School of Business Khin Pisey, Managing Director Tomáš Janča, Executive Director Pong Vanny, Researcher Kimhong Sin, Research Assistant Denmark Danish Technological Institute Cape Verde Stig Yding Sørensen, Senior Specialist INOVE Research Andreas Bjerre Lunkeit, Consultant Frantz Tavares, Chief Executive Of昀椀cer Jerónimo Freire, Project Manager Ecuador Júlio Delgado, Director ESPAE Graduate School of Management - ESPOL Chad Sara Wong, Professor Groupe de Recherches Alternatives Et de Tania Tenesaca, Project Coordinator Monitoring Du Projet Pétrole-Tchad-Cameroun Xavier Ordeñana, Dean Simael Mbairassem, Economist in charge of Jack Zambrano, Research Assistant Research and Public Policies Maoundonodji Gilbert, Managing Director Egypt Egyptian Center for Economic Studies - ECES Chile Abla Abdel Latif, Executive Director, and Director of School of Government, University Adolfo Ibañez Research Carolina Apablaza, Director Salma Bahaa El Din, Senior Economist Patricio Aroca, Professor Ahmed Maged, Research Assistant Isabella Cuneo, Doctoral Student Hossam Khater, Research Assistant Mohamed Khater, Research Assistant China Dataway Horizon Estonia Lingling Qiao, General Manager Estonian Institute of Economic Research -EKI Yuming Zhi, Research Director Marje Josing, Director Zhuyu Yao, Senior Project Manager Finland Colombia ETLA Research Institute of the Finnish Economy National Planning Department of Colombia Aki Kangasharju, Managing Director Consejo Privado de Competitividad Päivi Puonti, Head of Forecasting Jorge Ivan Gonzalez, General Director, Department Ville Kaitila, Researcher of National Planning Camilo Rivera Perez, Technical Director, Innovation France and Private Sector Development Business France Sara Patricia Rivera, Adviser, Innovation and Private RCassagnes Louise, Economist Sector Development Marcias Manuel, Head of Service : Economic studies Congo, Democratic Republic of Congo-Invest Consulting Georgia Teza Bila Minlangu, Administrator TSU Center for Analysis and Forecasting Faila Tabu Ngandi, Managing Director Vakhtang Charaia, Director Bertin Muderhwa, Head of Service in charge Otar Anguridze, Head of the Board of Studies and Statistics at the Federation of Shota Gulbani, Expert Businesses of Congo Mariam Lashkhi, Project Manager Mamuka Tsereteli, Expert Côte d'Ivoire Centre de Promotion des Investissements en Côte D’ivoire - CEPICI Solange Amichia, CEO Global Risks Report 2023 91
Germany Shulette Cox, Vice President, Research, Advocacy, Institute for Innovation and Technology within the and Project Implementation VDI/VDE Innovation + Technik GmbH National Competitiveness Council Jamaica Michael Nerger, Project Leader Sharifa Powell, Consultant Project Manager Ghana Japan Association of Ghana Industries Waseda University Yaw Adu-Gyam昀椀, President Jusuke Ikegami, Professor Seth Twum-Akwaboah, Chief Executive Of昀椀cer Mitsuyo Tsubayama, Coordinator John Defor, Direcctor, Policy and Research Shoko Miya, Coordinator Greece Jordan SEV Hellenic Federation of Enterprises Ministry of Planning and International Michael Mitsopoulos, Director - Business Cooperation of Jordan Environment and Regulatory Affairs Hadram Al Fayes, Director Athanasios Printsipas, Senior Advisor - SEV Ghada Issa, Head of Competitiveness Division Business Council for Sustainable Development Thamer Masarweh, Researcher Guatemala Kazakhstan FUNDESA Center for Strategic Initiatives LPP Juan Carlos Paiz, President of the Board of Directors Olzhas Khudaibergenov, Senior Partner Juan Carlos Zapata, Chief Executive Of昀椀cer Yerbol Tulegenov, Associate Partner Fernando Spross, Associate Researcher Symbat Aliaskarova, Consultant Priscilla González, Corporate Affairs Coordinator Kenya Hong Kong SAR, China University of Nairobi Hong Kong General Chamber of Commerce Karuti Kanyinga, Research Professor and Director, Simon Ngan, Director, Policy and Research IDS Wilson Chong, Senior Economist Vincent Mugo, Project Assistant IDS Paul Kamau, Associate Research Professor, IDS Hungary KOPINT-TÁRKI Economic Research Ltd Kosovo*, North Macedonia Peter Vakhal, Senior Research Associate Economic Chamber of North-West Macedonia Éva Palócz, CEO Drilon Iseni, Executive Director Durim Zekiri, Operations Manager Iceland Miranda Ajdini, Legal associate The Icelandic Centre for Future Studies Karl Friðriksson, Manager Director Kuwait Kuwait University India Fahad Al-Rashid, Committee Chair LeadCap Knowledge Solutions Pvt Ltd - Adel Al-Husainan, Committee Member LeadCap Ventures Majed Jamal Al-Deen, Committee Member Sangeeth Varghese, Managing Director and CEO Vidyadhar Prabhudesai, Director and COO Kyrgyzstan Economic Policy Institute Ireland Marat Tazabekov, Chairman Irish Business and Employers Confederation - Lola Abduhametova, Coordinator IBEC Irina Kandybko, Manager Geraldine Anderson, Head of Research Lao PDR Israel Enterprise and Development Consultants Co. Manufacturers' Association of Israel - MAI Ltd - EDC Ron Tomer, President Buakhai Phimmavong, Managing Partner Ruby Ginel, CEO Thipphasone Inthachack, Of昀椀ce administrator Dan Catarivas, General Manager, Foreign Trade and International Relations Division Latvia Itai Nakash, Deputy General Manager, Foreign Trade Stockholm School of Economics in Riga and International Relations Division Arnis Sauka, Head of the Centre for Sustainable Development Jamaica Mona School of Business and Management - Lesotho MSBM, The University of the West Indies, Mona Private Sector Foundation of Lesotho - PSFL David McBean, Executive Director Thabo Qhesi, CEO Franklin Johnston, Director Bokang Tsoanamatsie, Public Relations Of昀椀cer Yvette Cameron-Harris, Project Administrator Qothoase Khofane, Researcher Jamaica Promotions Corporation - JAMPRO Global Risks Report 2023 92
Liberia, Sierra Leone Mongolia GQRDOTCOM Limited - GQR Open Society Forum - OSF Omodele Jones, Chief Executive Of昀椀cer Erdenejargal Perenlei, Executive Director Oyunbadam Davaakhuu, Program Manager Lithuania Innovation Agency Lithuania Montenegro Jone Kalendiene, Head of Research and Analysis The Institute for Strategic Studies and Prognoses Division - ISSP Irena Karelina, Analyst Maja Drakic Grgur, Project Coordinator Veselin Vukotic, President Luxembourg Luxembourg Chamber of Commerce Morocco Christel Chatelain, Director of the Economic Affairs The Policy Centre for the New South Department Dr Karim El Aynaoui, Executive President Jean-Baptiste Nivet, Sr Economist Asmaa Tahraoui, Senior Knoweldge Manager Sidonie Paris, Economist Abdelaaziz Ait Ali, Head Economics Research Department Malawi Malawi Confederation of Chambers of Mozambique Commerce and Industry African Centre for Economic Transformation Chancellor Kaferapanjira, Chief Executive (ACET) Madalitso Kazembe, Director, Business Environment John Asafu Adjaye, Senior Fellow - Economic and Policy Advocacy Management and Governance Program Manfred Maguru, Economic Analyst Edward Brown, Senior Director, Research & Policy Chancy Mkandawire, Economic Analyst Engagements Confederation of Business Associations of Malaysia Mozambique Malaysia Productivity Corporation Roque Magaia, Economist Dato' Abdul Latif Abu Seman, Director General Zahid Ismail, Deputy Director General Namibia Dr Mazrina Mohamed Ibramsah, Deputy Director Institute for Public Policy Research - IPPR General Ndapunikwa Fikameni, Research Associate Wan Fazlin Nadia Wan Osman, Director Salmi Shigwedha, Research Associate Graham Hopwood, Director Mali Mali Applied and Theoretical Economics Nepal Research Group - GREAT Competitiveness and Development Institute - Massa Coulibaly, Executive Director CODE Wélé Fatoumata Binta Sow, Researcher Dr Ramesh C. Chitrakar, Project Director/ Country Badiégué Diallo, Administrative and Financial Coordinator Assistant Abhinandan Baniya, Associate Team Member Menaka Shrestha, Team Member Malta Netherlands Competitive Malta - Foundation for National Amsterdam Centre for Business Innovation, Competitiveness University of Amsterdam Adrian Said, Associate Henk Volberda, Director and Professor Matthew Castillo, Associate Kevin Heij, Senior Innovation Researcher Pieter van den Brink, Research Assistant Mauritius Nina Versluijs, Research Assistant Economic Development Board Jochem Bouman, Research Assistant Sanroy Seechurn, Head of Department Ken Poonoosamy, CEO New Zealand Dooshala Ramjutun-Ramlaul, Manager BusinessNZ Kirk Hope, CEO Mexico Kathryn Asare, Manager Communications Instituto Mexicano para la Competitividad - IMCO Nigeria Valeria Moy, General Director Nigerian Economic Summit Group - NESG Ivania Mazari, Program Manager Laoye Jaiyeola, Chief Executive Of昀椀cer Ministry of the Economy Dr Olusegun Omisakin, Director of Research and Jorge Eduardo Arreola Cavazos, General Director for Development Competitiveness and Competition Sodik Olo昀椀n, Economist Carlos Rubén Altamirano Márquez, Director Fernando Tonatiuh Parra Calvo, Underdirector for Competitiveness Global Risks Report 2023 93
Oman Rwanda National Competitiveness Of昀椀ce - NCO Rwanda Development Board Dr Salim Abdullah Al Shaikh, Acting Chief of NCO Delphine Uwase, Ag. Head of Strategy and Juhaina Saleh Al Balushi, Economic Researcher Competitiveness Department Jawaher Sultan Al Habsi, Business Analyst Kennedy Kalisa, Strategy Analyst Richard Kayibanda, Ag. Chief Strategy and Pakistan Compliance Of昀椀cer Mishal Pakistan Amir Jahangir, Chief Executive Of昀椀cer Saudi Arabia Puruesh Chaudhary, Director Alfaisal University Amna Sabahat Bhutta, Director Mohammed Kafaji, Vice Dean for Quality Assurance and Accreditation Paraguay National Competitiveness Centre Paraguayan Foundation for Cooperation and Eiman Habbas Al-Mutairi, CEO of the National Development Competitiveness Centre Martin Burt, CEO Waleed Al-Rudaian, Deputy CEO of the National Luis Fernando Sanabria, CEO Competitiveness Centre Sol Urbieta, Management Assistant Salman Al-Tukhai昀椀, General manager Abdulrahman M. Al-Ghamdi, Project Manager Peru Industrial Development Center of the National Senegal Society of Industries Université Cheikh Anta Diop of Dakar Luis Tenorio, Executive Director Thierno Thioune, Directeur du Centre de Recherches Maria Elena Baraybar, Project Assistant Economiques Appliquées Benoni Sanchez, Head of Systems Serbia Philippines Foundation for the Advancement of Economics Makati Business Club - MBC - FREN Roxanne Lu, Programs Director Aleksandar Radivojević, Coordinator Trisha Teope, Foreign Programs Of昀椀cer Dejan Molnar, Director Poland Singapore National Bank of Poland Singapore Economic Development Board Piotr Boguszewski, Economic Advisor Cheng Wai San, Director and Head Piotr Szpunar, Director Teo Xinyu, Executive Of昀椀cer, Senior Portugal Slovakia Business Administrators Forum - FAE Business Alliance of Slovakia - PAS Paulo Carmona, President Peter Serina, Executive Director Mariana Marques dos Santos, Member of the Board Robert Kičina, Member of the Board PROFORUM Association for the Development of Engineering Slovenia Ilidio De Ayala Serôdio, Vice-President Institute for Economic Research Helena Roquette, Secretary Peter Stanovnik, Professor Sonja Uršič, Senior Research Assistant Qatar University of Ljubljana, Faculty of Economics Qatari Businessmen Association - QBA Mateja Drnovšek, Full Professor Social and Economic Survey Research Institute, Qatar University South Africa Issa Abdull Salam Abu Issa, Secretary General Business Unity South Africa Sarah Abdallah, Deputy General Manager Tyson Thamsanqa Sibanda, Economic Policy Maria Jusay, Executive Secretary Manager Prof. Kaltham Al Ghanim, Director, Social and Olivier Serrao, Economic Policy Executive Director Economic Survey Research Institute Cas Coovadia, Chief Executive Of昀椀cer Raymond Carasig, Senior Survey Support Specialist South Korea Romania Korea Development Institute Association for Women Entrepreneurship Inho Song, Executive Director, Economic Information Development - ADAF and Education Center The Chamber of Commerce and Industry of Joohee Cho, Head, Public Opinion Analysis Unit Romania Boyoung Han, Senior Reseach Associate, Public Rotaru Cornelia, President Opinion Analysis Unit Rotaru Gela, Business Analyst Savu Cristina, Communication Expert Global Risks Report 2023 94
Spain Ukraine IESE Business School CASE Ukraine, Center for Social and Economic Pascual Berrone, Professor, Director of the Research International Center for Competitiveness Dmytro Boyarchuk, Executive Director María Luisa Blázquez, Research Associate Vladimir Dubrovskiy, Leading Economist Oksana Kuziakiv, Senior Adviser Sri Lanka Institute of Policy Studies of Sri Lanka - IPS United Arab Emirates Kithmina Hewage, Research Economist Federal Competitiveness and Statistics Centre Tharindu Udayanga, Research Assistant Hanan Ahli, Director General of Federal Competitiveness and Statistics Centre Switzerland Rashed Abdulkarim Al Blooshi, Undersecretary of University of St.Gallen, Center for Financial Department of Economic Development, Abu Dhabi Services Innovation Hend Abdulla, Analyst Tobias Trütsch, Managing Director Uruguay Taiwan, China Universidad ORT Uruguay Taiwan Institute of Economic Research Isidoro Hodara, Professor Chen, Yi-Man, Research Fellow Bruno Gili, Professor Tsuo, I-Chun, Assistant Research Fellow Federico Monetti, Professor Tanzania Bolivarian Republic of Venezuela REPOA Ltd Venezuelan Council for Investment Promotion Donald Mmari, Executive Director Jennyn Osorio, Economics Affairs Manager Lucas Katera, Director of Collaborations and Jorge García, Business Intelligence Manager Capacity Building Cornel Jahari, Researcher and Field Manager Viet Nam Ho Chi Minh City Institute for Development Thailand Studies - HIDS Chulalongkorn Business School Tran Hoang Ngan, Director Kanyarat (Lek) Sanoran, Assistant Professor and Trieu Thanh Son, Head of Rereach Management Assistant Dean at Dean's Of昀椀ce Nguyen Manh Quan, Researcher Wilert Puriwat, Professor and Dean Nat Kulvanich, Assistant Professor Yemen Yemeni Business Club - YBC Trinidad and Tobago Fathi Abdulwase Hayel Saeed, Chairman Arthur Lok Jack Global School of Business Ghadeer Ahmed Almaqha昀椀, Executive Director Raynardo Hassanally, Alumni Relations Coordinator Safa Abdullah Alsayaghi, Projects Manager Balraj Kistow, Programme Director Ron Sookram, Academic Coordinator Zambia University of Zambia Tunisia Joseph Simbaya, Director Institut Arabe des Chefs d’Entreprises Chitalu Chama Chiliba, Assistant Director and Senior Majdi Hassen, Executive Director Research Fellow Hager KARAA, Head of Studies Department Patricia Funjika, Research Fellow Türkiye Zimbabwe TÜSIAD, Sabanci University Competitivness National Competitiveness Commission Forum - REF Phillip Phiri, Executive Director Esra Durceylan Kaygusuz, Director Brighton Shayanewako, Director, Competitiveness Sezen Uğurlu Sum, Project Specialist Douglas Muzimba, Chief Economist, International Competitiveness Elizabeth Magwaza, Economist Global Risks Report 2023 95
January 2023 Global Risks Report 2023 Acknowledgements Contributors Sophie Heading Lead, Global Risks Saadia Zahidi Managing Director, World Economic Forum At the World Economic Forum, a debt of gratitude is owed to Professor Klaus Schwab (Founder and Executive Chairman) and Børge Brende (President), under whose guidance this report has been produced. This report has relied heavily on the dedication and expertise of World Economic Forum colleagues: Attilio di Battista, Ellissa Cavaciuti-Wishart, Kateryna Karunska, Kevin Kohler, Ricky Li, Dorsey Lockhart, Gayle Markovitz, Cam Powers, Samuel Werthmüller, and Yann Zopf. We would like to thank our Strategic Partners, Marsh McLennan, and Zurich Insurance Group, and particularly John Doyle (President and Chief Executive Of昀椀cer, Marsh McLennan) and Mario Greco (Chief Executive Of昀椀cer, Zurich Insurance Group). Thanks also to Peter Giger (Group Chief Risk Of昀椀cer, Zurich Insurance Group) and Carolina Klint (Managing Director, Risk Management Leader Continental Europe, Marsh). Special gratitude is due to John Scott (Head of Sustainability Risks, Zurich Insurance Group) and Richard Smith-Bingham (Executive Director, Marsh McLennan Advantage) for their contributions throughout the planning and drafting of the report. The report has greatly bene昀椀ted from the insight and expertise of the members of the Global Risks Advisory Board: Rolf Alter (Hertie School of Governance), Gabriella Bucher (Oxfam), Sharan Burrow (International Trade Union Confederation), Winnie Byanyima (UNAIDS), Marie-Valentine Florin (International Risk Governance Center), Charles Godfray (Oxford Martin School), Al Gore (Generation Investment Management), Pascal Lamy (Jacques Delors Institute), Robert Muggah (Igarapé Institute), Moisés Naím (Carnegie Endowment for International Peace), Carlos Afonso Nobre (University of São Paulo), Naomi Oreskes (Harvard University), Jonathan D. Ostry (Georgetown University), Carol Ouko-Misiko (Institute of Risk Management), Eduardo Pedrosa (Paci昀椀c Economic Cooperation Council), Danny Quah (National University of Singapore), Daniel Ralph (Cambridge Centre for Risks Studies), Samir Saran (Observer Research Foundation), John Scott (Zurich Insurance Group), Richard Smith-Bingham (Marsh McLennan), Effy Vayena (Swiss Federal Institute of Technology Zurich), Charlotte Warakaulle (CERN), Beatrice Weder di Mauro (Graduate Institute Geneva), Ngaire Woods (University of Oxford) and Alexandra Zapata (New America). We would also like to thank SalesForce (Justine Moscatello, Director of Customer & Executive Engagement) and Lovelytics for the design of the interactive global risks data visualization. We also thank our Academic partners: the National University of Singapore, the Oxford Martin School at the University of Oxford and the University of Pennsylvania. Global Risks Report 2023 96
We are grateful to the following individuals from our Strategic Partners and Risk Communities. Marsh McLennan: Amy Barnes, Kate Bravery, Helga Birgden, Rico Brandenburg, Erica Davis, Missy DeAngelis, Bruno Dotti, Liz Elliot, Gunes Ergun, Guillermo Franco, Lorna Friedman, Jason Groves, Kavitha Hariharan, Ben Hoster, Rachel Juay, Marshall Lee, Paul Mee, Luca Moneta, Shilpa Pankaj, Maurizio Quintavalle, Deepakshi Rawat, Graeme Riddell, Nick Salter, Reid Sawyer, Ben Simpfendorfer, Toshin Sequeira, Swenja Surminski, Daniel Tannebaum, and Rupert Watson. Zurich Insurance Group: Paige Adams, Ines Bourbon, Laura Castellano, Matt Holmes, Stefan Kröp昀氀, Guy Miller, Pavel Osipyants, and Robert Wyse. Chief Risk Of昀椀cers Community: Fatma Al-Suwaidi (Qatar National Bank), Stacy Allen (Lord Abbott), Christian Bluhm (UBS AG), Brenda Boultwood (International Monetary Fund), Manoj Chawla (Emirates NBD), Adam Farber (Boston Consulting Group), Carlo Ferraresi (Generali), Sebastian Fritz-Morgenthal (Bain & Company Inc.), Peter Giger (Zurich Insurance Group), Jan Hansen (Novartis), Arun Hari (Gulf International Bank), Bahare Heywood (Clifford Chance LLP), Alfred Kibe (Mastercard), Giselle Lim (Takeda Pharmaceutical Company), Maria Martinez (McKinsey & Company), Domingo Mirón (Accenture), Jody Myers (US International Development Finance Corporation), Heike Niebergall-Lackner (International Committee of the Red Cross), Fiachre O'Neil (PayPal), Sarah Otte (Deloitte), Deepak Padaki (Infosys Limited), Hanne Raatikainen (Of昀椀ce of the United Nations High Commissioner for Refugees), Nidhi Seksaria (Mahindra Group), Taalib Shah (Barclays), Lakshmi Shyam-Sunder (World Bank), Richard Smith-Bingham (Marsh McLennan), Matthew Snyder (Centene Corporation), Iliyana Tsanova (European Commission), and Jacob van der Blij (GAVI). A special thanks to experts who contributed to our thematic consultations: Cindy Arnson (The Woodrow Wilson International Center for Scholars), Alison Bewick (Nestlé), Agnes Callamard (Amnesty International), Arne Cartridge (Yara), Era Dabla-Norris (IMF), David Edwards (Education International), Bridget Fawcett (Citi), Luca Gattinni (European Investment Bank), Florence Gaub (European Council), Charles Godfray (Oxford Martin School), Günter Hemrich (FAO), Anne Kreuger (John Hopkins School of Advanced International Studies), Charles North (Global Partnership for Education), Henk Ovink (Netherlands Government), Megan Palmer (Stanford University), Eric Parrado (InterAmerican Development Bank), Dan Rice (Walmart), Olaf Schulz (Nokia), Hersh Shah (Institute of Risk Management), Jen Sovada (SandboxAQ), Christian Spano (International Council of Mining and Metals), Richard Threlfall (KPMG), Andrew Williamson (Huawei Technologies), Ngaire Woods (University of Oxford), Eden Woon (Asian Institute of Technology). This report has relied on the expertise of our colleagues who contributed to our thematic consultations: Silja Baller, Filipe Beato, Emma Benameur, Kimberly Bennet, Felipe Bezamat, Morgan Booher, Kimberley Botwright, Sebastian Buckup, Gretchen Bueermann, Diego Bustamante, Kevin Doxzen, Liming Chen, Jaci Eisenberg, Genesis Elhussein, Kay Firth-Butter昀椀eld, Nancy Gillis, Fernando Gomez, Philipp Grosskurth, Guillaume Hingel, Rebecca Ivey, Ariel Kastner, Purushottam Kaushik, Rebecca King, Andrej Kirn, Benjamin Larsen, Espen Mehlum, Kelly McCain, Chido Munyati, Jayant Narayan, Kim Piaget, Jörgen Sandström, David Sangokoya, Miriam Schive, Grigory Shutko, Kristian Teleki, Federico Torti, Tim van den Bergh, Irene Varoli and Eric White. We are grateful to the following colleagues for their time and help in review: Sean de Cleene, Daniel Dobrygowski, Abdellah Hmamouche, Anis Nassar, Supheakmungkol Sarin, Tania Strauss, Alessandro Valentini, and Priya Vithani. In addition to those mentioned above, we extend our thanks to the following colleagues: Sakshi Bhatnagar, Beatrice Di Caro, Kateryna Gordiychuk, Jamie Mathew John, Gulipairi Maimaiti, Eoin Ó Cathasaigh, Robin Pomeroy, Vesselina Ratcheva, and Katja Rouru. Design and Production: Thank you to all those involved in the design and production of this year’s report: Mike Fisher (editing), Jacopo Poletto (Design), and Beatrice Lattuada (Design). Global Risks Report 2023 97
The World Economic Forum, committed to improving the state of the world, is the International Organization for Public-Private Cooperation. The Forum engages the foremost political, business and other leaders of society to shape global, regional and industry agendas. World Economic Forum 91–93 route de la Capite CH-1223 Cologny/Geneva Switzerland Tel.: +41 (0) 22 869 1212 Fax: +41 (0) 22 786 2744 [email protected] www.weforum.org